You have a hybrid deployment of Microsoft 365 that contains the users shown the following table.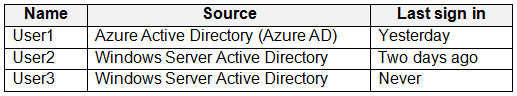
Azure AD Connect has the following settings:
✑ Password Hash Sync: Enabled
✑ Pass-through authentication: Enabled
You need to identify which users will be able to authenticate by using Azure AD if connectivity between on-premises Active Directory and the internet is lost.
Which users should you identify?
Answer:
D
Reference:
https://docs.microsoft.com/en-us/azure/active-directory/hybrid/choose-ad-authn
HOTSPOT -
You have a Microsoft 365 subscription that contains a guest user named User1. User1 is assigned the User administrator role.
You have a Microsoft Azure Active Directory (Azure AD) tenant named contoso.com. Contoso.com is configured as shown in the following exhibit.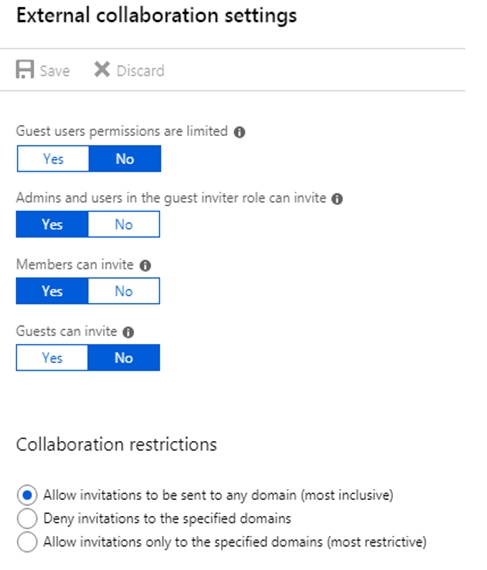
Use the drop-down menus to select the answer choice that completes each statement based on the information presented in the graphic.
NOTE: Each correct selection is worth one point.
Hot Area: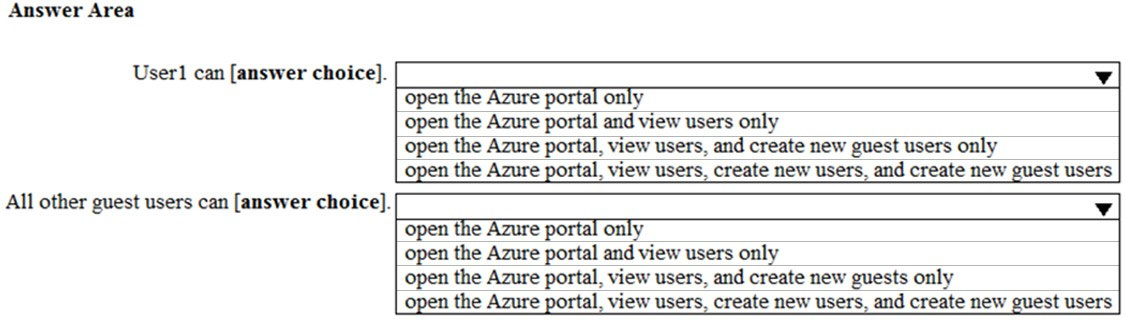
Answer:
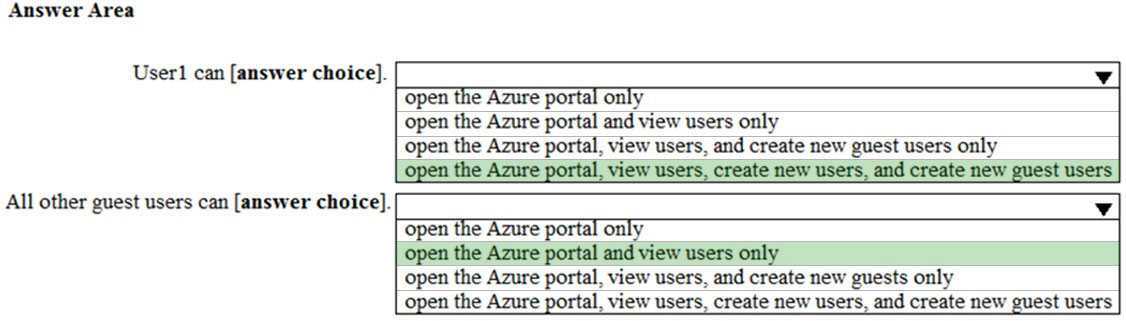
Default permissions for guests are restrictive by default. Guests can be added to administrator roles, which grant them full read and write permissions contained in the role. There is one additional restriction available, the ability for guests to invite other guests. Setting Guests can invite to No prevents guests from inviting other guests.
User1 is assigned the User Administrator role. Therefore, User1 can open the Azure portal, view users, create new users, and create new guest users.
In the exhibit, the 'Guest user permissions are limited' is set to no. This means that guest users have the same permissions as members. However, the 'Guests can invite' setting is set to No. Therefore, other guest users (all guest users except User1) can open the Azure portal and view users in the same way as member users can.
Reference:
https://docs.microsoft.com/en-us/azure/active-directory/b2b/delegate-invitations https://docs.microsoft.com/en-us/azure/active-directory/fundamentals/users-default-permissions
You have a Microsoft 365 subscription and a Microsoft Azure Active Directory (Azure AD) tenant named contoso.com.
Contoso.com is configured as shown in the following exhibit.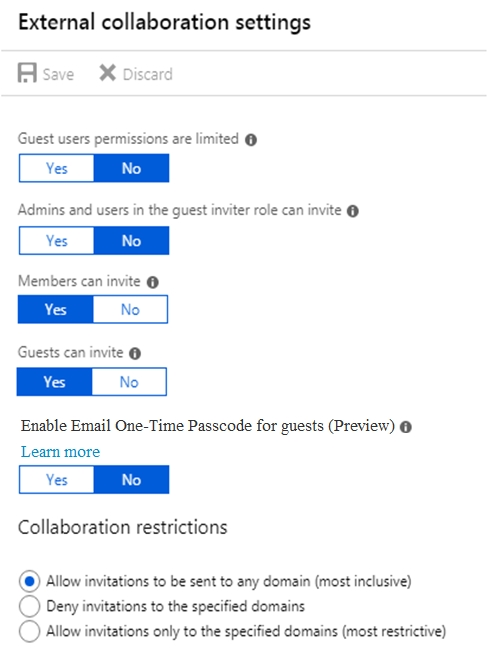
You need to ensure that guest users can be created in the tenant.
Which setting should you modify?
Answer:
D
The setting ג€Admins and users in the guest inviter role can inviteג€ is set to No. This means that no one can create guest accounts because they cannot 'invite' guests. This setting needs to be changed to Yes to ensure that guest users can be created in the tenant.
Reference:
https://docs.microsoft.com/en-us/azure/active-directory/b2b/delegate-invitations https://docs.microsoft.com/en-us/azure/active-directory/fundamentals/users-default-permissions
Your company recently purchased a Microsoft 365 subscription.
You enable Microsoft Azure Multi-Factor Authentication (MFA) for all 500 users in the Azure Active Directory (Azure AD) tenant.
You need to generate a report that lists all the users who completed the Azure MFA registration process.
What is the best approach to achieve the goal? More than one answer choice may achieve the goal. Select the BEST answer.
Answer:
B
You can use the Get-MsolUser cmdlet to generate a report that lists all the users who completed the Azure MFA registration process. The full command would look like this:
Get-MsolUser -All | Where-Object {$_.StrongAuthenticationMethods.Count -eq 0} | Select-Object -Property
UserPrincipalName -
Reference:
https://docs.microsoft.com/en-us/azure/active-directory/authentication/howto-mfa-reporting
You have a Microsoft 365 Enterprise subscription.
You have a conditional access policy to force multi-factor authentication when accessing Microsoft SharePoint from a mobile device.
You need to view which users authenticated by using multi-factor authentication.
What should you do?
Answer:
B
With the sign-ins activity report in the Azure portal, you can get the information you need to determine how your environment is doing.
The sign-ins report can provide you with information about the usage of managed applications and user sign-in activities, which includes information about multi- factor authentication (MFA) usage. The MFA data gives you insights into how MFA is working in your organization. It enables you to answer questions like:
✑ Was the sign-in challenged with MFA?
How did the user complete MFA?
✑ Why was the user unable to complete MFA?
✑ How many users are challenged for MFA?
✑ How many users are unable to complete the MFA challenge?
✑ What are the common MFA issues end users are running into?
Reference:
https://docs.microsoft.com/en-us/azure/active-directory/authentication/howto-mfa-reporting
You have a Microsoft 365 Enterprise E5 subscription.
You need to enforce multi-factor authentication on all cloud-based applications for the users in the finance department.
What should you do?
Answer:
A
You can configure a sign-in risk policy that applies to the Finance department users. The policy can be configured to 'Allow access' but with multi-factor authentication as a requirement.
Note:
There are several versions of this question in the exam. The question has two possible correct answers:
1. Create a sign-in risk policy.
2. Create a conditional access policy.
Other incorrect answer options you may see on the exam include the following:
1. Create an activity policy.
2. Create a session policy.
3. Create an app permission policy.
4. Configure the sign-in status for the user accounts of the finance department users.
5. Assign an Enterprise Mobility + Security E5 license to the finance department users.
Reference:
https://docs.microsoft.com/en-us/azure/active-directory/identity-protection/howto-sign-in-risk-policy
Your network contains an on-premises Active Directory domain named contoso.local. The domain contains five domain controllers.
Your company purchases Microsoft 365 and creates a Microsoft Azure Active Directory (Azure AD) tenant named contoso.onmicrosoft.com.
You plan to install Azure AD connect on a member server and implement pass-through authentication.
You need to prepare the environment for the planned implementation of pass-through authentication.
Which three actions should you perform? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
Answer:
BCF
The on-premise Active Directory domain is named contoso.local. Before you can configure Azure AD Connect, you need to purchase a routable domain, for example, contoso.com.
You then need to add the domain contoso.com to Microsoft as a custom domain name.
The user accounts in the Active Directory domain need to be configured to use the domain name contoso.com as a UPN suffix. You need to add contoso.com to the Active Directory first by using Active Directory Domains and Trusts to add contoso.com add a UPN suffix. You can then configure each account to use the new
UPN suffix.
An Authentication Agent is required on a domain controller to perform the authentication when pass-through authentication is used. When the custom domain and user accounts are configured, you can install and configure Azure AD Connect. An Authentication Agent is installed when you select the pass-through authentication option in the Azure AD Connect configuration or you can install the Authentication Agent manually.
Reference:
https://docs.microsoft.com/en-us/azure/active-directory/hybrid/how-to-connect-pta-quick-start
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
Your company plans to deploy several Microsoft Office 365 services.
You need to design an authentication strategy for the planned deployment. The solution must meet the following requirements:
✑ Users must be able to authenticate during business hours only.
✑ Authentication requests must be processed successfully if a single server fails.
✑ When the password for an on-premises user account expires, the new password must be enforced the next time the user signs in.
✑ Users who connect to Office 365 services from domain-joined devices that are connected to the internal network must be signed in automatically.
Solution: You design an authentication strategy that contains a pass-through authentication model. The solution contains two servers that have an Authentication
Agent installed and password hash synchronization configured.
Does this meet the goal?
Answer:
B
This solution meets the following goals:
✑ Users must be able to authenticate during business hours only.
✑ Authentication requests must be processed successfully if a single server fails.
✑ When the password for an on-premises user account expires, the new password must be enforced the next time the user signs in.
However, the following goal is not met:
Users who connect to Office 365 services from domain-joined devices that are connected to the internal network must be signed in automatically.
You would need to configure Single-sign on (SSO) to meet the last requirement.
Reference:
https://docs.microsoft.com/en-us/azure/active-directory/hybrid/choose-ad-authn
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
Your company plans to deploy several Microsoft Office 365 services.
You need to design an authentication strategy for the planned deployment. The solution must meet the following requirements:
✑ Users must be able to authenticate during business hours only.
✑ Authentication requests must be processed successfully if a single server fails.
✑ When the password for an on-premises user account expires, the new password must be enforced the next time the user signs in.
✑ Users who connect to Office 365 services from domain-joined devices that are connected to the internal network must be signed in automatically.
Solution: You design an authentication strategy that contains a pass-through authentication model. You install an Authentication Agent on three servers and configure seamless SSO.
Does this meet the goal?
Answer:
A
This solution meets all the requirements:
✑ Users must be able to authenticate during business hours only. (This can be configured by using Logon Hours in Active Directory. Pass-through authentication passes authentication to the on-premise Active Directory)
✑ Authentication requests must be processed successfully if a single server fails. (We have Authentication Agents running on three servers)
When the password for an on-premises user account expires, the new password must be enforced the next time the user signs in. (This can be configured in
Active Directory. Pass-through authentication passes authentication to the on-premise Active Directory)
✑ Users who connect to Office 365 services from domain-joined devices that are connected to the internal network must be signed in automatically. (This goal is met by seamless SSO)
Reference:
https://docs.microsoft.com/en-us/azure/active-directory/hybrid/choose-ad-authn
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
Your company plans to deploy several Microsoft Office 365 services.
You need to design an authentication strategy for the planned deployment. The solution must meet the following requirements:
✑ Users must be able to authenticate during business hours only.
✑ Authentication requests must be processed successfully if a single server fails.
✑ When the password for an on-premises user account expires, the new password must be enforced the next time the user signs in.
✑ Users who connect to Office 365 services from domain-joined devices that are connected to the internal network must be signed in automatically.
Solution: You design an authentication strategy that uses password hash synchronization and seamless SSO. The solution contains two servers that have an
Authentication Agent installed.
Does this meet the goal?
Answer:
B
This solution meets the following requirements:
✑ Users who connect to Office 365 services from domain-joined devices that are connected to the internal network must be signed in automatically.
Authentication requests must be processed successfully if a single server fails.
The following requirements are not met:
✑ Users must be able to authenticate during business hours only.
✑ When the password for an on-premises user account expires, the new password must be enforced the next time the user signs in.
To meet these two requirements, you would have to configure pass-through authentication.
Reference:
https://docs.microsoft.com/en-us/azure/active-directory/hybrid/choose-ad-authn