SIMULATION -
You need to configure network connectivity between a virtual network named VNET1 and a virtual network named VNET2. The solution must ensure that virtual machines connected to VNET1 can communicate with virtual machines connected to VNET2.
To complete this task, sign in to the Azure portal and modify the Azure resources.
Answer:
See the explanation below.
You need to configure VNet Peering between the two networks. The questions states, ג€The solution must ensure that virtual machines connected to VNET1 can communicate with virtual machines connected to VNET2ג€. It doesn't say the VMs on VNET2 should be able to communicate with VMs on VNET1. Therefore, we need to configure the peering to allow just the one-way communication.
1. In the Azure portal, type Virtual Networks in the search box, select Virtual Networks from the search results then select VNET1. Alternatively, browse to
Virtual Networks in the left navigation pane.
2. In the properties of VNET1, click on Peerings.
3. In the Peerings blade, click Add to add a new peering.
4. In the Name of the peering from VNET1 to remote virtual network box, enter a name such as VNET1-VNET2 (this is the name that the peering will be displayed as in VNET1)
5. In the Virtual Network box, select VNET2.
6. In the Name of the peering from remote virtual network to VNET1 box, enter a name such as VNET2-VNET1 (this is the name that the peering will be displayed as in VNET2).
There is an option Allow virtual network access from VNET to remote virtual network. This should be left as Enabled.
7. For the option Allow virtual network access from remote network to VNET1, click the slider button to Disabled.
8. Click the OK button to save the changes.
Reference:
https://docs.microsoft.com/en-us/azure/virtual-network/virtual-network-manage-peering
SIMULATION -
You need to deploy an Azure firewall to a virtual network named VNET3.
To complete this task, sign in to the Azure portal and modify the Azure resources.
This task might take several minutes to complete. You can perform other tasks while the task completes.
Answer:
See the explanation below.
To add an Azure firewall to a VNET, the VNET must first be configured with a subnet named AzureFirewallSubnet (if it doesn't already exist).
Configure VNET3.
1. In the Azure portal, type Virtual Networks in the search box, select Virtual Networks from the search results then select VNET3. Alternatively, browse to
Virtual Networks in the left navigation pane.
2. In the Overview section, note the Location (region) and Resource Group of the virtual network. We'll need these when we add the firewall.
3. Click on Subnets.
4. Click on + Subnet to add a new subnet.
5. Enter AzureFirewallSubnet in the Name box. The subnet must be named AzureFirewallSubnet.
6. Enter an appropriate IP range for the subnet in the Address range box.
7. Click the OK button to create the subnet.
Add the Azure Firewall.
1. In the settings of VNET3 click on Firewall.
2. Click the Click here to add a new firewall link.
3. The Resource group will default to the VNET3 resource group. Leave this default.
4. Enter a name for the firewall in the Name box.
5. In the Region box, select the same region as VNET3.
6. In the Public IP address box, select an available public IP address if one exists, or click Add new to add a new public IP address.
7. Click the Review + create button.
8. Review the settings and click the Create button to create the firewall.
Reference:
https://docs.microsoft.com/en-us/azure/firewall/tutorial-firewall-deploy-portal
SIMULATION -
You need to configure a virtual network named VNET2 to meet the following requirements:
✑ Administrators must be prevented from deleting VNET2 accidentally.
✑ Administrators must be able to add subnets to VNET2 regularly.
To complete this task, sign in to the Azure portal and modify the Azure resources.
Answer:
See the explanation below.
Locking prevents other users in your organization from accidentally deleting or modifying critical resources, such as Azure subscription, resource group, or resource.
Note: In Azure, the term resource refers to an entity managed by Azure. For example, virtual machines, virtual networks, and storage accounts are all referred to as Azure resources.
1. In the Azure portal, type Virtual Networks in the search box, select Virtual Networks from the search results then select VNET2. Alternatively, browse to
Virtual Networks in the left navigation pane.
2. In the Settings blade for virtual network VNET2, select Locks.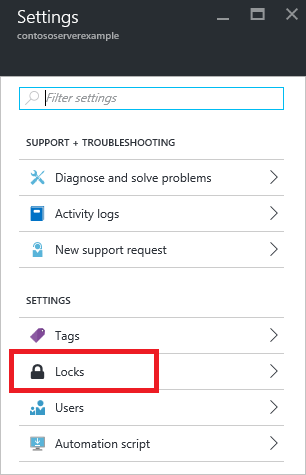
3. To add a lock, select Add.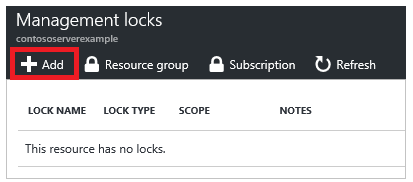
4. For Lock type select Delete lock, and click OK
Reference:
https://docs.microsoft.com/en-us/azure/azure-resource-manager/resource-group-lock-resources
You have an Azure virtual machine named VM1.
From Microsoft Defender for Cloud, you get the following high-severity recommendation: `Install endpoint protection solutions on virtual machine`.
You need to resolve the issue causing the high-severity recommendation.
What should you do?
Answer:
A
Reference:
https://docs.microsoft.com/en-us/azure/security-center/security-center-endpoint-protection
HOTSPOT -
You have a file named File1.yaml that contains the following contents.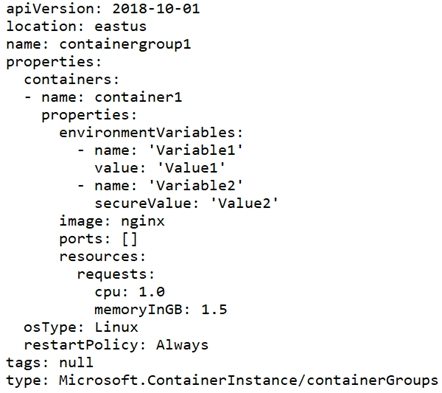
You create an Azure container instance named container1 by using File1.yaml.
You need to identify where you can access the values of Variable1 and Variable2.
What should you identify? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area: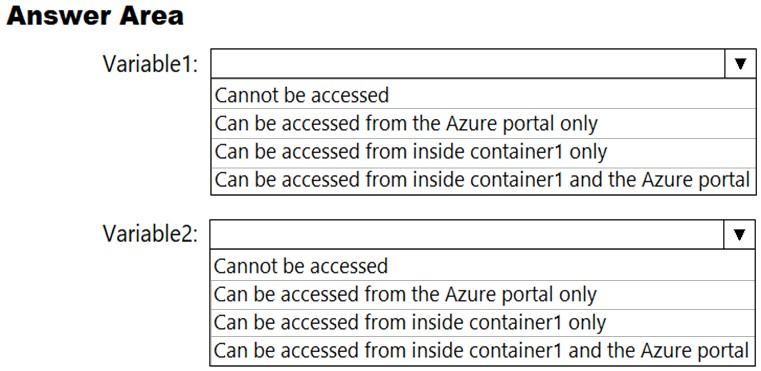
Answer:
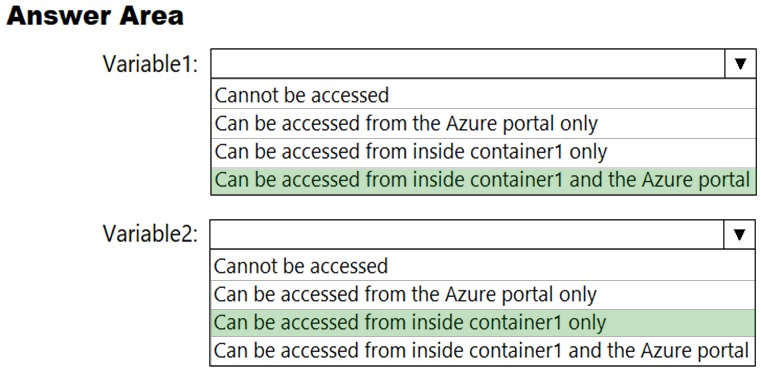
Reference:
https://docs.microsoft.com/en-us/azure/container-instances/container-instances-environment-variables
You have an Azure subscription that contains a virtual network. The virtual network contains the subnets shown in the following table.
The subscription contains the virtual machines shown in the following table.
You enable just in time (JIT) VM access for all the virtual machines.
You need to identify which virtual machines are protected by JIT.
Which virtual machines should you identify?
Answer:
C
An NSG needs to be enabled, either at the VM level or the subnet level.
Reference:
https://docs.microsoft.com/en-us/azure/security-center/security-center-just-in-time
HOTSPOT -
You have an Azure subscription that contains the virtual machines shown in the following table.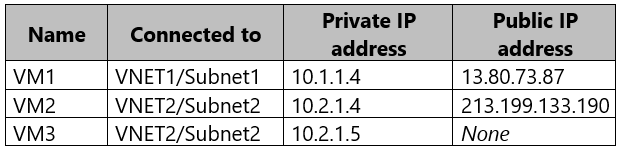
Subnet1 and Subnet2 have a Microsoft.Storage service endpoint configured.
You have an Azure Storage account named storageacc1 that is configured as shown in the following exhibit.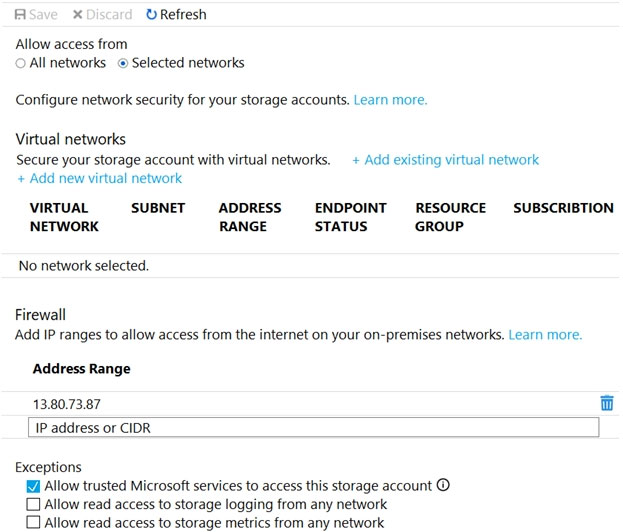
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
Hot Area: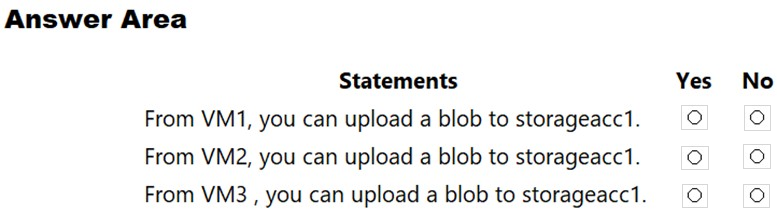
Answer:
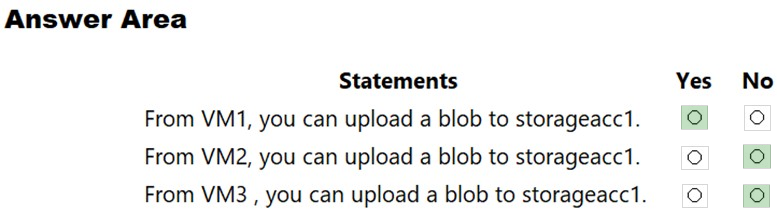
Box 1: Yes -
The public IP of VM1 is allowed through the firewall.
Box 2: No -
The allowed virtual network list is empty so VM2 cannot access storageacc1 directly. The public IP address of VM2 is not in the allowed IP list so VM2 cannot access storageacc1 over the Internet.
Box 3: No -
The allowed virtual network list is empty so VM3 cannot access storageacc1 directly. VM3 does not have a public IP address so it cannot access storageacc1 over the Internet.
Reference:
https://docs.microsoft.com/en-gb/azure/storage/common/storage-network-security
HOTSPOT -
You have Azure virtual machines that have Update Management enabled. The virtual machines are configured as shown in the following table.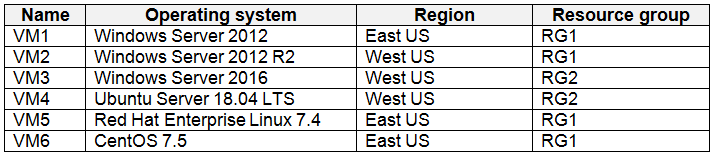
You schedule two update deployments named Update1 and Update2. Update1 updates VM3. Update2 updates VM6.
Which additional virtual machines can be updated by using Update1 and Update2? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:
Answer:
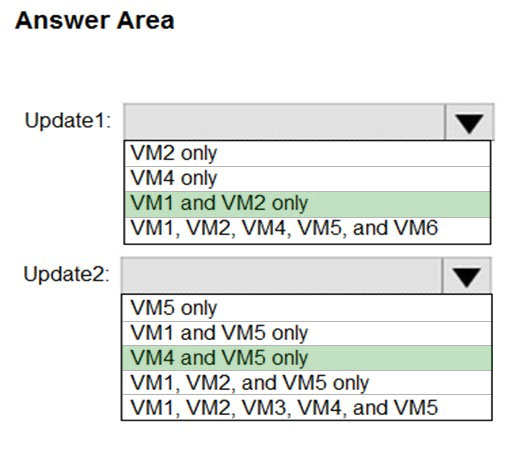
An update deployment can apply to Windows VMs or Linux VMs but not both. The VMs can be in different regions, different subscriptions and different resource groups.
Update1: VM1 and VM2 only -
VM3: Windows Server 2016.
Update2: VM4 and VM5 only -
VM6: CentOS 7.5.
For Linux, the machine must have access to an update repository. The update repository can be private or public.
Reference:
https://docs.microsoft.com/en-us/azure/automation/update-management/overview
HOTSPOT -
You have an Azure subscription named Sub1.
You create a virtual network that contains one subnet. On the subnet, you provision the virtual machines shown in the following table.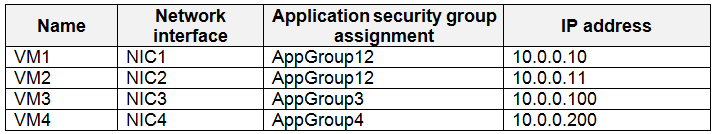
Currently, you have not provisioned any network security groups (NSGs).
You need to implement network security to meet the following requirements:
✑ Allow traffic to VM4 from VM3 only.
✑ Allow traffic from the Internet to VM1 and VM2 only.
✑ Minimize the number of NSGs and network security rules.
How many NSGs and network security rules should you create? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:
Answer:
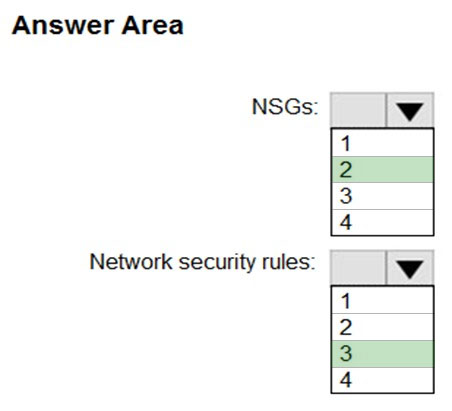
NSGs: 2 -
Network security rules: 3 -
Not 2: You cannot specify multiple service tags or application groups) in a security rule.
References:
https://docs.microsoft.com/en-us/azure/virtual-network/security-overview
HOTSPOT -
You have an Azure key vault.
You need to delegate administrative access to the key vault to meet the following requirements:
✑ Provide a user named User1 with the ability to set advanced access policies for the key vault.
✑ Provide a user named User2 with the ability to add and delete certificates in the key vault.
✑ Use the principle of least privilege.
What should you use to assign access to each user? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area: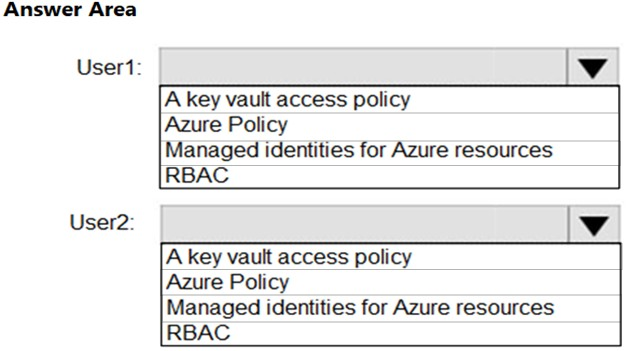
Answer:
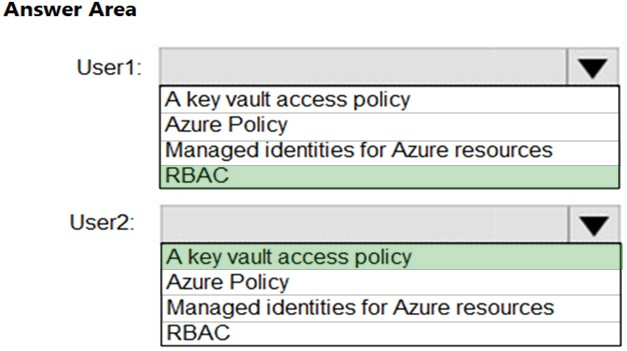
User1: RBAC -
RBAC is used as the Key Vault access control mechanism for the management plane. It would allow a user with the proper identity to:
✑ set Key Vault access policies
✑ create, read, update, and delete key vaults
✑ set Key Vault tags
Note: Role-based access control (RBAC) is a system that provides fine-grained access management of Azure resources. Using RBAC, you can segregate duties within your team and grant only the amount of access to users that they need to perform their jobs.
User2: A key vault access policy
A key vault access policy is the access control mechanism to get access to the key vault data plane. Key Vault access policies grant permissions separately to keys, secrets, and certificates.
References:
https://docs.microsoft.com/en-us/azure/key-vault/key-vault-secure-your-key-vault