You are a Microsoft 365 administrator for a company.
You need to identify security vulnerabilities by using the Office 365 Attack Simulator.
Which three attack simulations are available? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.
Answer:
ACE
Reference:
https://docs.microsoft.com/en-us/microsoft-365/security/office-365-security/attack-simulator
DRAG DROP -
A company plans to use Microsoft 365 Defender.
Which services should you use? To answer, drag the appropriate services to the correct requirements. Each service may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.
Select and Place: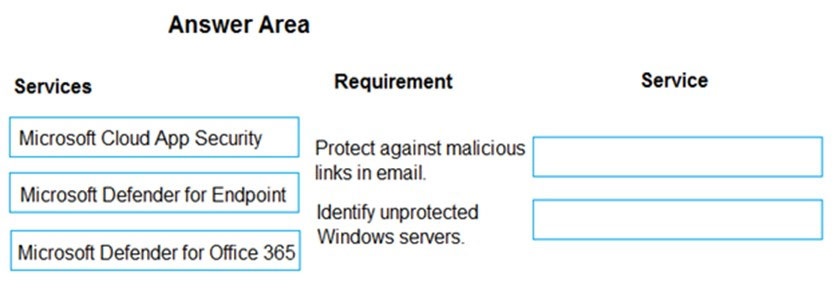
Answer:
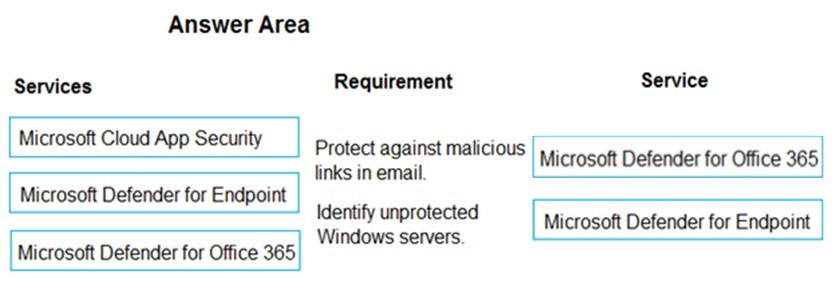
Reference:
https://docs.microsoft.com/en-us/microsoft-365/security/defender/microsoft-365-defender?view=o365-worldwide
HOTSPOT -
Instructions: For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct match is worth one point.
Hot Area: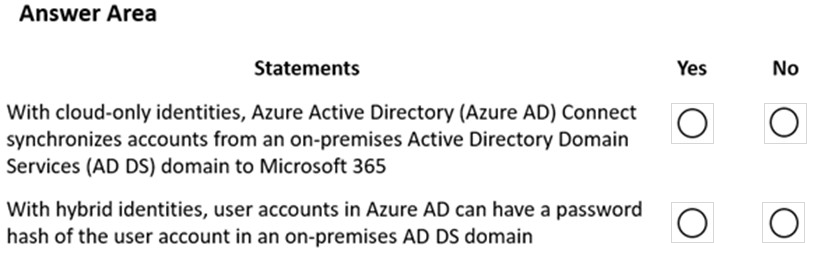
Answer:
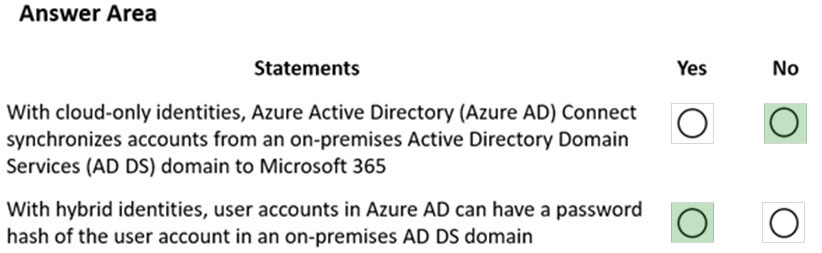
Reference:
https://docs.microsoft.com/en-us/microsoft-365/enterprise/about-microsoft-365-identity?view=o365-worldwide
HOTSPOT -
Instructions: For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct match is worth one point.
Hot Area: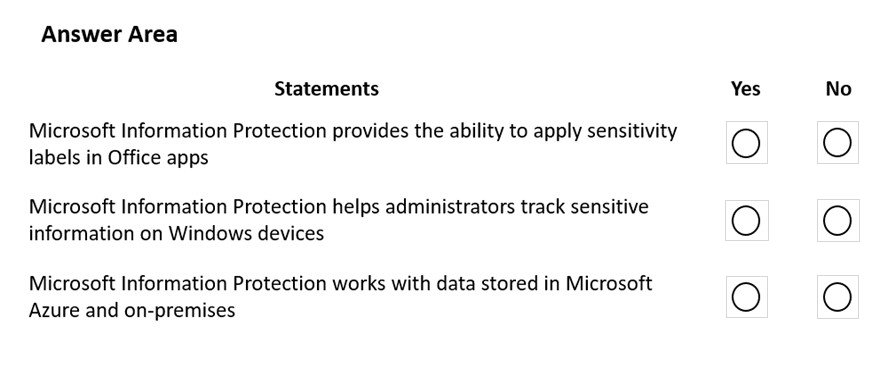
Answer:
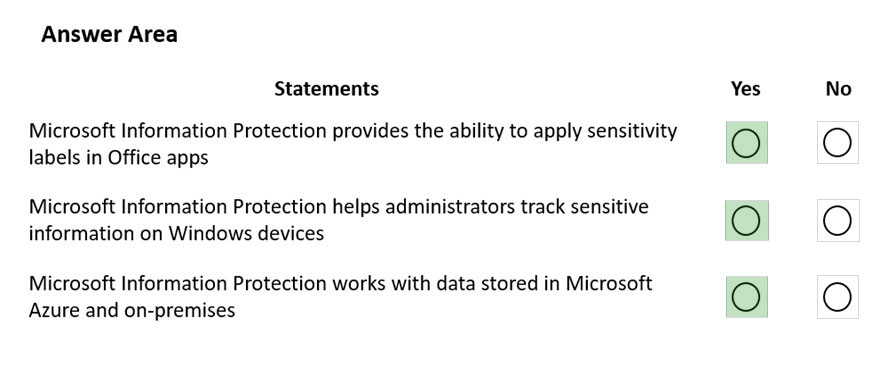
Reference:
https://docs.microsoft.com/en-us/microsoft-365/compliance/information-protection?view=o365-worldwide
HOTSPOT -
A company plans to implement Microsoft Defender for Office 365.
Instructions: For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct match is worth one point.
Hot Area: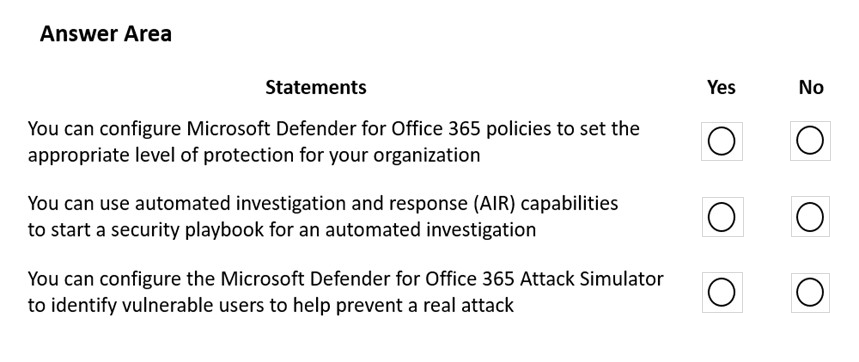
Answer:
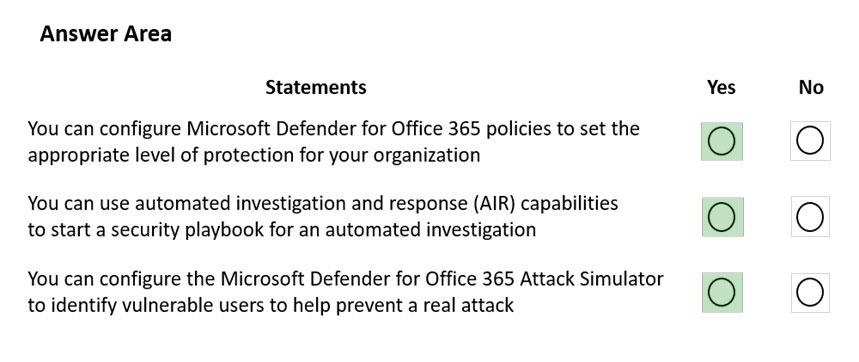
Reference:
https://docs.microsoft.com/en-us/microsoft-365/security/office-365-security/overview?view=o365-worldwide https://docs.microsoft.com/en-us/microsoft-365/security/office-365-security/tenant-wide-setup-for-increased-security?view=o365-worldwide https://docs.microsoft.com/en-us/microsoft-365/security/office-365-security/attack-simulator?view=o365-worldwide
A company plans to implement an insider risk solution in Microsoft 365.
The company needs to implement a solution that meets the following requirements:
✑ Uses machine learning to identify email risks.
✑ Provides workflows to remediate email risks.
✑ Provides a dashboard to display email risks, actions, and trends.
You need to identify a solution that meets the requirements.
Which solution should you select?
Answer:
A
Reference:
https://docs.microsoft.com/en-us/microsoft-365/compliance/communication-compliance?view=o365-worldwide
Your organization plans to deploy Microsoft 365 in a hybrid scenario.
You need to ensure that employees can use a smart card for authentication.
Which hybrid identity solution should you implement?
Answer:
B
Reference:
https://docs.microsoft.com/en-us/azure/security/azure-ad-choose-authn
HOTSPOT -
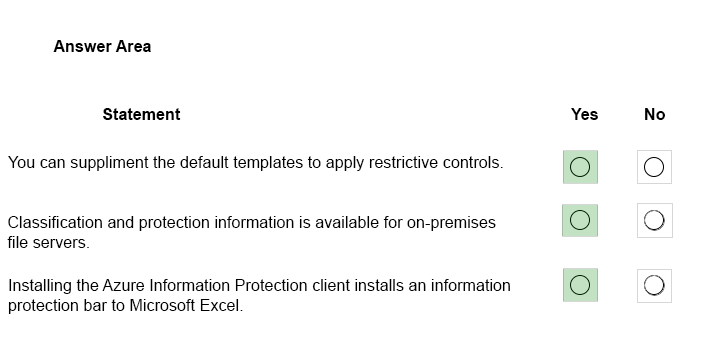
You implement Microsoft Azure Information Protection.
For each of the following statements, select Yes if the statement is true. otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area: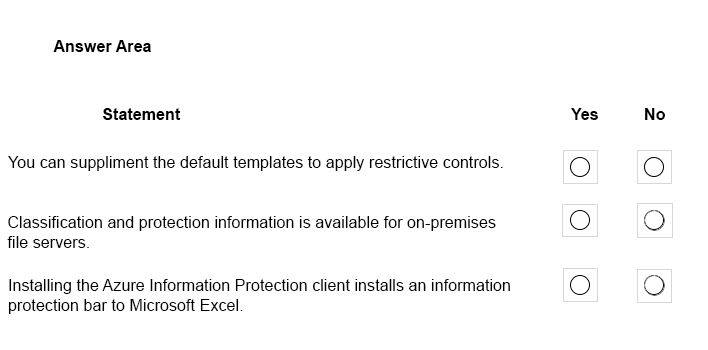
Answer:
Reference:
https://docs.microsoft.com/en-us/azure/information-protection/what-is-information-protection https://docs.microsoft.com/en-us/azure/information-protection/rms-client/client-classify-protect
You need to ensure that the process by which users sign in to Microsoft 365 confirms the identity of the user.
Which feature should you use?
Answer:
C
Multi-Factor Authentication (MFA) is a two-step identity verification system that can be used to authenticate users.
Reference:
https://docs.microsoft.com/en-us/azure/active-directory/authentication/concept-mfa-howitworks
You are a Microsoft 365 administrator for a company.
You need to ensure that company documents are marked as confidential. You must prevent employees from sharing documents with people outside the company.
What are two possible ways to achieve the goal? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.
Answer:
BE
B: Sensitive information types can also be used with the Azure Information Protection scanner to classify and protect files on premises. Sensitive information types define how the automated process recognizes specific information types such as health service numbers and credit card numbers.
E: With sensitivity labels you can classify and help protect your sensitive content. Protection options include labels, watermarks, and encryption.
Reference:
https://docs.microsoft.com/en-us/microsoft-365/compliance/protect-information