Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a Microsoft 365 E5 subscription that contains a user named User1.
You need to enable User1 to create Compliance Manager assessments.
Solution: From the Microsoft 365 compliance center, you add User1 to the Compliance Manager Assessors role group.
Does this meet the goal?
Answer:
A
Reference:
https://github.com/MicrosoftDocs/microsoft-365-docs/blob/public/microsoft-365/security/office-365-security/permissions-in-the-security-and-compliance-center.md
HOTSPOT -
You have a Microsoft 365 E5 subscription.
You configure a new alert policy as shown in the following exhibit.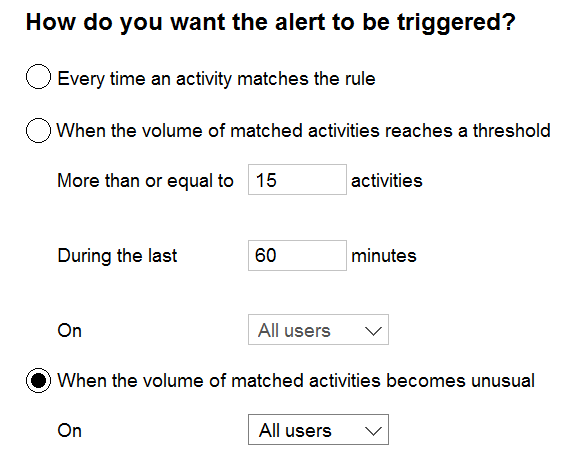
You need to identify the following:
✑ How many days it will take to establish a baseline for unusual activity.
✑ Whether alerts will be triggered during the establishment of the baseline.
What should you identify? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area: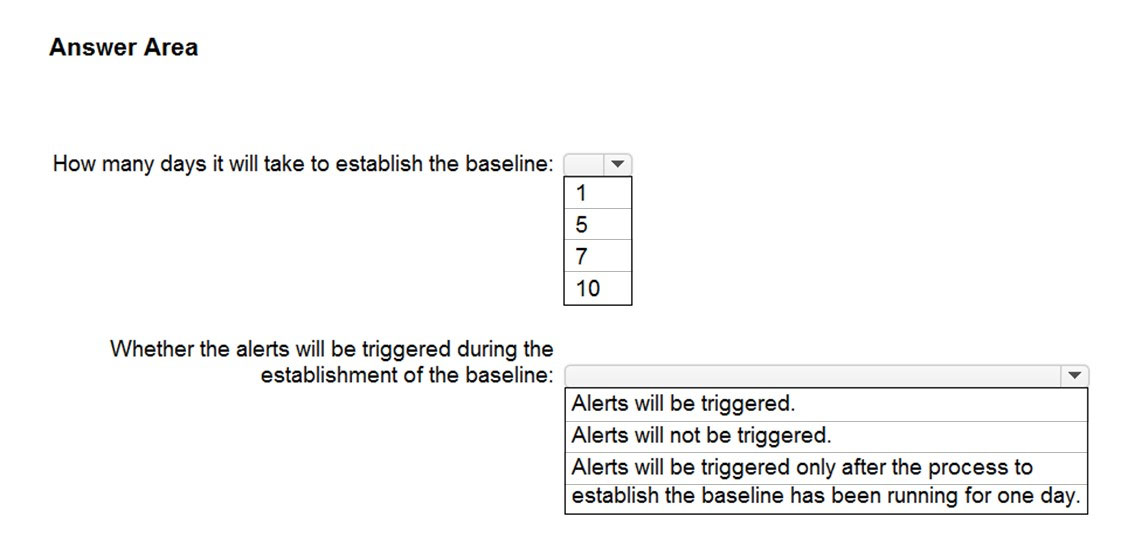
Answer:
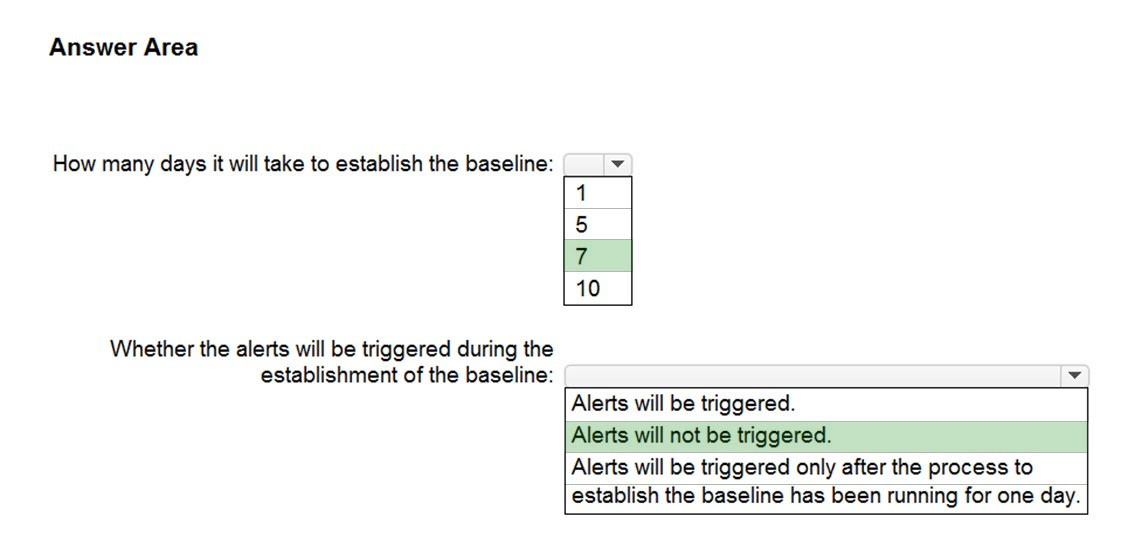
Reference:
https://docs.microsoft.com/en-us/microsoft-365/compliance/alert-policies?view=o365-worldwide
You have a Microsoft 365 E5 subscription that contains the devices shown in the following table.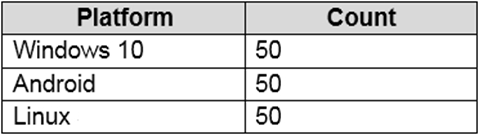
You need to configure an incident email notification rule that will be triggered when an alert occurs only on a Windows 10 device. The solution must minimize administrative effort.
What should you do first?
Answer:
B
Reference:
https://docs.microsoft.com/en-us/microsoft-365/security/defender-endpoint/machine-groups?view=o365-worldwide https://docs.microsoft.com/en-us/microsoft-365/security/defender-endpoint/configure-email-notifications?view=o365-worldwide
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a Microsoft 365 E5 subscription.
You create an account for a new security administrator named SecAdmin1.
You need to ensure that SecAdmin1 can manage Microsoft Defender for Office 365 settings and policies for Microsoft Teams, SharePoint, and OneDrive.
Solution: From the Microsoft 365 admin center, you assign SecAdmin1 the Exchange admin role.
Does this meet the goal?
Answer:
B
You need to assign the Security Administrator role.
Reference:
https://docs.microsoft.com/en-us/microsoft-365/security/office-365-security/office-365-atp?view=o365-worldwide
You have a Microsoft 365 tenant.
You plan to implement Endpoint Protection device configuration profiles.
Which platform can you manage by using the profiles?
Answer:
A
Create a device profile containing Endpoint protection settings
1. Sign in to the Microsoft Endpoint Manager admin center.
2. Select Devices > Configuration profiles > Create profile.
3. Enter the following properties:
4. Platform: Choose the platform of your devices. Your options: macOS
Windows 10 and later -
Profile: Select Templates > Endpoint protection.
5. Select Create.
6. Etc.
Reference:
https://docs.microsoft.com/en-us/mem/intune/protect/endpoint-protection-configure
HOTSPOT -
You have a Microsoft 365 E5 subscription that contains the devices shown in the following table.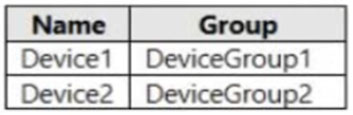
At 08:00, you create an incident notification rule that has the following configurations:
✑ Name: Notification1
✑ Notification settings
- Notify on alert severity: Low
- Device group scope: All (3)
- Details: First notification per incident
✑ Recipients: [email protected], [email protected]
At 08:02, you create an incident notification rule that has the following configurations:
✑ Name: Notification2
✑ Notification settings
- Notify on alert severity: Low, Medium
- Device group scope: DeviceGroup1, DeviceGroup2
✑ Recipients: [email protected]
In Microsoft 365 Defender, alerts are logged as shown in the following table.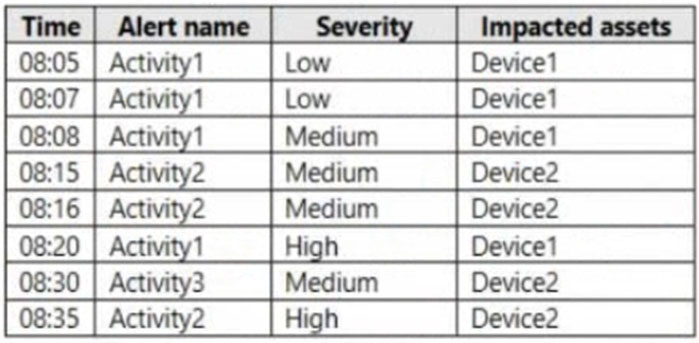
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area: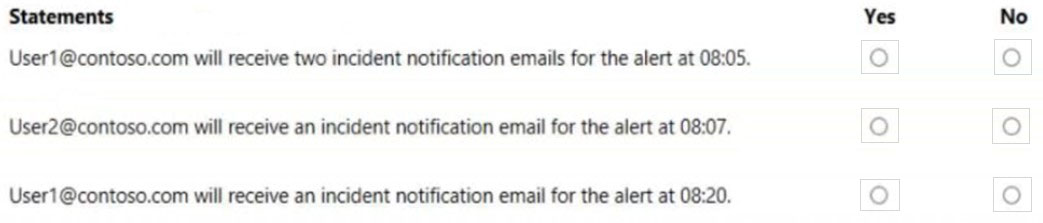
Answer:
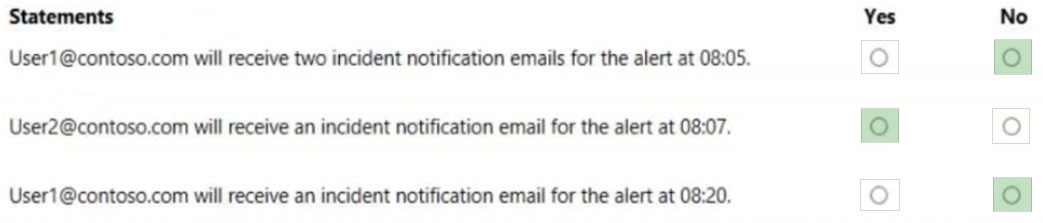
Box 1: No -
Notification it has: First notification per incident
Only notify on first occurrence per incident - Select if you want a notification only on the first alert that matches your other selections. Later updates or alerts related to the incident won't send additional notifications.
Box 2: Yes -
Box 3: No -
Severity of the 8:20 incident is high, so neither of the notification rules will trigger.
Note: Alert severity - Choose the alert severities that will trigger an incident notification. For example, if you only want to be informed about high-severity incidents, select High.
Reference:
https://docs.microsoft.com/en-us/microsoft-365/security/defender/incidents-overview
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a Microsoft 365 subscription.
You discover that some external users accessed content on a Microsoft SharePoint site. You modify the SharePoint sharing policy to prevent sharing outside your organization.
You need to be notified if the SharePoint sharing policy is modified in the future.
Solution: From Microsoft 365 Defender, you create a Threat policy.
Does this meet the goal?
Answer:
B
From the Security & Compliance admin center, Alerts, you create a new alert policy.
Reference:
https://docs.microsoft.com/en-us/microsoft-365/compliance/alert-policies
You have a Microsoft 365 E5 tenant.
You configure sensitivity labels.
Users report that the Sensitivity button is unavailable in Microsoft Word for the web. The Sensitivity button is available in Word for Microsoft 365.
You need to ensure that the users can apply the sensitivity labels when they use Word for the web.
What should you do?
Answer:
C
Sensitivity labels must be published from the Microsoft 365 compliance center or the Security & Compliance Center to be available in Office applications.
Reference:
https://support.microsoft.com/en-us/office/known-issues-with-sensitivity-labels-in-office-b169d687-2bbd-4e21-a440-7da1b2743edc
You have a Microsoft 365 E5 tenant that contains two groups named Group1 and Group2.
You need to prevent the members of Group1 from communicating with the members of Group2 by using Microsoft Teams. The solution must comply with regulatory requirements and must not affect other users in the tenant.
What should you use?
Answer:
B
Microsoft Purview Information Barriers (IBs) are policies that an admin can configure to prevent individuals or groups from communicating with each other.
Reference:
https://docs.microsoft.com/en-us/microsoftteams/information-barriers-in-teams
You have a Microsoft 365 E5 subscription.
You need to identify which users accessed Microsoft Office 365 from anonymous IP addresses during the last seven days.
What should you do?
Answer:
C
The Microsoft Defender for Cloud Apps anomaly detection policies provide out-of-the-box user and entity behavioral analytics (UEBA) and machine learning (ML) so that you're ready from the outset to run advanced threat detection across your cloud environment.
Protection includes: Activity from anonymous IP addresses
Reference:
https://docs.microsoft.com/en-us/defender-cloud-apps/anomaly-detection-policy