DRAG DROP -
A company uses Microsoft 365.
You need to identify the appropriate report for each definition.
Which report should you choose for each definition? To answer, drag the appropriate reports to the correct definitions. Each report may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.
Select and Place: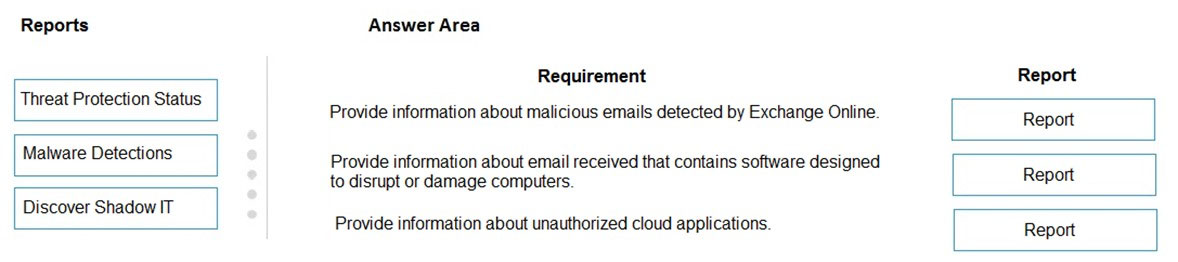
Answer:
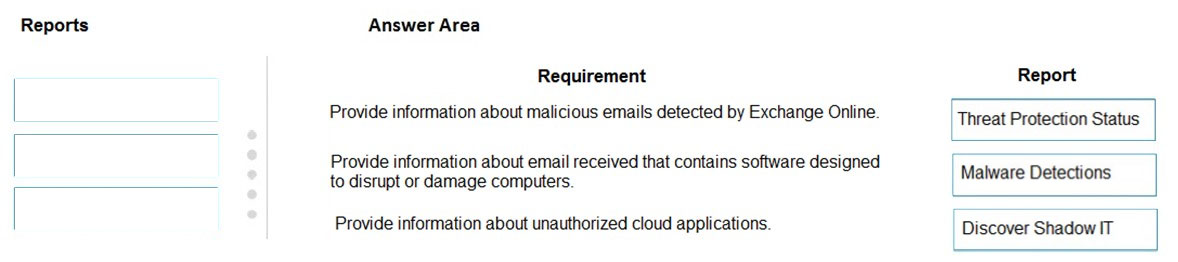
Reference:
https://docs.microsoft.com/en-us/cloud-app-security/tutorial-shadow-it
A company deploys Microsoft Azure AD. You run the Identity Secure Score report. The report displays five security items.
Which three security items on the report have the most impact on the score? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.
Answer:
ABC
Reference:
https://docs.microsoft.com/en-us/microsoft-365/security/defender/microsoft-secure-score?view=o365-worldwide
A company deploys Microsoft Azure AD. You enable multi-factor authentication.
You need to inform users about the multi-factor authentication methods that they can use.
Which of the following methods is NOT a valid multi-factor authentication method in Microsoft 365?
Answer:
D
You deploy Enterprise Mobility + Security E5 and assign Microsoft 365 licenses to all employees.
Employees must not be able to share documents or forward emails that contain sensitive information outside the company.
You need to enforce the file sharing restrictions.
What should you do?
Answer:
A
HOTSPOT -
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth pone point.
Hot Area: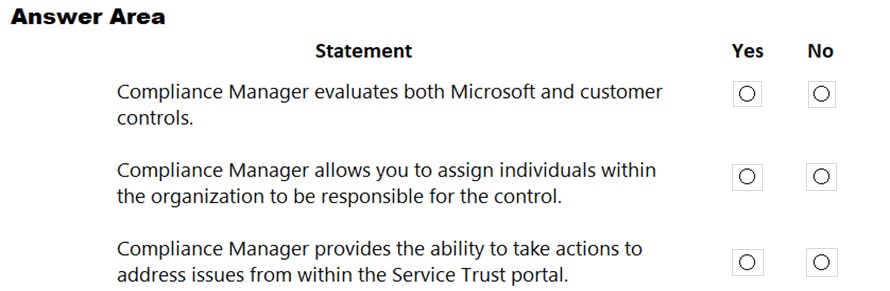
Answer:
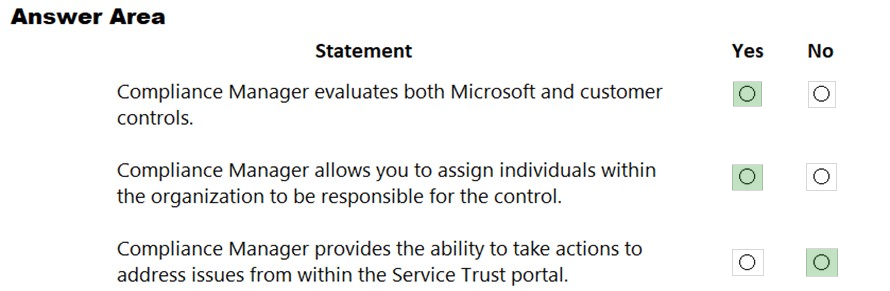
Reference:
https://docs.microsoft.com/en-us/office365/securitycompliance/compliance-manager-overview#controls https://docs.microsoft.com/en-us/office365/securitycompliance/meet-data-protection-and-regulatory-reqs-using-microsoft-cloud https://docs.microsoft.com/en-us/office365/securitycompliance/get-started-with-service-trust-portal
HOTSPOT -
You are a Microsoft 365 administrator for a company. The company implements federated authentication.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area: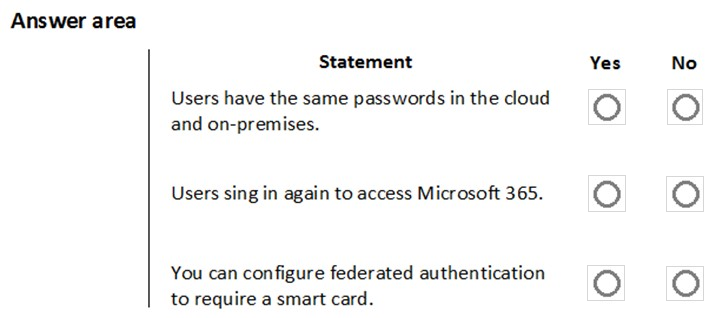
Answer:
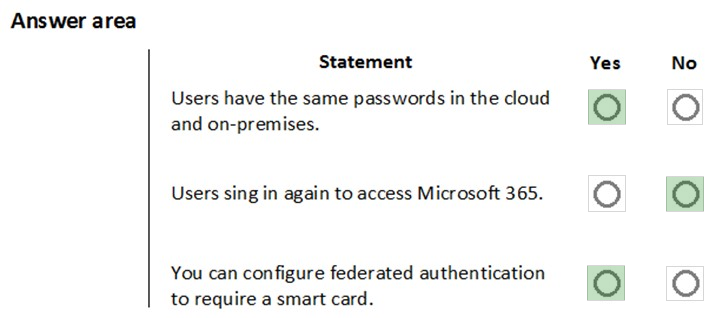
Reference:
https://docs.microsoft.com/en-us/azure/security/fundamentals/choose-ad-authn
DRAG DROP -
A company plans to migrate to a hybrid cloud infrastructure.
You need to determine where to manage the environment after the migration is complete.
Match each item to the location where it will be managed. To answer, drag the appropriate item from the column on the left to its location on the right. Each item may be used once, more than once, or not at all.
NOTE: Each correct selection is worth one point.
Select and Place: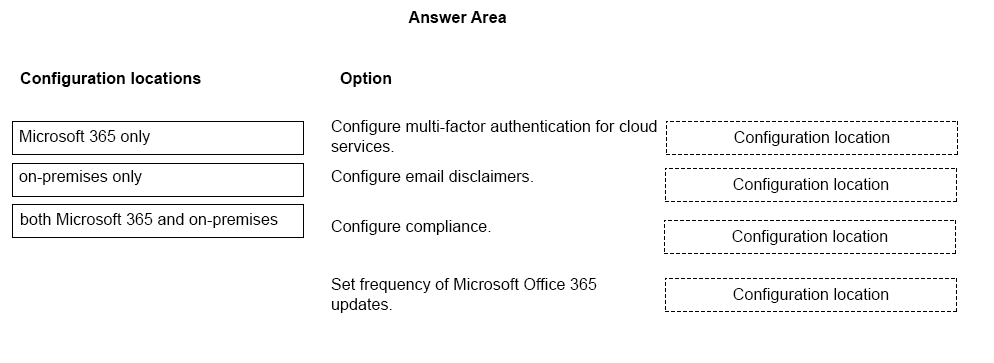
Answer:

Reference:
https://docs.microsoft.com/en-us/office365/securitycompliance/go-to-the-securitycompliance-center https://docs.microsoft.com/en-us/exchange/security-and-compliance/mail-flow-rules/disclaimers-signatures-footers-or-headers https://www.itprotoday.com/email-and-calendaring/configure-email-disclaimer-exchange-server-2016 https://docs.microsoft.com/en-us/office365/troubleshoot/administration/switch-channel-for-office-365
A company deploys Microsoft 365.
The company needs to deploy a solution that meets the following requirements:
✑ allows access to Microsoft 365 only from corporate networks
✑ allows access to Microsoft 365 only from corporate-owned devices
✑ requires additional verification during authentication
You need to identify a solution that meets the requirements.
What should you select?
Answer:
B
Reference:
https://docs.microsoft.com/en-us/azure/active-directory/conditional-access/overview
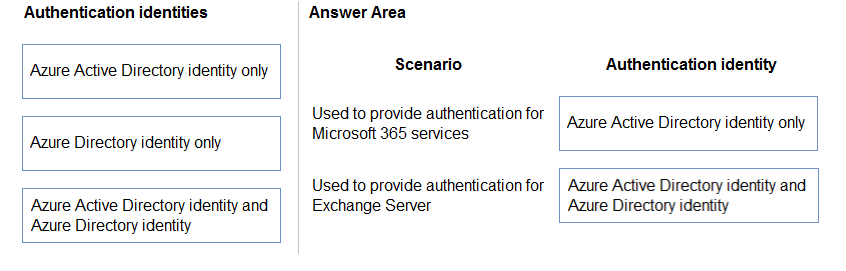
DRAG DROP -
Match each authentication identity to its scenario. To answer, drag the appropriate authentication identity from the column on the left to its scenario on the right.
Each authentication identity may be used once, more than once, or not at all.
NOTE: Each correct match is worth one point.
Select and Place: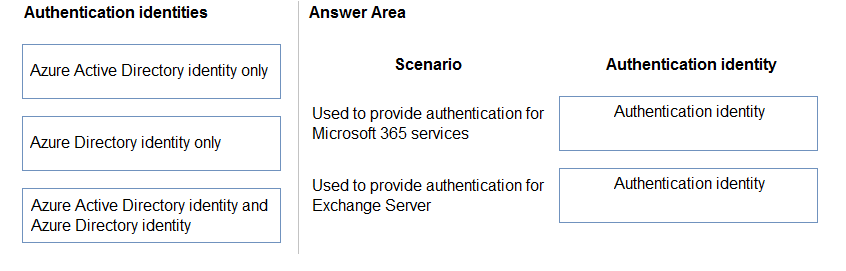
Answer:
Reference:
https://docs.microsoft.com/en-us/microsoft-365/enterprise/about-microsoft-365-identity https://mikeparker365.co.uk/2018/09/19/how-to-secure-exchange-2016-with-azure-ad-part-2-hybrid-modern-authentication/
After experiencing security breaches with on-premises servers, a company is considering migrating to Microsoft 365 for their security solutions.
What are three security-related benefits of moving to Microsoft 365? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.
Answer:
ACD