You have an Azure Active Directory group named Group1. Group1 contains two Windows 10 Enterprise devices named Device1 and Device2.
You create a device configuration profile named Profile1. You assign Profile1 to Group1.
You need to ensure that Profile1 applies to Device1 only.
What should you modify in Profile1?
Answer:
D
You create a profile, and it includes all the settings you entered. The next step is to deploy or "assign" the profile to your user or device groups. When it's assigned, the users and devices receive your profile, and the settings you entered are applied.
Reference:
https://docs.microsoft.com/en-us/mem/intune/configuration/device-profile-assign
Your network contains an on-premises Active Directory domain and an Azure Active Directory (Azure AD) tenant.
The Default Domain Policy Group Policy Object (GPO) contains the settings shown in the following table.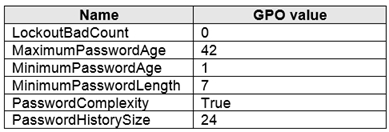
You need to migrate the existing Default Domain Policy GPO settings to a device configuration profile.
Which type of device configuration profile should you create?
Answer:
A
Intune (and other MDM solutions) build there policy configurations and user interfaces on top of CSPs(Configuration Service Providers) . However, some CSPs and its settings might not be exposed in the interface directly but such a setting can be set anyway by entering its OMA-URI manually. Think of an OMA-URI as sort of a registry key that you can set to make the underlying configuration setting happen.
In Intune this is called a Custom Policy.
Example: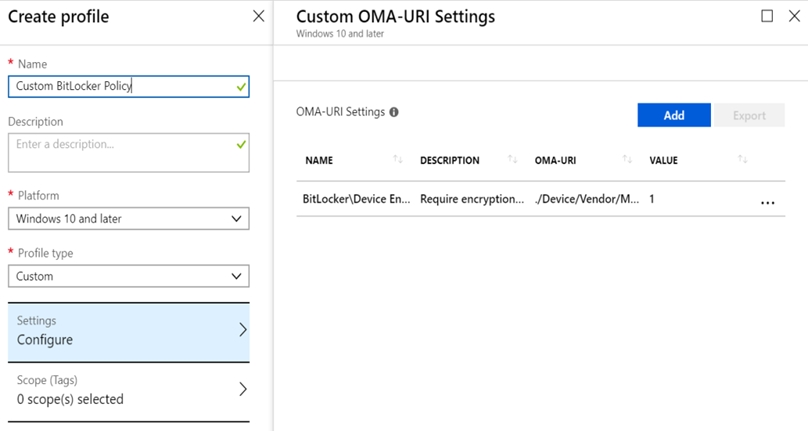
Reference:
https://danielchronlund.com/2018/11/27/how-to-replace-your-old-gpos-with-intune-configuration-profiles/
Your company plans to deploy tablets to 50 meeting rooms.
The tablets run Windows 10 and are managed by using Microsoft Intune. The tablets have an application named App1.
You need to configure the tablets so that any user can use App1 without having to sign in. Users must be prevented from using other applications on the tablets.
Which device configuration profile type should you use?
Answer:
A
Reference:
https://docs.microsoft.com/en-us/windows/configuration/kiosk-single-app
HOTSPOT -
Your network contains an Active Directory domain named contoso.com that syncs to Azure Active Directory (Azure AD). The domain contains computers that run
Windows 10. The computers are configured as shown in the following table.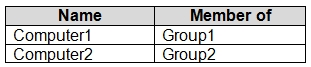
All the computers are enrolled in Microsoft Intune.
You configure the following Maintenance Scheduler settings in the Default Domain Policy:
✑ Turn off auto-restart for updates during active hours: Enabled
✑ Active hours start: 08:00
✑ Active hours end: 22:00
In Intune, you create a device configuration profile named Profile1 that has the following OMA-URI settings:
✑ ./Device/Vendor/MSFT/Policy/Config/ControlPolicyConflict/MDMWinsOverGP set to value 1
✑ ./Device/Vendor/MSFT/Policy/Config/Update/ActiveHoursStart set to value 9
✑ ./Device/Vendor/MSFT/Policy/Config/Update/ActiveHoursEnd set to value 21
You assign Profile to Group1.
How are the active hours configured on Computer1 and Computer2? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area: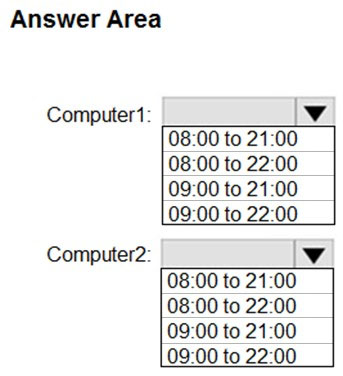
Answer:
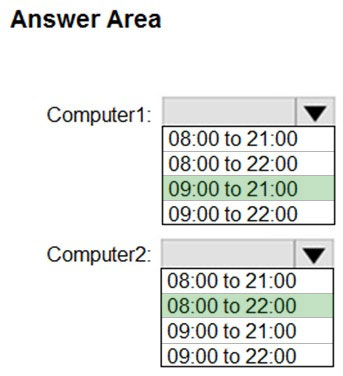
Box 1: 09:00 to 21:00 -
For Computer1 Profile1 overrides the Default Domain Policy.
Box 2: 08:00 to 22:00 -
Computer2 uses the default Domain Policy.
Reference:
https://docs.microsoft.com/en-us/windows/client-management/mdm/policy-csp-controlpolicyconflict
HOTSPOT -
You have a Microsoft 365 subscription.
You have 25 Microsoft Surface Hub devices that you plan to manage by using Microsoft Endpoint Manager.
You need to configure the devices to meet the following requirements:
✑ Enable Windows Hello for Business.
✑ Configure Microsoft Defender SmartScreen to block users from running unverified files.
Which profile types should you configure? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area: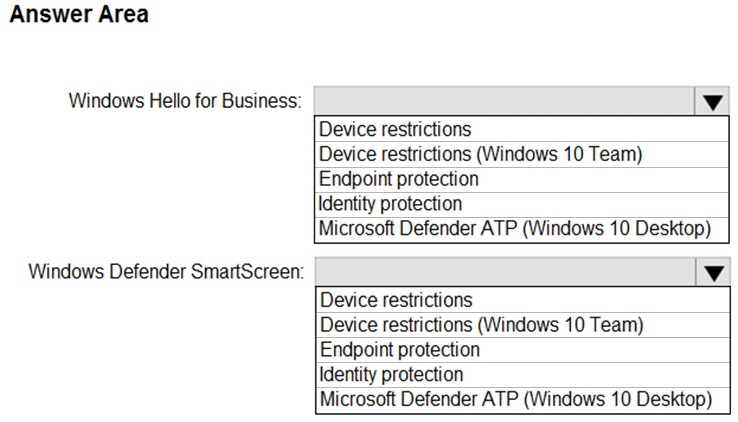
Answer:
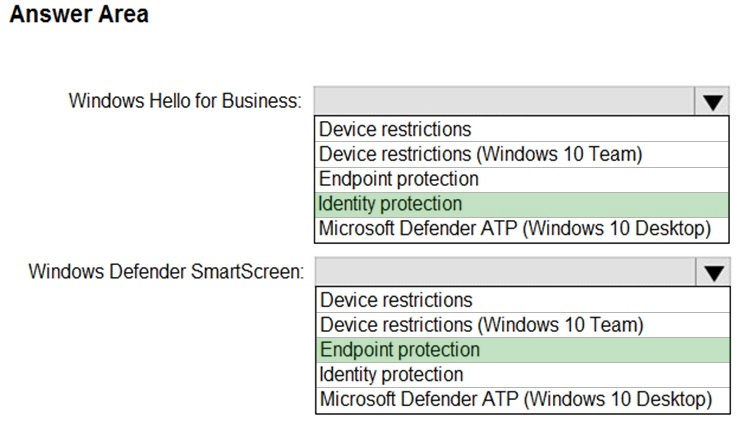
Box 1: Identity protection -
In the Windows Hello for Business settings you can configure in an Identity protection profile. Identity protection profiles are part of device configuration policy in
Microsoft Intune. With an Identity protection profile, you can configure settings on discrete groups of Windows 10/11 devices.
Box 2: Endpoint protection -
Microsoft Intune includes many settings to help protect your devices. These settings are created in an endpoint protection configuration profile in Intune to control security, including BitLocker and Microsoft Defender.
Reference:
https://docs.microsoft.com/en-us/mem/intune/protect/identity-protection-windows-settings?toc=/intune/configuration/toc.json&bc=/intune/configuration/breadcrumb/ toc.json https://docs.microsoft.com/en-us/mem/intune/protect/endpoint-protection-windows-10?toc=/intune/configuration/toc.json&bc=/intune/configuration/breadcrumb/ toc.json
DRAG DROP -
Your network contains an Active Directory domain that is synced to Microsoft Azure Active Directory (Azure AD). All computers are joined to the domain and registered to Azure AD.
The network contains a Microsoft Endpoint Configuration Manager deployment that is configured for co-management with Microsoft Intune.
All the computers in the finance department are managed by using Endpoint Configuration Manager. All the computers in the marketing department are managed by using Intune.
You install new computers for the users in the marketing department by using the Microsoft Deployment Toolkit (MDT).
You purchase an application named App1 that uses an MSI package.
You need to install App1 on the finance department computers and the marketing department computers.
How should you deploy App1 to each department? To answer, drag the appropriate deployment methods to the correct departments. Each deployment method may be used once, more than once, or not at all. You may need to drag the split bat between panes or scroll to view content.
NOTE: Each correct selection is worth one point.
Select and Place: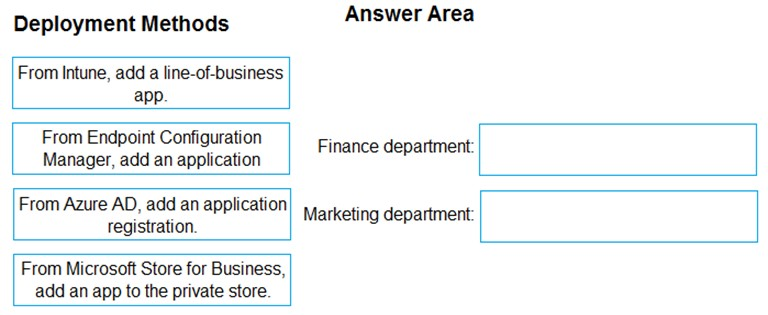
Answer:
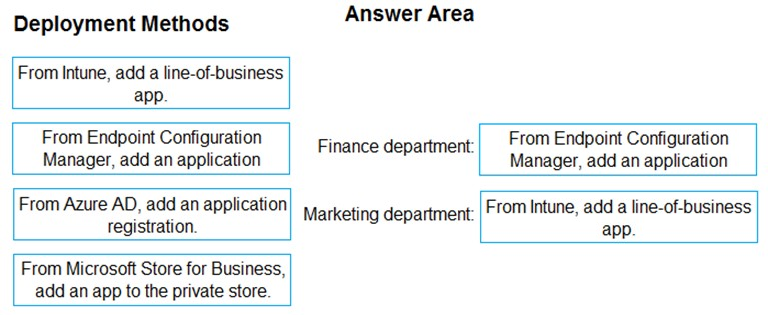
Box 1: From Endpoint Configuration Manager, add an application
All the computers in the finance department are managed by using Endpoint Configuration Manager.
Distribute the application content.
1. In the Configuration Manager console, choose Software Library.
2. In the Software Library workspace, expand Applications. Then, in the list of applications, select the application.
3. Etc.
Box 2: From Intune, add a line-of-business app
All the computers in the marketing department are managed by using Intune.
Before you can configure, assign, protect, or monitor apps, you must add them to Microsoft Intune.
You can add an app in Microsoft Intune by selecting Apps > All apps > Add. The Select app type pane is displayed and allows you to select the App type.
Note: An LOB app is one that you add from an app installation file.
Reference:
https://docs.microsoft.com/en-us/intune/apps-add
https://docs.microsoft.com/en-us/sccm/apps/get-started/create-and-deploy-an-application
Your company has a Microsoft 365 subscription.
The company uses Microsoft Intune to manage all devices.
The company uses conditional access to restrict access to Microsoft 365 services for devices that do not comply with the company's security policies.
You need to identify which devices will be prevented from accessing Microsoft 365 services.
What should you use?
Answer:
C
Monitor Intune Device compliance policies.
1. Open the Intune Device compliance dashboard:
2. Sign in to the Microsoft Endpoint Manager admin center.
3. Select Devices > Overview > Compliance status tab.
Note: Compliance reports help you review device compliance and troubleshoot compliance-related issues in your organization. Using these reports, you can view information on:
✑ The overall compliance states of devices
✑ The compliance status for an individual setting
✑ The compliance status for an individual policy
✑ Drill down into individual devices to view specific settings and policies that affect the device
Reference:
https://docs.microsoft.com/en-us/mem/intune/protect/compliance-policy-monitor
HOTSPOT -
You have 200 computers that run Windows 10.
You need to create a provisioning package to configure the following tasks:
✑ Remove the Microsoft News and the Xbox Microsoft Store apps.
✑ Add a VPN connection to the corporate network.
Which two customizations should you configure? To answer, select the appropriate customizations in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:
Answer:
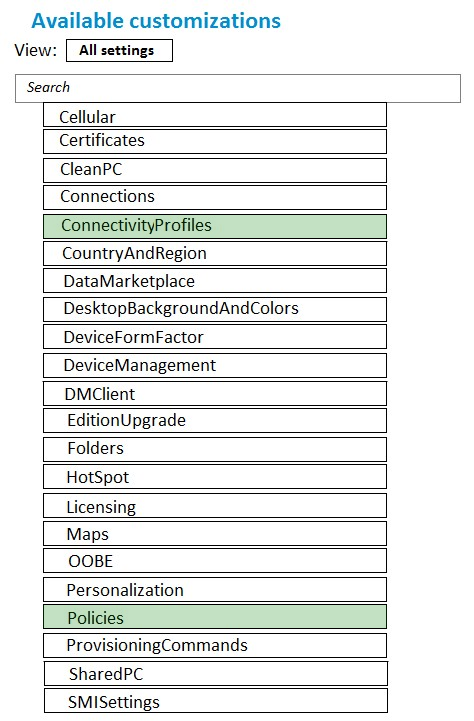
Box 1: ConnectivityProfiles -
Add a VPN connection to the corporate network.
ConnectivityProfiles is used to configure profiles that a user will connect with, such as an email account or VPN profile.
Box 2: Policies -
Remove the Microsoft News and the Xbox Microsoft Store apps.
ApplicationManagement policies, such as ApplicationManagement/DisableStoreOriginatedApps, are included in policies on Windows 10.
Reference:
https://docs.microsoft.com/en-us/windows/configuration/wcd/wcd-connectivityprofiles https://docs.microsoft.com/en-us/windows/client-management/mdm/policy-configuration-service-provider#applicationmanagement-applicationrestrictions https://docs.microsoft.com/en-us/windows/configuration/wcd/wcd-policies
You have an Azure Active Directory (Azure AD) tenant named contoso.com.
You create a terms of use (ToU) named Terms1 in contoso.com.
You are creating a conditional access policy named Policy1 to assign a cloud app named App1 to the users in contoso.com.
You need to configure Policy1 to require the users to accept Terms1.
What should you configure in Policy1?
Answer:
A
Before accessing certain cloud apps in your environment, you might want to get consent from users in form of accepting your terms of use (ToU). Azure Active
Directory (Azure AD) Conditional Access provides you with:
A simple method to configure ToU
The option to require accepting your terms of use through a Conditional Access policy
Reference:
https://docs.microsoft.com/en-us/azure/active-directory/conditional-access/require-tou
HOTSPOT -
You have devices enrolled in Microsoft Intune as shown in the following table.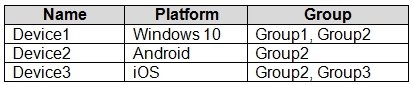
You create device configuration profiles in Intune as shown in the following table.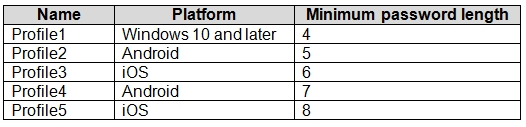
You assign the device configuration profiles to groups as shown in the following table.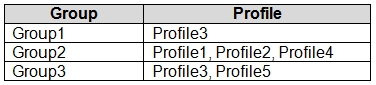
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area: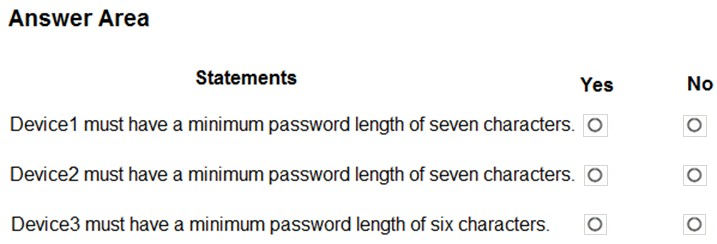
Answer:
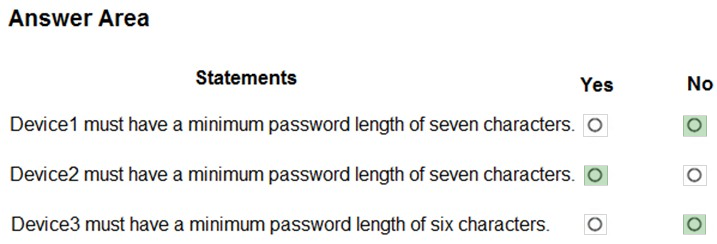
Box 1: No -
Windows 10 Device1 belongs to Group1 and Group2. Group 1 has Profile3. Group2 has Profile1, Profile2 and Profile 4. Profile1, for the correct platform, is the only that applies, with Minimum password length set to 4.
Box 2: Yes -
Android Device2 belongs to Group2. Group2 has Profile1, Profile2 and Profile 4, but only Profile2 applies to Android. Profile2 has a Minimum password length set to 5.
Box 3: No -
iOS Device3 belongs to Group2 and Group3. Group2 has Profile1, Profile2 and Profile 4. Group3 has Profile3 and Profile5. Only Profile3 and Profile5 applies to iOS. Profile5 is the most restrictive with Minimum password length set to 8.
Note: If a compliance policy evaluates against the same setting in another compliance policy, then the most restrictive compliance policy setting applies.
Reference:
https://docs.microsoft.com/en-us/mem/intune/configuration/device-profile-troubleshoot