Which Azure service should you use to store certificates?
Answer:
C
Azure Key Vault is a secure store for storage various types of sensitive information including passwords and certificates.
Azure Key Vault can be used to Securely store and tightly control access to tokens, passwords, certificates, API keys, and other secrets.
Secrets and keys are safeguarded by Azure, using industry-standard algorithms, key lengths, and hardware security modules (HSMs). The HSMs used are
Federal Information Processing Standards (FIPS) 140-2 Level 2 validated.
Access to a key vault requires proper authentication and authorization before a caller (user or application) can get access. Authentication establishes the identity of the caller, while authorization determines the operations that they are allowed to perform.
References:
https://docs.microsoft.com/en-us/azure/key-vault/key-vault-overview
Which Azure service can you use as a security information and event management (SIEM) solution?
Answer:
B
Reference:
https://azure.microsoft.com/en-in/services/azure-sentinel/
HOTSPOT -
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area: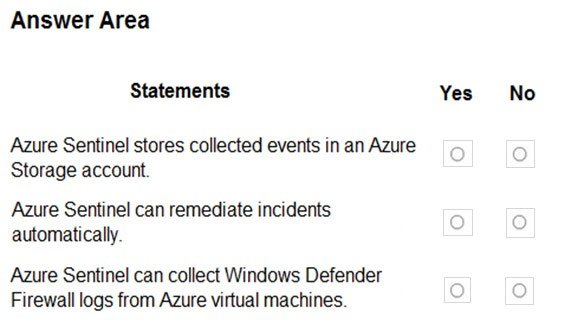
Answer:
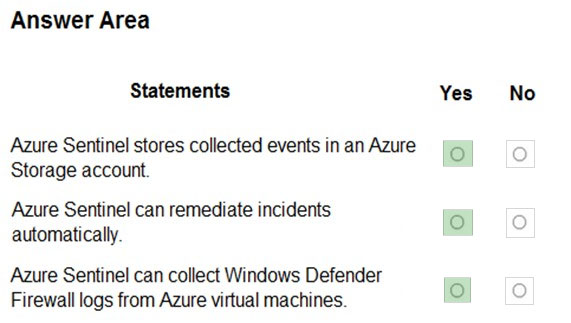
Reference:
https://docs.microsoft.com/en-us/azure/sentinel/overview
DRAG DROP -
Match the Azure Services service to the correct descriptions.
Instructions: To answer, drag the appropriate service from the column on the left to its description on the right. Each service may be used once, more than once, or not at all.
NOTE: Each correct match is worth one point.
Select and Place: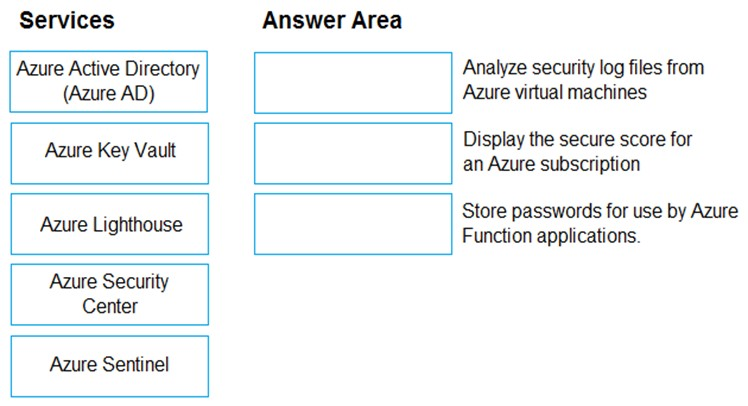
Answer:
Incorrect Answer:
Box 1: Azure Sentinel -
Box 2: Azure Security Center -
Box 3: Azure Key Vault -
✑ Azure Active Directory (Azure AD)
Azure AD is an identity and access management service, which helps your employees sign in and access resources
✑ Azure Lighthouse
Azure Lighthouse is used for cross- and multi-tenant management.
Reference:
https://docs.microsoft.com/en-us/azure/sentinel/overview
https://docs.microsoft.com/en-us/azure/security-center/secure-score-security-controls https://practical365.com/securing-sensitive-information-in-azure-functions-with-the-azure-key-vault/ https://docs.microsoft.com/en-us/azure/active-directory/fundamentals/active-directory-whatis https://docs.microsoft.com/en-us/azure/lighthouse/overview
HOTSPOT -
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area: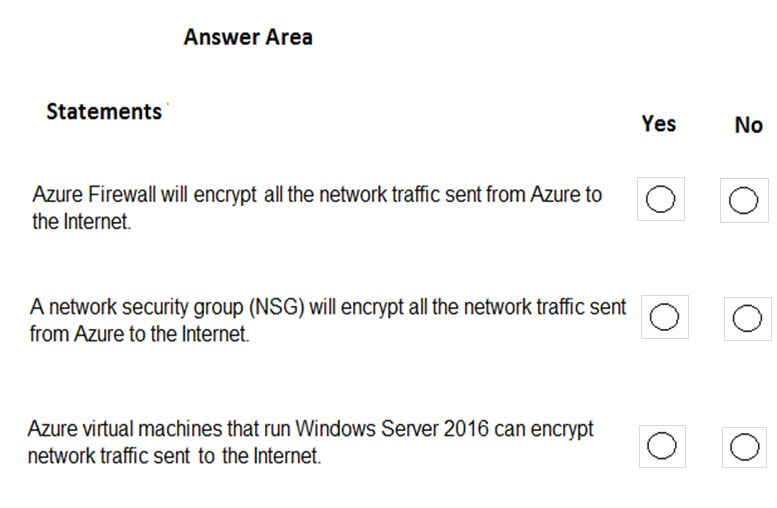
Answer:
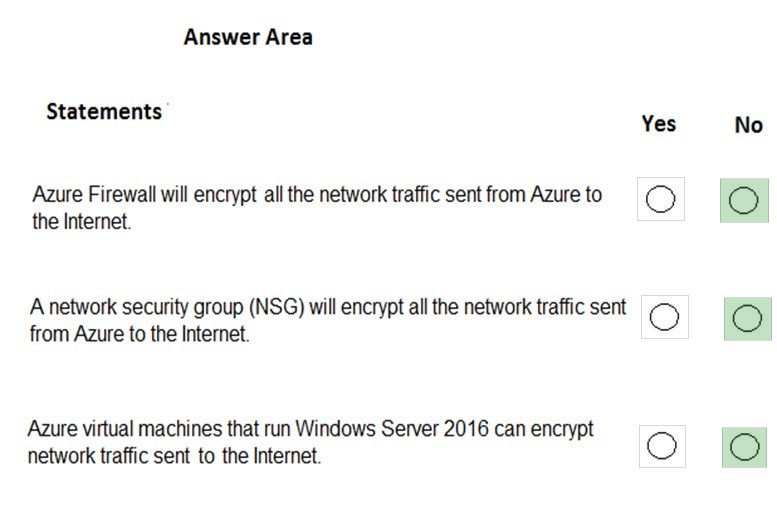
Box 1: No -
Azure firewall does not encrypt network traffic. It is used to block or allow traffic based on source/destination IP address, source/destination ports and protocol.
Box 2: No -
A network security group does not encrypt network traffic. It works in a similar way to a firewall in that it is used to block or allow traffic based on source/ destination IP address, source/destination ports and protocol.
Box 3: No -
The question is rather vague as it would depend on the configuration of the host on the Internet. Windows Server does come with a VPN client and it also supports other encryption methods such IPSec encryption or SSL/TLS so it could encrypt the traffic if the Internet host was configured to require or accept the encryption.
However, the VM could not encrypt the traffic to an Internet host that is not configured to require the encryption.
Reference:
https://docs.microsoft.com/en-us/azure/security/azure-security-data-encryption-best-practices#protect-data-in-transit
HOTSPOT -
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area:
Answer:
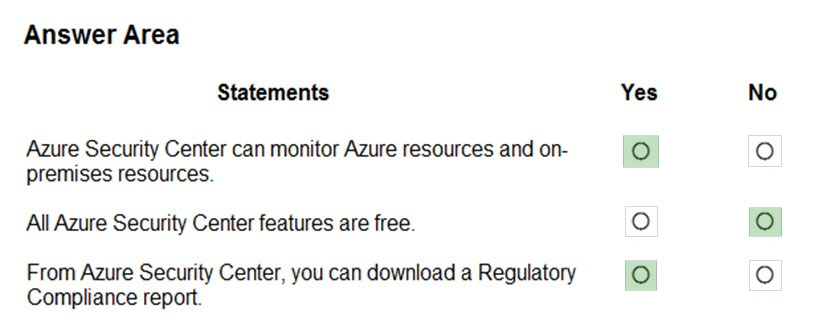
Box 1: Yes -
Azure Security Center is a unified infrastructure security management system that strengthens the security posture of your data centers, and provides advanced threat protection across your hybrid workloads in the cloud - whether they're in Azure or not - as well as on premises.
Box 2: No -
Only two features: Continuous assessment and security recommendations, and Azure secure score, are free.
Box 3: Yes -
The advanced monitoring capabilities in Security Center also let you track and manage compliance and governance over time. The overall compliance provides you with a measure of how much your subscriptions are compliant with policies associated with your workload.
References:
https://docs.microsoft.com/en-us/azure/security-center/security-center-intro
DRAG DROP -
You need to complete the defense-in-depth strategy used in a datacenter.
What should you do? To answer, drag the appropriate layers to the correct positions in the model. Each layer may be used once, more than once, or not at all.
You may need to drag the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.
Select and Place: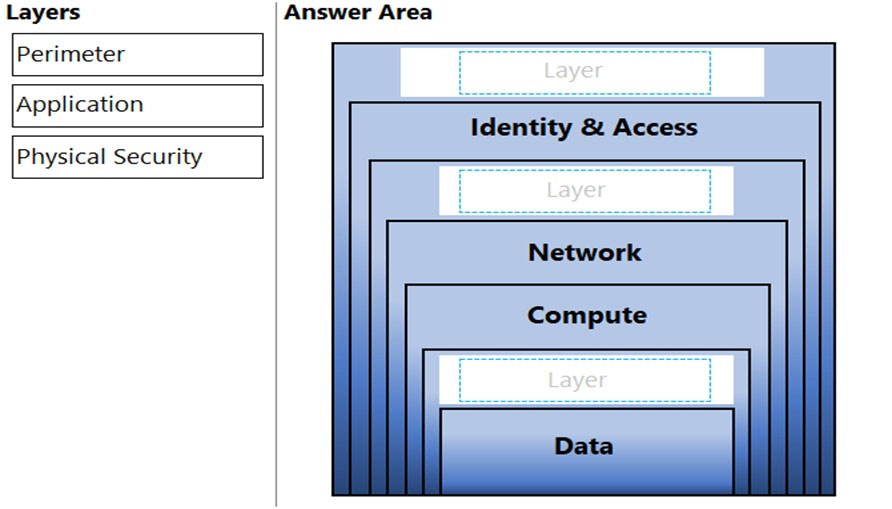
Answer:
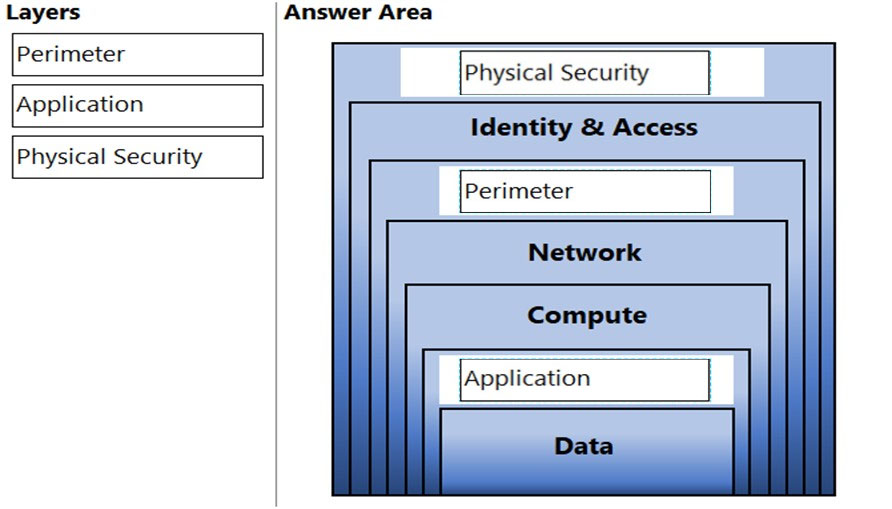
Defence in depth layers (from bottom to top):
✑ Data
- In almost all cases attackers are after data.
- Data can be in database, stored on disk inside VMs, on a SaaS application such as Office 365 or in cloud storage.
- Those storing and controlling access to data to ensures that it's properly secured
- Often regulatory requirements dictates controls & processes
- to ensure confidentiality, integrity, and availability.
✑ Application
- Ensure applications are secure and free of vulnerabilities.
- Store sensitive application secrets in a secure storage medium.
- Make security a design requirement for all application development.
- Integrate security into the application development life cycle.
✑ Compute
- Secure access to virtual machines.
- Implement endpoint protection and keep systems patched and current.
- Malware, unpatched systems, and improperly secured systems open your environment to attacks.
✑ Networking
- Limit communication between resources.
- Deny by default.
- Allow only what is required
- Restrict inbound internet access and limit outbound, where appropriate.
- Implement secure connectivity to on-premises networks.
✑ Perimeter
- Use distributed denial of service (DDoS) protection to filter large-scale attacks before they can cause a denial of service for end users.
- Use perimeter firewalls to identify and alert on malicious attacks against your network.
✑ Identity and access
- Control access to infrastructure and change control.
- Access granted is only what is needed
- Use single sign-on and multi-factor authentication.
- Audit events and changes.
✑ Physical security
- Building security & controlling access to computing hardware.
- First line of defense.
Reference:
https://github.com/undergroundwires/Azure-in-bullet-points/blob/master/AZ-900%20Microsoft%20Azure%20Fundamentals/4.2.%20Defence%20in%20Depth.md
You have an Azure virtual machine named VM1.
You plan to encrypt VM1 by using Azure Disk Encryption.
Which Azure resource must you create first?
Answer:
B
Azure Disk Encryption requires an Azure Key Vault to control and manage disk encryption keys and secrets.
Reference:
https://docs.microsoft.com/en-us/azure/virtual-machines/windows/disk-encryption-overview
Which resources can be used as a source for a Network security group inbound security rule?
Answer:
B
Source or destination:
Any, or an individual IP address, classless inter-domain routing (CIDR) block (10.0.0.0/24, for example), service tag, or application security group.
Reference:
https://docs.microsoft.com/en-us/azure/virtual-network/network-security-groups-overview
HOTSPOT -
To complete the sentence, select the appropriate option in the answer area.
Hot Area:
Answer:
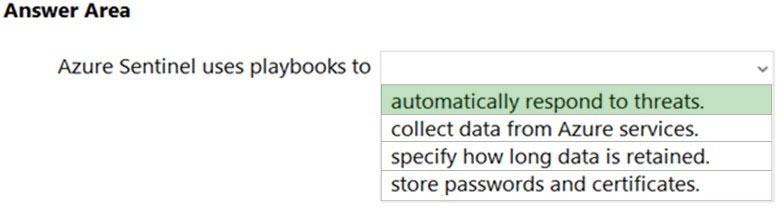
Reference:
https://docs.microsoft.com/en-us/azure/sentinel/tutorial-respond-threats-playbook