SIMULATION -
You need to perform a full malware scan every Sunday at 02:00 on a virtual machine named VM1 by using Microsoft Antimalware for Virtual Machines.
To complete this task, sign in to the Azure portal.
Answer:
See the explanation below.
Deploy the Microsoft Antimalware Extension using the Azure Portal for single VM deployment
1. In Azure Portal, go to the Azure VM1's blade, navigate to the Extensions section and press Add.
2. Select the Microsoft Antimalware extension and press Create.
3. Fill the ג€Install extensionג€ form as desired and press OK.
Scheduled: Enable -
Scan type: Full -
Scan day: Sunday -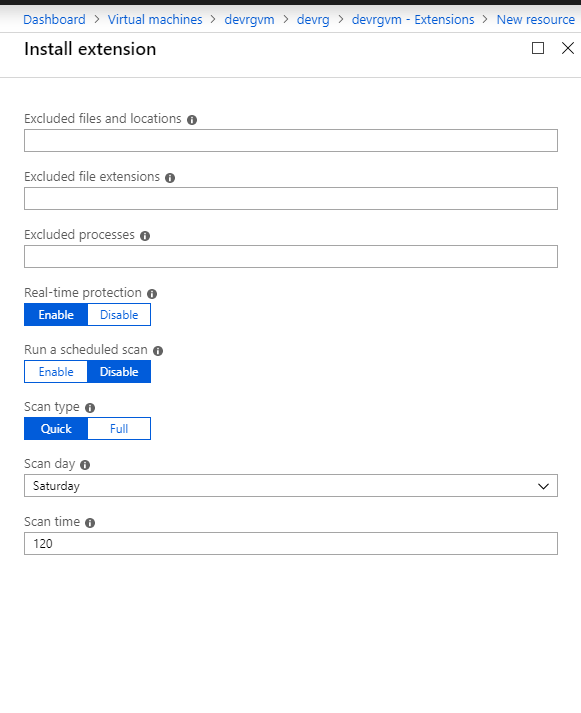
Reference:
https://www.e-apostolidis.gr/microsoft/azure/azure-vm-antimalware-extension-management/
SIMULATION -
You need to prevent administrative users from accidentally deleting a virtual network named VNET1. The administrative users must be allowed to modify the settings of VNET1.
To complete this task, sign in to the Azure portal.
Answer:
See the explanation below.
Locking prevents other users in your organization from accidentally deleting or modifying critical resources, such as Azure subscription, resource group, or resource.
Note: In Azure, the term resource refers to an entity managed by Azure. For example, virtual machines, virtual networks, and storage accounts are all referred to as Azure resources.
1. In the Settings blade for virtual network VNET, select Locks.
2. To add a lock, select Add.
3. For Lock type select Delete lock, and click OK
Reference:
https://docs.microsoft.com/en-us/azure/azure-resource-manager/resource-group-lock-resources
SIMULATION -
You need to grant the required permissions to a user named User2-1234578 to manage the virtual networks in the RG1lod1234578 resource group. The solution must use the principle of least privilege.
To complete this task, sign in to the Azure portal.
Answer:
See the explanation below.
1. In Azure portal, locate and select the RG1lod1234578 resource group.
2. Click Access control (IAM).
3. Click the Role assignments tab to view all the role assignments at this scope.
4. Click Add > Add role assignment to open the Add role assignment pane.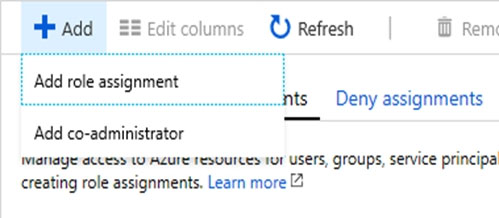
5. In the Role drop-down list, select the role Virtual Machine Contributor.
Virtual Machine Contributor lets you manage virtual machines, but not access to them, and not the virtual network or storage account they're connected to.
6. In the Select list, select user User2-1234578
7. Click Save to assign the role.
Reference:
https://docs.microsoft.com/en-us/azure/role-based-access-control/role-assignments-portal https://docs.microsoft.com/en-us/azure/role-based-access-control/built-in-roles#virtual-machine-contributor
SIMULATION -
You need to ensure that only devices connected to a 131.107.0.0/16 subnet can access data in the rg1lod1234578 Azure Storage account.
To complete this task, sign in to the Azure portal.
Answer:
See the explanation below.
Step 1:
1. In Azure portal go to the storage account you want to secure. Here: rg1lod1234578
2. Click on the settings menu called Firewalls and virtual networks.
3. To deny access by default, choose to allow access from Selected networks. To allow traffic from all networks, choose to allow access from All networks.
4. Click Save to apply your changes.
Step 2:
1. Go to the storage account you want to secure. Here: rg1lod1234578
2. Click on the settings menu called Firewalls and virtual networks.
3. Check that you've selected to allow access from Selected networks.
4. To grant access to a virtual network with a new network rule, under Virtual networks, click Add existing virtual network, select Virtual networks and Subnets options. Enter the 131.107.0.0/16 subnet and then click Add.
Note: When network rules are configured, only applications requesting data over the specified set of networks can access a storage account. You can limit access to your storage account to requests originating from specified IP addresses, IP ranges or from a list of subnets in an Azure Virtual Network (VNet).
Reference:
https://docs.microsoft.com/en-us/azure/storage/common/storage-network-security
HOTSPOT -
You create resources in an Azure subscription as shown in the following table.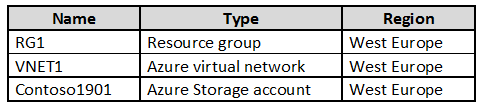
VNET1 contains two subnets named Subnet1 and Subnet2. Subnet1 has a network ID of 10.0.0.0/24. Subnet2 has a network ID of 10.1.1.0/24.
Contoso1901 is configured as shown in the exhibit. (Click the Exhibit tab.)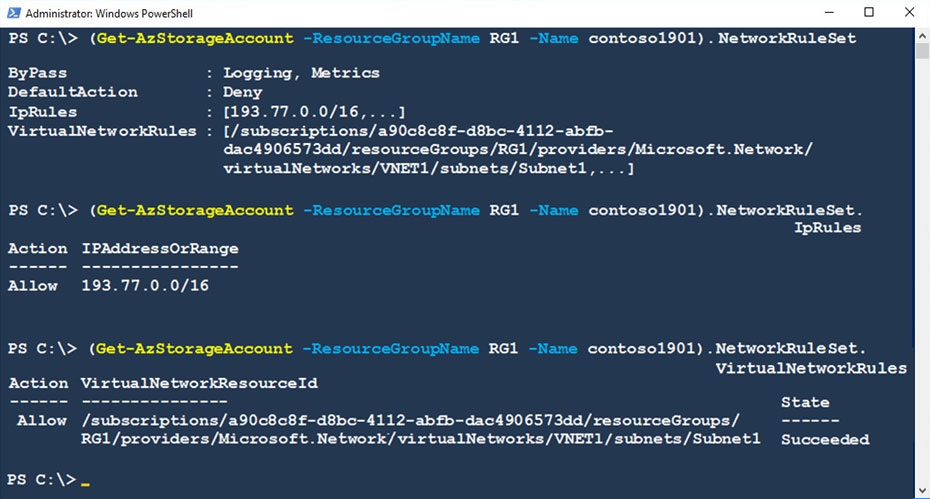
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area: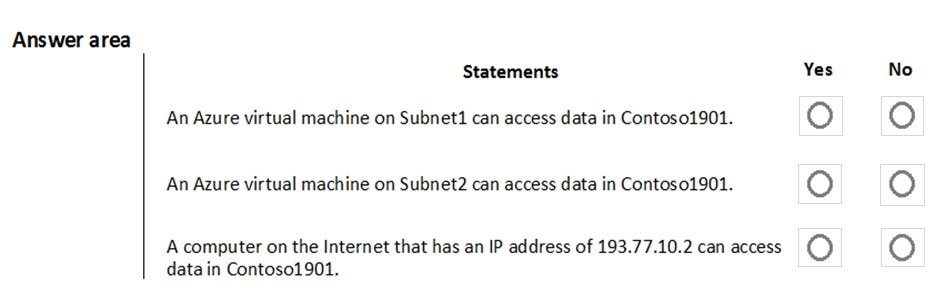
Answer:
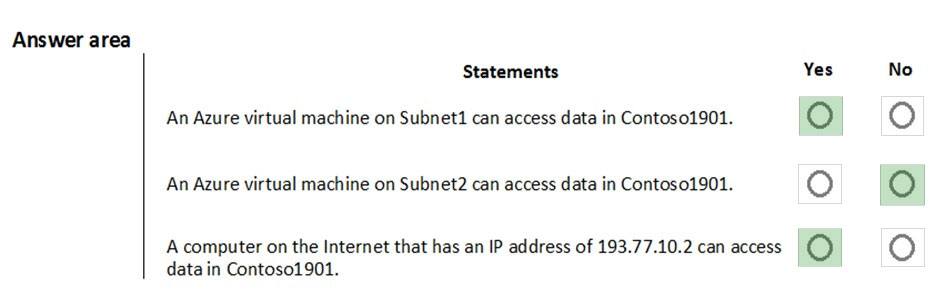
Box 1: Yes -
Access from Subnet1 is allowed.
Box 2: No -
No access from Subnet2 is allowed.
Box 3: Yes -
Access from IP address 193.77.10.2 is allowed.
You have an Azure subscription that contains the virtual machines shown in the following table.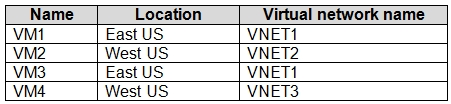
All the virtual networks are peered.
You deploy Azure Bastion to VNET2.
Which virtual machines can be protected by the bastion host?
Answer:
A
Reference:
https://docs.microsoft.com/en-us/azure/bastion/vnet-peering
You have Azure Resource Manager templates that you use to deploy Azure virtual machines.
You need to disable unused Windows features automatically as instances of the virtual machines are provisioned.
What should you use?
Answer:
B
You can use Azure Automation State Configuration to manage Azure VMs (both Classic and Resource Manager), on-premises VMs, Linux machines, AWS VMs, and on-premises physical machines.
Note: Azure Automation State Configuration provides a DSC pull server similar to the Windows Feature DSC-Service so that target nodes automatically receive configurations, conform to the desired state, and report back on their compliance. The built-in pull server in Azure Automation eliminates the need to set up and maintain your own pull server. Azure Automation can target virtual or physical Windows or Linux machines, in the cloud or on-premises.
Reference:
https://docs.microsoft.com/en-us/azure/automation/automation-dsc-getting-started
You have an Azure subscription named Sub1. Sub1 contains a virtual network named VNet1 that contains one subnet named Subnet1.
Subnet1 contains an Azure virtual machine named VM1 that runs Ubuntu Server 18.04.
You create a service endpoint for Microsoft.Storage in Subnet1.
You need to ensure that when you deploy Docker containers to VM1, the containers can access Azure Storage resources by using the service endpoint.
What should you do on VM1 before you deploy the container?
Answer:
C
The Azure Virtual Network container network interface (CNI) plug-in installs in an Azure Virtual Machine. The plug-in supports both Linux and Windows platform.
The plug-in assigns IP addresses from a virtual network to containers brought up in the virtual machine, attaching them to the virtual network, and connecting them directly to other containers and virtual network resources. The plug-in doesn't rely on overlay networks, or routes, for connectivity, and provides the same performance as virtual machines.
The following picture shows how the plug-in provides Azure Virtual Network capabilities to Pods: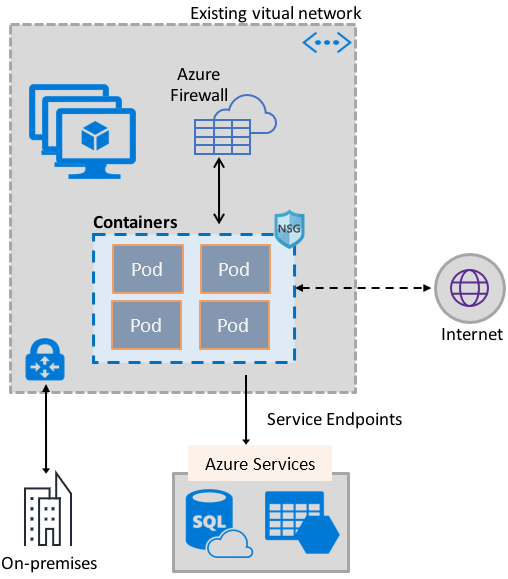
References:
https://docs.microsoft.com/en-us/azure/virtual-network/container-networking-overview
You have Azure Resource Manager templates that you use to deploy Azure virtual machines.
You need to disable unused Windows features automatically as instances of the virtual machines are provisioned.
What should you use?
Answer:
B
The primary use case for the Azure Desired State Configuration (DSC) extension is to bootstrap a VM to the Azure Automation State Configuration (DSC) service.
The service provides benefits that include ongoing management of the VM configuration and integration with other operational tools, such as Azure Monitoring.
Using the extension to register VM's to the service provides a flexible solution that even works across Azure subscriptions.
Reference:
https://docs.microsoft.com/en-us/azure/virtual-machines/extensions/dsc-overview
DRAG DROP -
You have an Azure subscription that contains the virtual networks shown in the following table.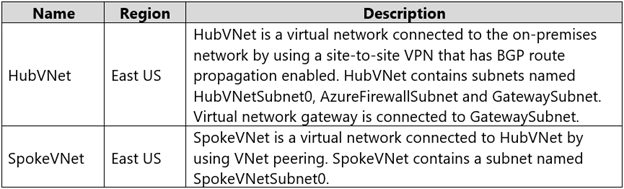
The Azure virtual machines on SpokeVNetSubnet0 can communicate with the computers on the on-premises network.
You plan to deploy an Azure firewall to HubVNet.
You create the following two routing tables:
✑ RT1: Includes a user-defined route that points to the private IP address of the Azure firewall as a next hop address
✑ RT2: Disables BGP route propagation and defines the private IP address of the Azure firewall as the default gateway
You need to ensure that traffic between SpokeVNetSubnet0 and the on-premises network flows through the Azure firewall.
To which subnet should you associate each route table? To answer, drag the appropriate subnets to the correct route tables. Each subnet may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.
Select and Place:
Answer:
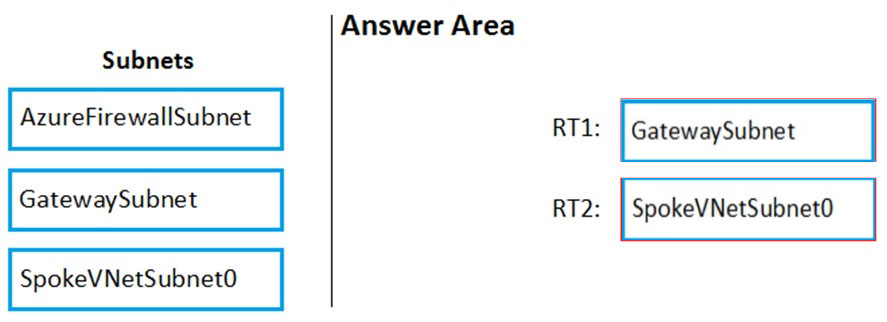
Reference:
https://docs.microsoft.com/en-us/azure/firewall/tutorial-hybrid-portal#create-the-routes