Your company has three main offices and one branch office. The branch office is used for research.
The company plans to implement a Microsoft 365 tenant and to deploy multi-factor authentication.
You need to recommend a Microsoft 365 solution to ensure that multi-factor authentication is enforced only for users in the branch office.
What should you include in the recommendation?
Answer:
A
With Azure Active Directory (Azure AD) Conditional Access, you can control how authorized users can access your cloud apps. The location condition of a
Conditional Access policy enables you to tie access controls settings to the network locations of your users.
For this question, we need to configure a location condition in a conditional access policy and apply the policy to users in that location (the branch office). The conditional access policy can be required to 'Allow Access' but 'Required MFA'.
Reference:
https://docs.microsoft.com/en-us/azure/active-directory/conditional-access/location-condition
Your network contains an Active Directory domain named contoso.com.
All users authenticate by using a third-party authentication solution.
You purchase Microsoft 365 and plan to implement several Microsoft 365 services.
You need to recommend an identity strategy that meets the following requirements:
✑ Provides seamless SSO
✑ Minimizes the number of additional servers required to support the solution
✑ Stores the passwords of all the users in Microsoft Azure Active Directory (Azure AD)
✑ Ensures that all the users authenticate to Microsoft 365 by using their on-premises user account
You are evaluating the implementation of federation.
Which two requirements are met by using federation? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.
Answer:
BD
When you choose this federation as the authentication method, Azure AD hands off the authentication process to a separate trusted authentication system, such as on-premises Active Directory Federation Services (AD FS), to validate the user's password. AD FS can use on-premise Active Directory as an authentication provider. AD FS can also provide SSO when using Active Directory as an authentication provider.
Incorrect Answers:
A: Additional servers are required to support the AD FS infrastructure.
C: The passwords are not synchronised to Azure AD.
Reference:
https://docs.microsoft.com/en-us/azure/security/azure-ad-choose-authn
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
Your company plans to deploy several Microsoft Office 365 services.
You need to design an authentication strategy for the planned deployment. The solution must meet the following requirements:
✑ Users must be able to authenticate during business hours only.
✑ Authentication requests must be processed successfully if a single server fails.
✑ When the password for an on-premises user account expires, the new password must be enforced the next time the user signs in.
✑ Users who connect to Office 365 services from domain-joined devices that are connected to the internal network must be signed in automatically.
Solution: You design an authentication strategy that uses federation authentication by using Active Directory Federation Services (AD FS). The solution contains two AD FS servers and two Web Application Proxies.
Does this meet the goal?
Answer:
B
This solution meets the following requirements:
✑ Users must be able to authenticate during business hours only.
✑ Authentication requests must be processed successfully if a single server fails.
✑ When the password for an on-premises user account expires, the new password must be enforced the next time the user signs in.
The following requirement is not met:
✑ Users who connect to Office 365 services from domain-joined devices that are connected to the internal network must be signed in automatically.
To meet this requirement, you would need to configure seamless Single Sign-on (SSO)
Reference:
https://docs.microsoft.com/en-us/azure/security/azure-ad-choose-authn
HOTSPOT -
You have a Microsoft 365 subscription that contains the users shown in the following table.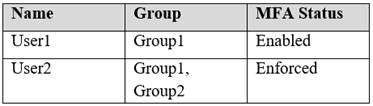
You have the named locations shown in the following table.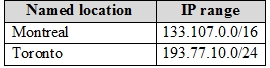
You create a conditional access policy that has the following configurations:
✑ Users and groups:
- Include: Group1
- Exclude: Group2
✑ Cloud apps: Include all cloud apps
✑ Conditions:
- Include: Any location
- Exclude: Montreal
✑ Access control: Grant access, Require multi-factor authentication
User1 is on the multi-factor authentication (MFA) blocked users list.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area:
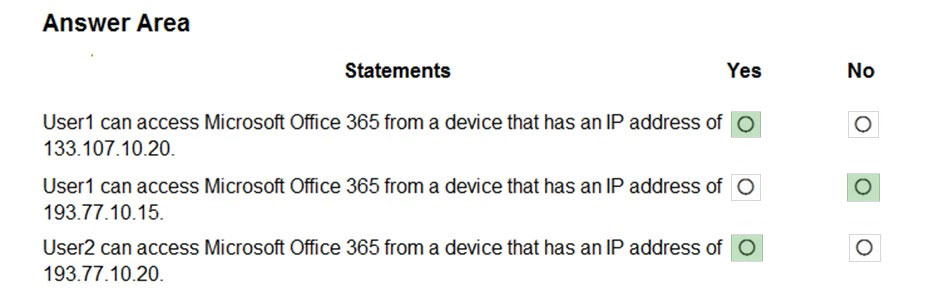
Answer:
The Blocked User list is used to block specific users from being able to receive Multi-Factor Authentication requests. Any authentication attempts for blocked users are automatically denied. Users remain blocked for 90 days from the time that they are blocked.
Box 1: Yes -
133.107.10.20 is in the Montreal named location. The conditional access policy excludes Montreal so the policy does not apply. Therefore, User1 can access
Microsoft Office 365.
Box 2: No -
193.77.10.15 is in the Toronto named location. The conditional access policy applies to Group1 which User1 is a member of and all locations except for Montreal.
Therefore, the conditional access policy applies in this case. The policy requires MFA but User1 is on the MFA blocked list so he is unable to use MFA.
Therefore, User1 cannot access Microsoft 365.
Box 3: Yes -
User2 is in Group1 and Group2. The conditional access policy applies to Group1 but excludes Group2. Therefore, the conditional access policy does not apply in this case so User2 can access Microsoft Office 365.
Reference:
https://docs.microsoft.com/en-us/azure/active-directory/authentication/howto-mfa-mfasettings
Your network contains an Active Directory domain named contoso.com. The domain contains five domain controllers.
You purchase Microsoft 365 and plan to implement several Microsoft 365 services.
You need to identify an authentication strategy for the planned Microsoft 365 deployment. The solution must meet the following requirements:
✑ Ensure that users can access Microsoft 365 by using their on-premises credentials.
✑ Use the existing server infrastructure only.
✑ Store all user passwords on-premises only.
✑ Be highly available.
Which authentication strategy should you identify?
Answer:
A
Azure AD Pass-through Authentication. Provides a simple password validation for Azure AD authentication services by using a software agent that runs on one or more on-premises servers. The servers validate the users directly with your on-premises Active Directory, which ensures that the password validation doesn't happen in the cloud.
Incorrect Answers:
B: Password hash synchronization replicates passwords to Azure Active Directory. This does not meet the following requirement: Store all user passwords on- premises only
C: Password hash synchronization replicates passwords to Azure Active Directory. This does not meet the following requirement: Store all user passwords on- premises only
D: Federation requires additional servers running Active Directory Federation Services. This does not meet the following requirement: Use the existing server infrastructure only.
Reference:
https://docs.microsoft.com/en-us/azure/security/fundamentals/choose-ad-authn
Your network contains an on-premises Active Directory domain.
You have a Microsoft 365 subscription.
You implement a directory synchronization solution that uses pass-through authentication.
You configure Microsoft Azure Active Directory (Azure AD) smart lockout as shown in the following exhibit.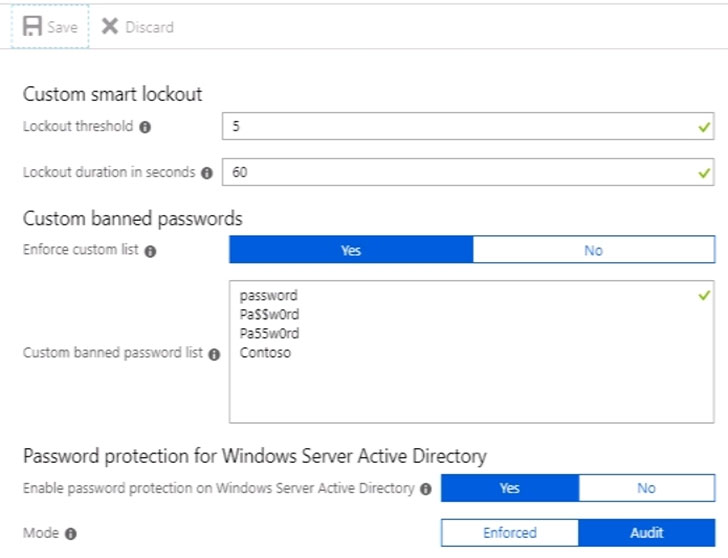
You discover that Active Directory users can use the passwords in the custom banned passwords list.
You need to ensure that banned passwords are effective for all users.
Which three actions should you perform? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
Answer:
ADE
Azure AD password protection is a feature that enhances password policies in an organization. On-premises deployment of password protection uses both the global and custom banned-password lists that are stored in Azure AD. It does the same checks on-premises as Azure AD does for cloud-based changes. These checks are performed during password changes and password reset scenarios.
You need to install the Azure AD Password Protection Proxy on a domain controller and install the Azure AD Password Protection DC Agent on all domain controllers. When the proxy and agent are installed and configured, Azure AD password protection will work.
In the exhibit, the password protection is configured in Audit mode. This is used for testing. To enforce the configured policy, you need to set the password protection setting to Enforced.
Reference:
https://docs.microsoft.com/en-us/azure/active-directory/authentication/howto-password-ban-bad-on-premises-deploy https://docs.microsoft.com/en-us/azure/active-directory/authentication/concept-password-ban-bad-on-premises
HOTSPOT -
You have a Microsoft Azure Active Directory (Azure AD) tenant named contoso.com that includes a user named User1.
You enable multi-factor authentication for contoso.com and configure the following two fraud alert settings:
✑ Set Allow users to submit fraud alerts: On
✑ Automatically block users who report fraud: On
You need to instruct the users in your organization to use the fraud reporting features correctly.
What should you tell the users to do? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area: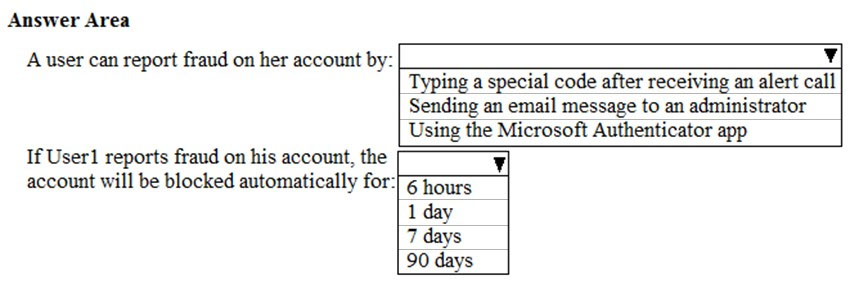
Answer:
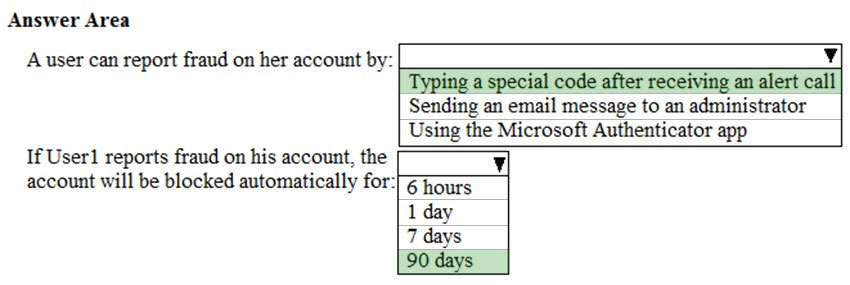
Code to report fraud during initial greeting: When users receive a phone call to perform two-step verification, they normally press # to confirm their sign-in. To report fraud, the user enters a code before pressing #. This code is 0 by default, but you can customize it.
Block user when fraud is reported: If a user reports fraud, their account is blocked for 90 days or until an administrator unblocks their account. An administrator can review sign-ins by using the sign-in report, and take appropriate action to prevent future fraud. An administrator can then unblock the user's account.
Reference:
https://docs.microsoft.com/en-us/azure/active-directory/authentication/howto-mfa-mfasettings#fraud-alert
You have a Microsoft Azure Active Directory (Azure AD) tenant named contoso.onmicrosoft.com.
An external user has a Microsoft account that uses an email address of [email protected]
An administrator named Admin1 attempts to create a user account for the external user and receives the error message shown in the following exhibit.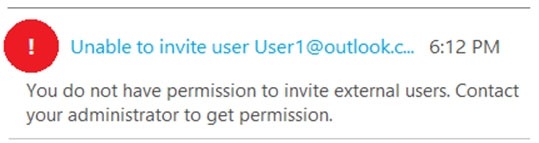
You need to ensure that Admin1 can add the user.
What should you do from the Azure Active Directory admin center?
Answer:
C
In the External Collaboration settings, you can set the following invitation policies:
✑ Turn off invitations
✑ Only admins and users in the Guest Inviter role can invite
✑ Admins, the Guest Inviter role, and members can invite
✑ All users, including guests, can invite
In this question, an Admin user is unable to invite the guest user. This suggests that invitations are turned off altogether.
Reference:
https://docs.microsoft.com/en-us/azure/active-directory/b2b/delegate-invitations
HOTSPOT -
You have a Microsoft 365 Enterprise E5 subscription.
You create a password policy as shown in the following exhibit.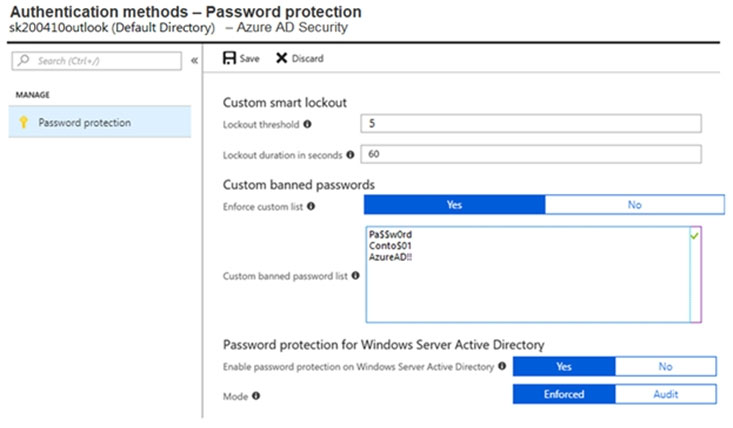
Use the drop-down menus to select the answer choice that completes each statement based on the information presented in the graphic.
NOTE: Each correct selection is worth one point.
Hot Area: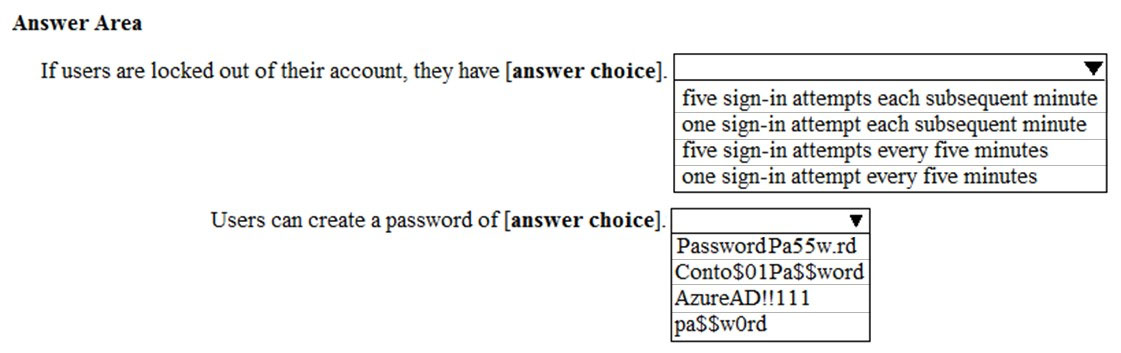
Answer:
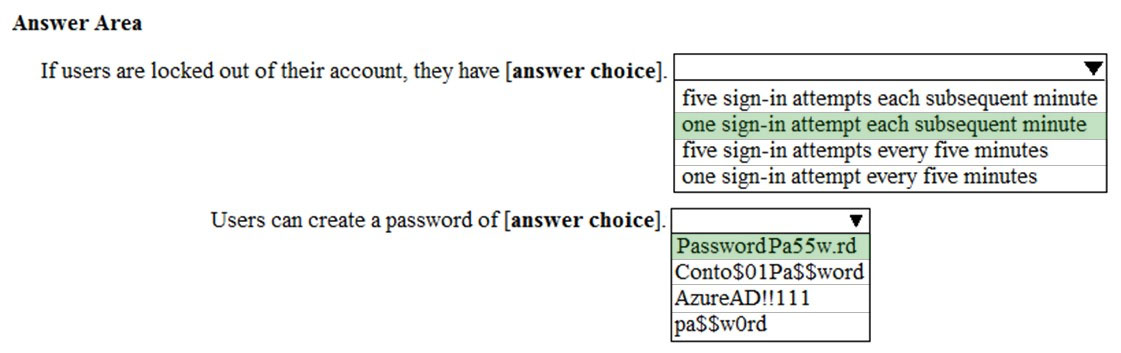
By default, smart lockout locks the account from sign-in attempts for one minute after 10 failed attempts. In this question, the lockout threshold if 5 failed attempts.
The account locks again after each subsequent failed sign-in attempt, for one minute at first and longer in subsequent attempts.
Password evaluation goes through several steps including normalization and Substring matching which is used on the normalized password to check for the user's first and last name as well as the tenant name.
The next step is to identify all instances of banned passwords in the user's normalized new password. Then:
1. Each banned password that is found in a user's password is given one point.
2. Each remaining unique character is given one point.
3. A password must be at least five (5) points for it to be accepted.
Conto$01Pa$$word contains two banned passwords and no remaining unique characters so is given a score of 2 points. This is less than the required 5 points so will be rejected.
Pa$$w0rd contains a banned password and no remaining unique characters so is given a score of 1 point. This is less than the required 5 points so will be rejected.
AzureAD!!111 contains a banned password (AzureAD!!) and has three remaining characters. However, the remaining characters are all the same (they're all 1s) so that is only one unique character. So that password will be given a score of 2. One for the banned password and 1 for the unique character. This is less than the required 5 points so will be rejected.
PasswordPa55w.rd does not contain a banned password. PasswordPa55w.rd contains 16 characters. However, there are two 'P', two 'a', two 's', two 'w', two 'r', two 'd', and two '5' so there are 9 unique characters. Therefore, the password will be given a score of 9 points. This is more than the required 5 points so the password will be accepted.
Reference:
https://docs.microsoft.com/en-us/azure/active-directory/authentication/concept-password-ban-bad https://docs.microsoft.com/en-us/azure/active-directory/authentication/howto-password-smart-lockout
SIMULATION -
Please wait while the virtual machine loads. Once loaded, you may proceed to the lab section. This may take a few minutes, and the wait time will not be deducted from your overall test time.
When the Next button is available, click it to access the lab section. In this section, you will perform a set of tasks in a live environment. While most functionality will be available to you as it would be in a live environment, some functionality (e.g., copy and paste, ability to navigate to external websites) will not be possible by design.
Scoring is based on the outcome of performing the tasks stated in the lab. In other words, it doesn't matter how you accomplish the task, if you successfully perform it, you will earn credit for that task.
Labs are not timed separately, and this exam may have more than one lab that you must complete. You can use as much time as you would like to complete each lab. But, you should manage your time appropriately to ensure that you are able to complete the lab(s) and all other sections of the exam in the time provided.
Please note that once you submit your work by clicking the Next button within a lab, you will NOT be able to return to the lab.
You may now click next to proceed to the lab.
Lab information -
Use the following login credentials as needed:
To enter your username, place your cursor in the Sign in box and click on the username below.
To enter your password, place your cursor in the Enter password box and click on the password below.
Microsoft 365 Username: [email protected]
Microsoft 365 Password: xxxxxxxxxx
If the Microsoft 365 portal does not load successfully in the browser, press CTRL-K to reload the portal in a new browser tab.
The following information is for technical support purposes only:
Lab Instance: 111111111 -
You need to ensure that when Lynne Robbins attempts to sign in to the Microsoft Office 365 portal, Lynne Robbins is prompted to authenticate by using multiple methods.
To answer, sign in to the Microsoft 365 portal.
Answer:
See explanation below.
You need to enable Multi-Factor Authentication for Lynne Robbins.
1. Sign in to the Microsoft 365 Admin Center.
2. In the left navigation pane, expand the Users section and select Active Users.
3. Click the 'Multi-factor authentication' link.
4. Select Lynne Robbins.
5. In the right navigation pane, select the 'Enable' link to enable MFA for the account.
6. Confirm the setting by clicking the 'Enable multi-factor authentication' button.
7. Click the Close button to close the confirmation window.