A company has a model-driven app. The app has forms with both Business Rules and JavaScript added to handle the business logic on the form.
The form contains logic that is enforced by using business rules. The company wants to apply the business rules to all forms in the app.
You need to recommend a simplified form setup so the form can be maintained moving forward.
What should you recommend?
Answer:
A
PCF controls are reusable.
Reference:
https://docs.microsoft.com/en-us/powerapps/developer/component-framework/overview
A local bank uses Microsoft Power Platform apps to store customer data.
The bank IT director discovers that all employees can see the social security numbers of their customers. The IT team does not understand how field-level security works and needs help with the design.
You need to recommend a solution to the bank that meets the following requirements:
✑ The system must restrict access to customer social security numbers to the vice president of finance only.
✑ The vice president of finance must be able to read and update customer social security numbers.
Which two actions should you recommend? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
Answer:
CD
Field-level security is managed by the security profiles. To implement field-level security, a system administrator performs the following tasks.
1. Enable field security on one or more fields for a given entity.
2. Associate one more existing security profiles, or create one or more new security profiles to grant the appropriate access to specific users or teams.
Reference:
https://docs.microsoft.com/en-us/power-platform/admin/field-level-security
HOTSPOT -
You are designing a Microsoft Power Platform solution for a national repair service. The service has a 24-hour call center for customers to call and schedule repairs.
The solution dispatches a technician to troubleshoot and repair customer issues. Customers sign into a customer portal to view and log information concerning the repairs. The repair service contracts with third party technicians for repair jobs.
The solution must meet the following requirements:
✑ Dispatch technicians to troubleshoot and repair customer issues.
✑ Call center must log customer issues.
✑ Third-party technicians must be able to access assigned repair service jobs.
You need to recommend an authentication strategy.
Which authentication models should you use? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area: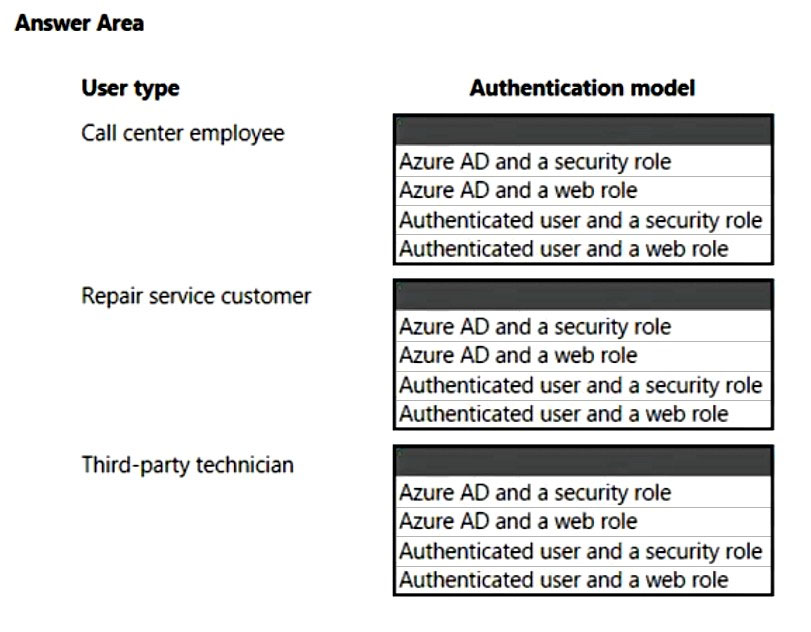
Answer:
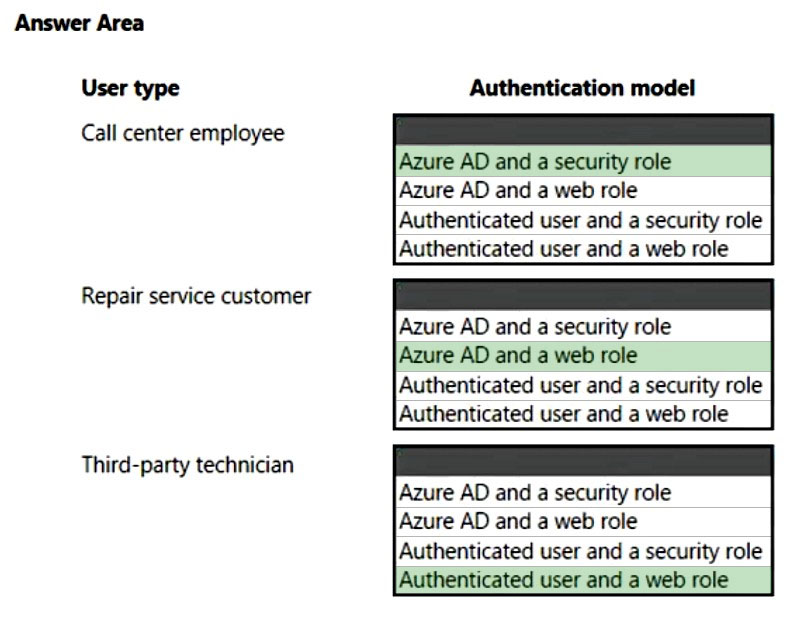
Box 1: Azure AD and a security role.
Call center must log customer issues.
Box 2: Azure AD and a web role.
Dispatch technicians to troubleshoot and repair customer issues.
Box 3: Authenticated user and a web role
Third-party technicians must be able to access assigned repair service jobs.
Before you grant authenticated users access to table permissions or restricted pages, they must first be assigned to a web role.
Authenticated users -
Enabling the Authenticated Users Role makes it the default web role for all users. This role is commonly used to provide a predetermined access for users that aren't associated to any other roles. Keep in mind that users can have multiple web roles, but there can only be one Authenticated Users web role for authenticated users.
Reference:
https://docs.microsoft.com/en-us/power-platform/admin/database-security https://docs.microsoft.com/en-us/power-pages/security/create-web-roles
DRAG DROP -
You are designing a data model for a Microsoft Power Platform solution.
The data model must meet the following requirements:
✑ When an account is assigned to a new salesperson, all opportunities that are associated with the account must be assigned to the new salesperson.
✑ When a salesperson assigns a lead to another salesperson, all phone call activities related to the lead must be assigned to the new salesperson.
You need to recommend cascading strategies for the data model.
Which cascading strategy should you recommend? To answer, drag the appropriate cascading strategies to the correct requirements. Each cascading strategy may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.
Select and Place: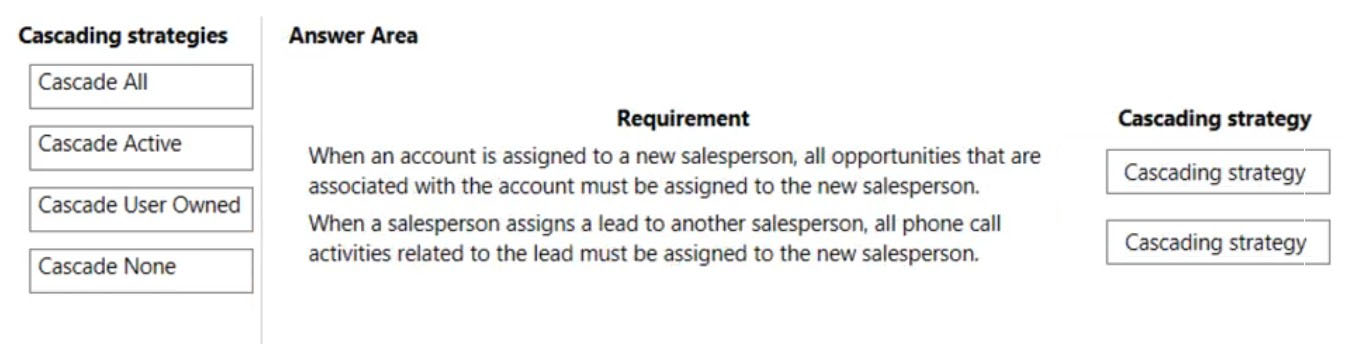
Answer:
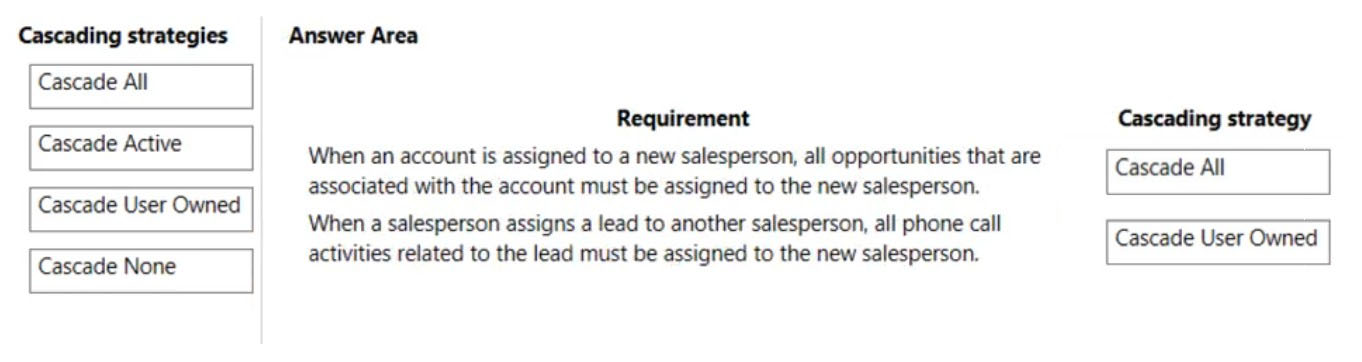
Box 1: Cascade All -
Cascade All - Perform the action on all referencing table records associated with the referenced table record.
Box 2: Cascade User Owned -
Cascade User Owned - Perform the action on all referencing table records owned by the same user as the referenced table record.
Reference:
https://docs.microsoft.com/en-us/power-apps/developer/data-platform/configure-entity-relationship-cascading-behavior
You are a Microsoft Power Platform architect designing a solution.
You must use a custom connector to integrate Power Automate with a data source.
You need to authenticate the connector with the data source.
Which three authentication methods can you use? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.
Answer:
ABD
Authentication types -
The different types of authentication that are currently supported are:
No authentication -
Basic authentication -
Api Key based authentication -
Oauth 2.0 -
Reference:
https://docs.microsoft.com/en-us/connectors/custom-connectors/connection-parameters
HOTSPOT -
You are working with a customer to plan a go-live deployment to their production environment. The solution includes several apps and environment variables. The superuser team manages the production environment that is secured by using a specific environment Azure AD security group.
The following issues have been identified:
✑ The superuser team cannot access make.powerapps.com to open and set the environment variables.
Users are added to the environment Azure AD security group and are not able to access the model-driven app.
✑ Users are added to the environment Azure AD security group and are not able to access the canvas app.
You need to resolve the issues.
What should you do? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area: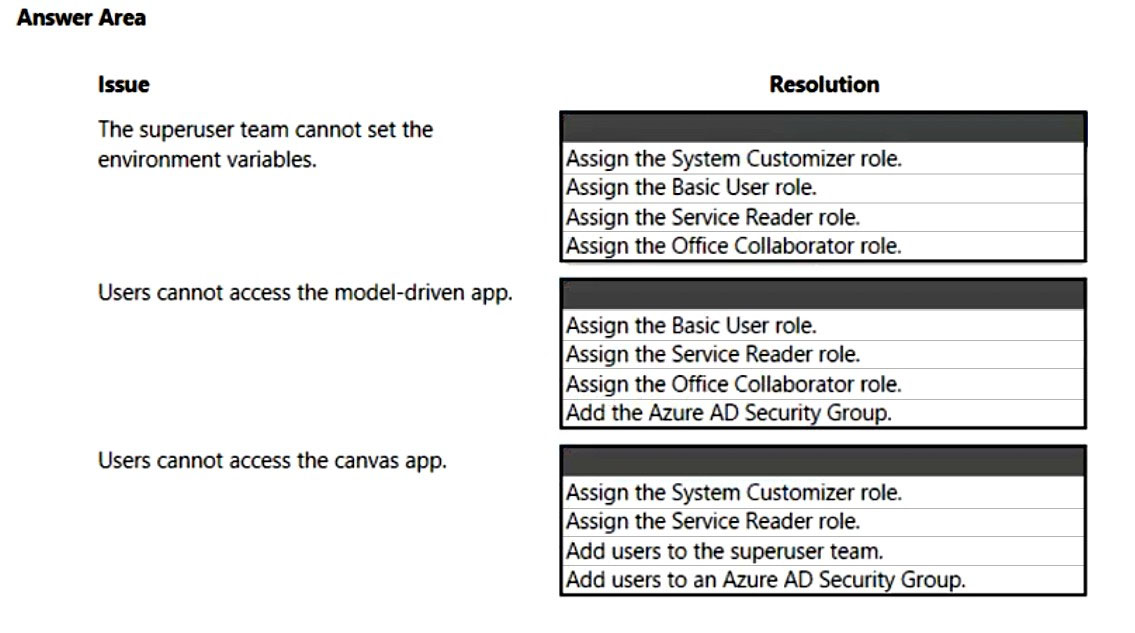
Answer:
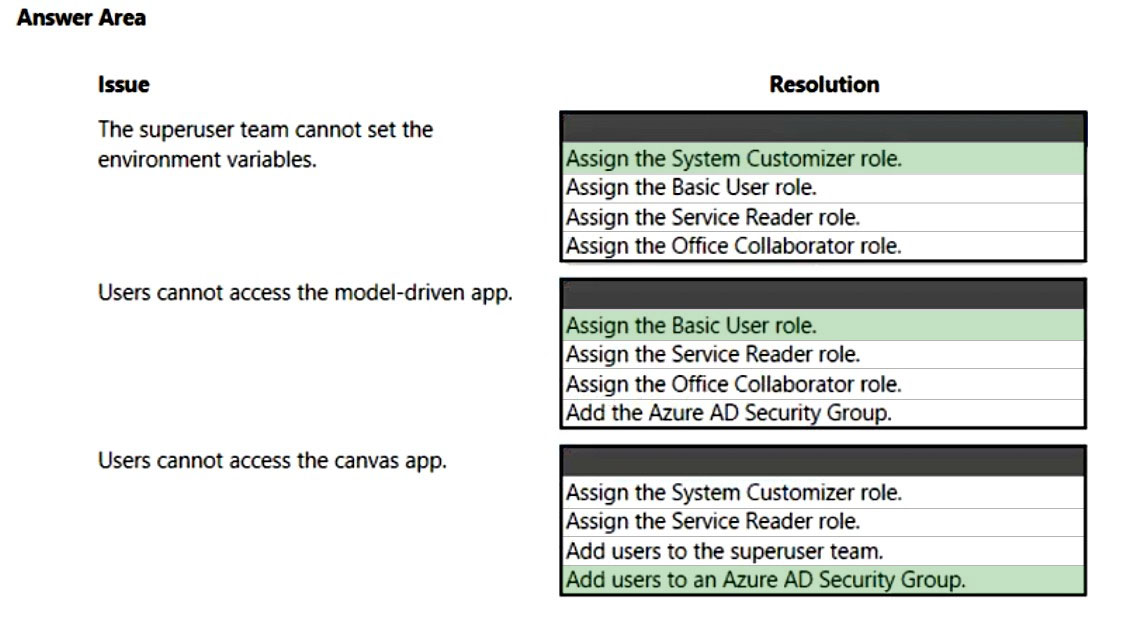
Box 1: System Customizer -
System Customizer - Has full permission to customize the environment. However, users with this role can only view records for environment entities that they create.
Box 2: Assign the Basic User role.
Can run an app within the environment and perform common tasks for the records that they own.
Note: A user's ability to see and use apps is controlled by sharing the application with the user. Sharing of canvas apps is done directly with a user or Azure AD group but is still subject to Dataverse security roles. Sharing of model-driven apps is done via Dataverse security roles.
Box 3: Add users to an Azure AD Security Group.
Sharing of canvas apps is done directly with a user or Azure AD group but is still subject to Dataverse security roles.
Incorrect:
* Office Collaborator role
Has Read permission to tables where a record from these tables was shared with the organization. Does not have access to any other core and custom table records. This role is assigned to the Office Collaborators owner team and not to an individual user.
Reference:
https://docs.microsoft.com/en-us/power-apps/maker/data-platform/environmentvariables https://docs.microsoft.com/en-us/power-platform/admin/wp-security https://docs.microsoft.com/en-us/power-platform/admin/database-security
DRAG DROP -
You are designing a Microsoft Power Platform solution that will be deployed to two separate companies in the same Microsoft Office 365 tenant: Contoso, Ltd. and
Contoso Pharmaceuticals.
The solution must meet the following security requirements:
✑ Restrict Contoso, Ltd. users from seeing the Contoso Pharmaceuticals company.
✑ Restrict access to specific forms.
✑ Restrict access to specific tables.
What should you recommend? To answer, drag the appropriate security types to the correct restrictions. Each security type may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.
Select and Place: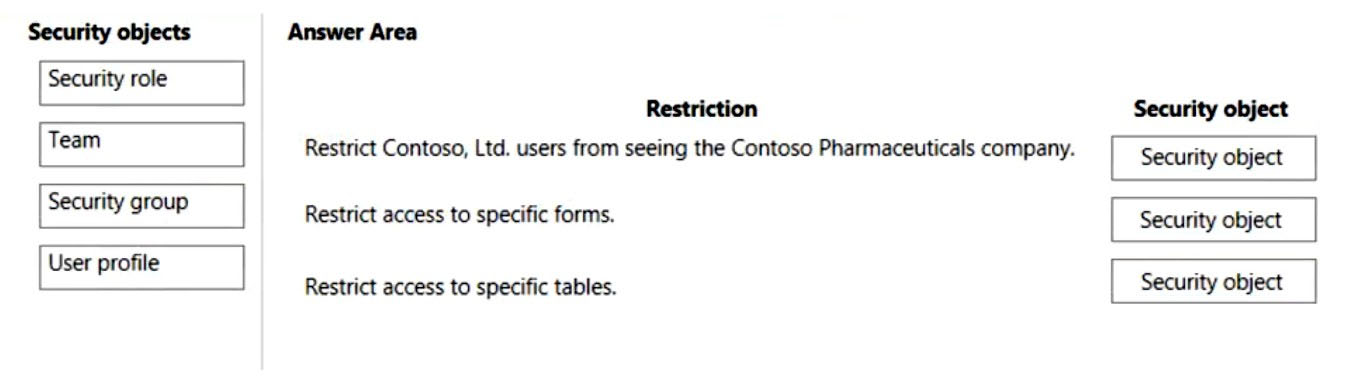
Answer:
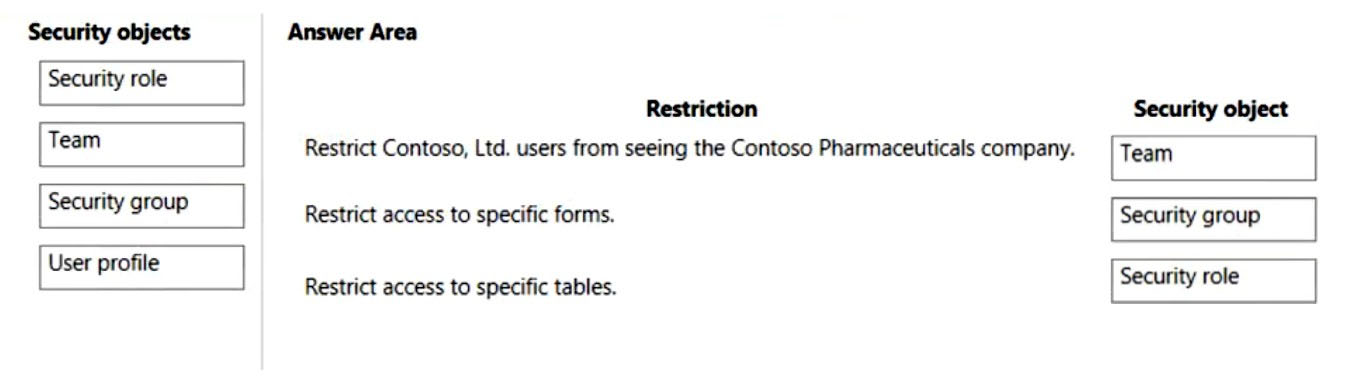
Box 1: Team -
Restrict Contoso, Ltd. users from seeing the Contoso Pharmaceuticals company.
One tenant with two teams.
Box 2: Security group -
Restrict access to specific forms.
For model-driven apps, form-level security allows you to allow only specific security groups to access specific forms. This is useful if you want to restrict how people enter or view data by their job role.
Box 3: Security role -
Restrict access to specific tables.
By default, permissions are applied to components containing data. Making it visible to anyone, or only to specific roles, is done by managing table permissions.
Reference:
https://docs.microsoft.com/en-us/power-apps/maker/portals/add-form https://docs.microsoft.com/en-us/power-apps/guidance/planning/security
A company has a Microsoft Power Platform solution that integrates with a third-party system.
The client reports that unexpected updates are being made to the Accounts table.
You need to determine the root cause of the issue.
In which three locations should you investigate? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.
Answer:
ABD
A: How to View Auditing Log Details?
System administrators can see activities for the entities that are enabled for audit logging. To view the audit logs:
1. Go to Settings > System >Auditing.
2. Choose Audit Summary View.
3. Under Audit Summary View, you will see the list of audit entries
B: You can view details about solution operations from the Solutions area of Power Apps. An operation can be a solution import, export, or uninstall. The solution history displays information such as solution version, solution publisher, type of operation, operation start and end time, and operation status.
D: Trace log records are written to the PluginTraceLog Table. Writing of these records is controlled by the trace settings mentioned in Enable trace logging.
This data can be found in model-driven applications by navigating to Settings and choosing the Plug-in Trace Log tile.
Reference:
https://www.sherweb.com/blog/dynamics-365/audits-dynamics-365/ https://docs.microsoft.com/en-us/powerapps/developer/data-platform/logging-tracing
You are designing a Power Platform solution.
During quality assurance testing the API limits are reached.
You need to identify and resolve the issue.
Which two actions should you recommend? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
Answer:
AC
A: When users exceed their limits, administrators can see this in the admin center (see below). You can do either one of the following:
✑ Adjust the app or flow to use fewer API requests
✑ Purchase the Power Apps and Power Automate capacity add-on for your organization.
C: Home (default) Dashboard.
This is the default dashboard that provides information on the number of active Dataverse users, storage usage, the most active workflows, and more.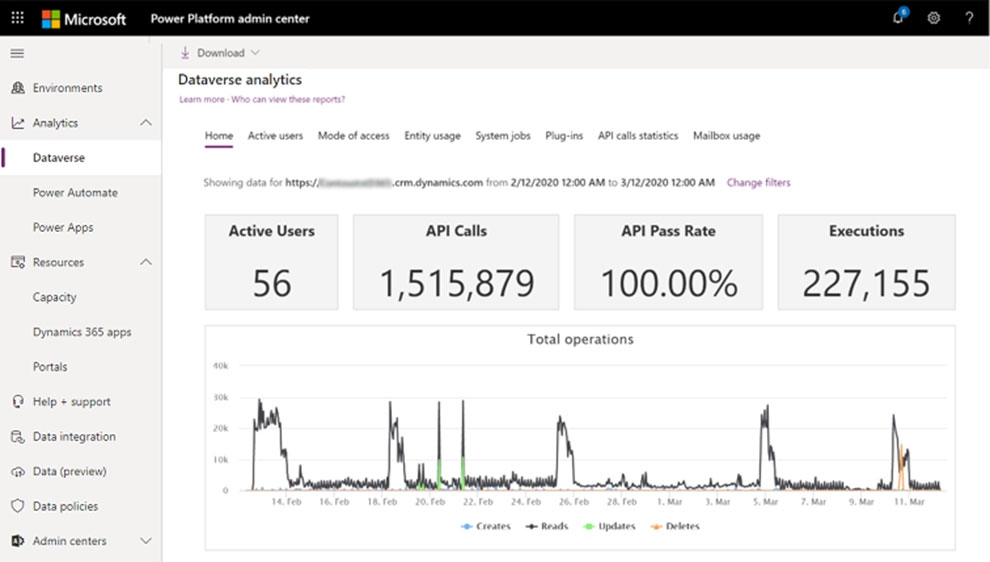
API Calls: API Calls Number of API calls that were made by the Dataverse environment for the selected time period.
Reference:
https://docs.microsoft.com/en-us/power-platform/admin/api-request-limits-allocations https://docs.microsoft.com/en-us/power-platform/admin/analytics-common-data-service
HOTSPOT -
You design a Power Platform solution for a customer. The solution uses Microsoft Dataverse as the data store. You are managing the go-live process for the solution.
The customer reports the following performance issues:
✑ Form load time is much slower than it was during testing.
✑ Overall system performance has been significantly slower that it was during testing.
You need to recommend how to troubleshoot system performance.
Which actions should you recommend? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:
Answer:
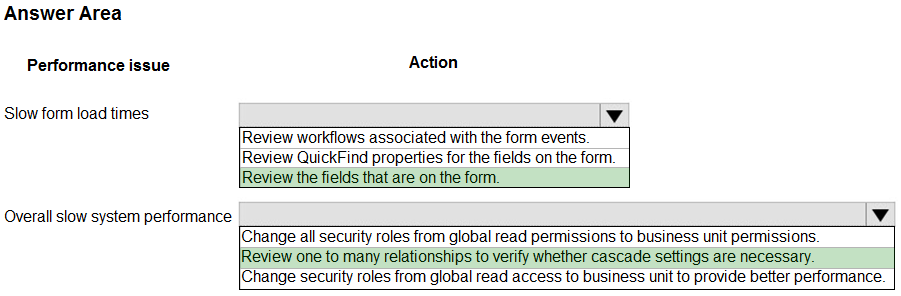
Box 1: Review the fields that are on the form
Keep the number of table columns (fields) to a minimum.
The more table columns (formerly referred to as fields) you have in a form, the more data that needs to be downloaded to view each record.
Box 2: Review one to many relationships to verify whether cascade settings are necessary.
Reference:
https://docs.microsoft.com/en-us/powerapps/maker/model-driven-apps/optimize-form-performance