HOTSPOT -
You have an Azure subscription that contains the custom roles shown in the following table.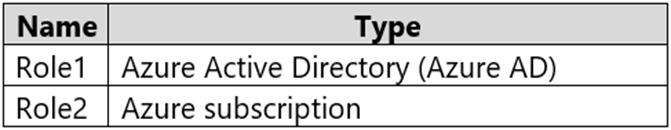
In the Azure portal, you plan to create new custom roles by cloning existing roles. The new roles will be configured as shown in the following table.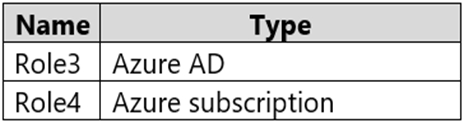
Which roles can you clone to create each new role? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area: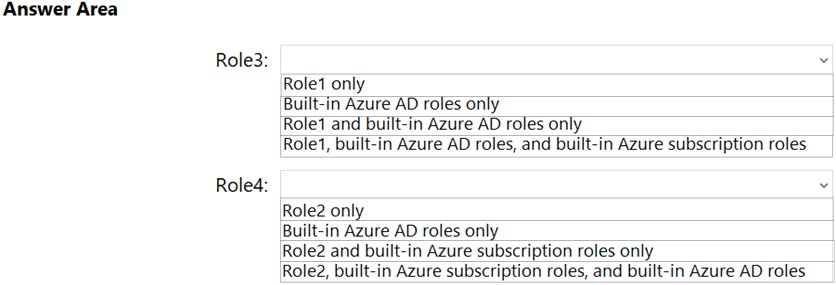
Answer:
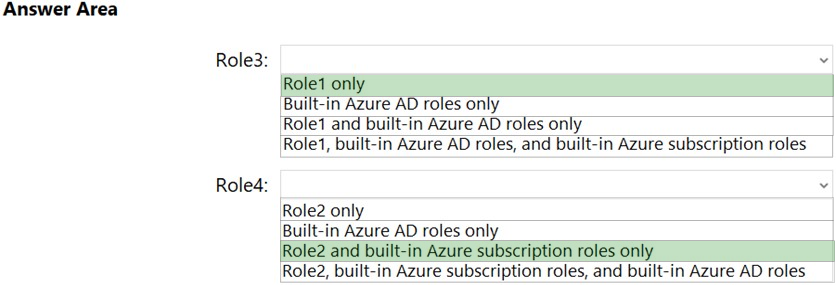
Reference:
https://docs.microsoft.com/en-us/azure/active-directory/roles/custom-create https://docs.microsoft.com/en-us/azure/role-based-access-control/custom-roles-portal
HOTSPOT -
You have an Azure subscription that contains the Azure Active Directory (Azure AD) resources shown in the following table.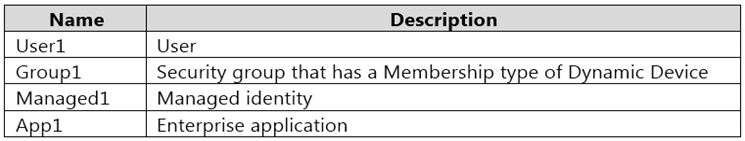
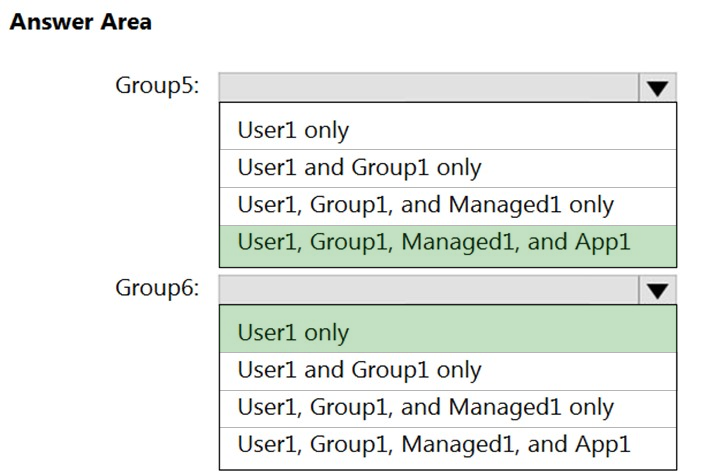
You create the groups shown in the following table.
Which resources can you add to Group5 and Group6? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area: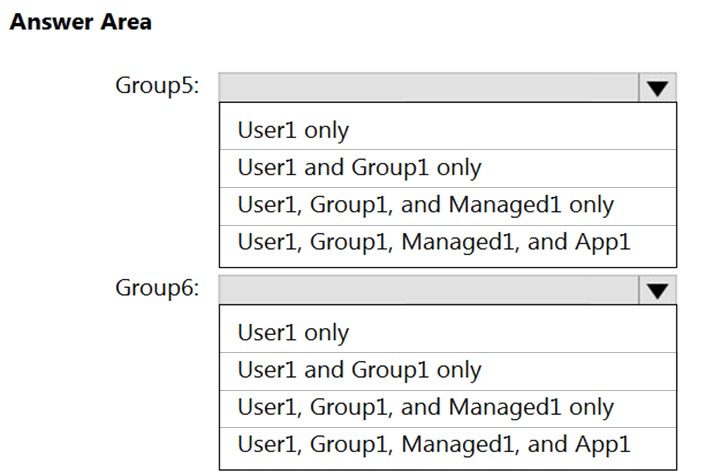
Answer:
HOTSPOT -
You have an Azure Active Directory (Azure AD) tenant named contoso.com that contains three security groups named Group1, Group2, and Group3 and the users shown in the following table.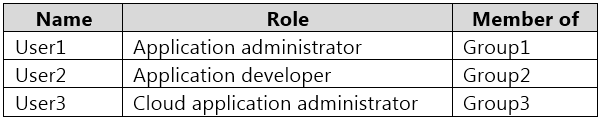
Group3 is a member of Group2.
In contoso.com, you register an enterprise application named App1 that has the following settings:
✑ Owners: User1
✑ Users and groups: Group2
You configure the properties of App1 as shown in the following exhibit.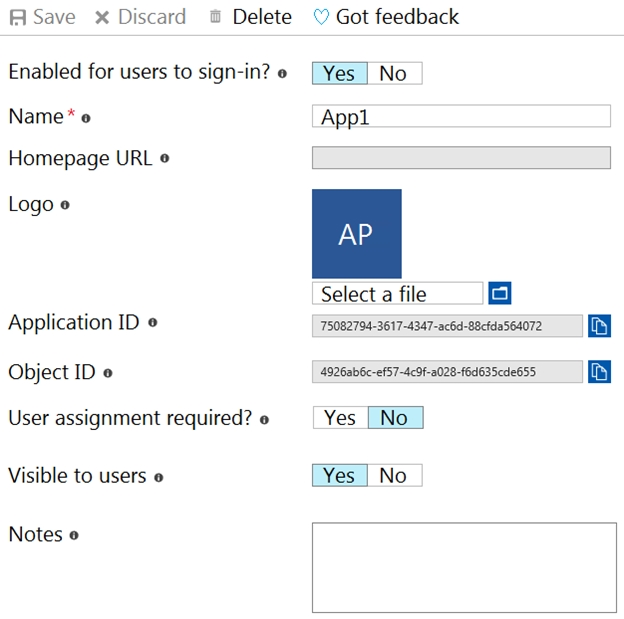
For each of the following statements, select Yes if the statement is true. Otherwise, select no.
NOTE: Each correct selection is worth one point.
Hot Area:
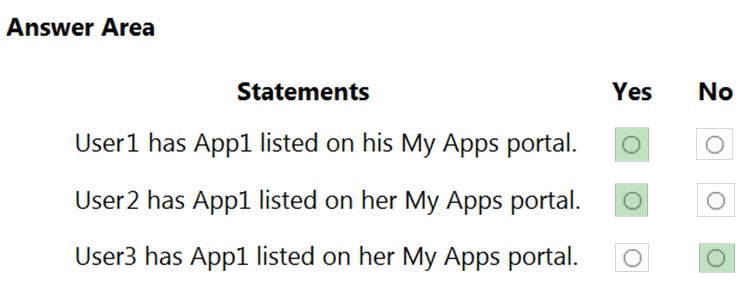
Answer:
Reference:
https://docs.microsoft.com/en-us/azure/active-directory/manage-apps/assign-user-or-group-access-portal
You have an Azure subscription that contains the resources shown in the following table.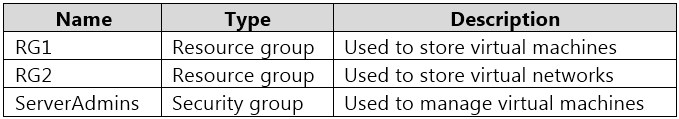
You need to ensure that ServerAdmins can perform the following tasks:
✑ Create virtual machines in RG1 only.
✑ Connect the virtual machines to the existing virtual networks in RG2 only.
The solution must use the principle of least privilege.
Which two role-based access control (RBAC) roles should you assign to ServerAdmins? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
Answer:
AF
Reference:
https://docs.microsoft.com/en-us/azure/role-based-access-control/built-in-roles
HOTSPOT -
Your network contains an on-premises Active Directory domain named adatum.com that syncs to Azure Active Directory (Azure AD).
The Azure AD tenant contains the users shown in the following table.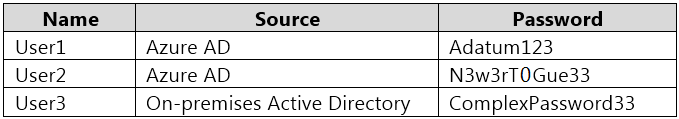
You configure the Authentication methods `" Password Protection settings for adatum.com as shown in the following exhibit.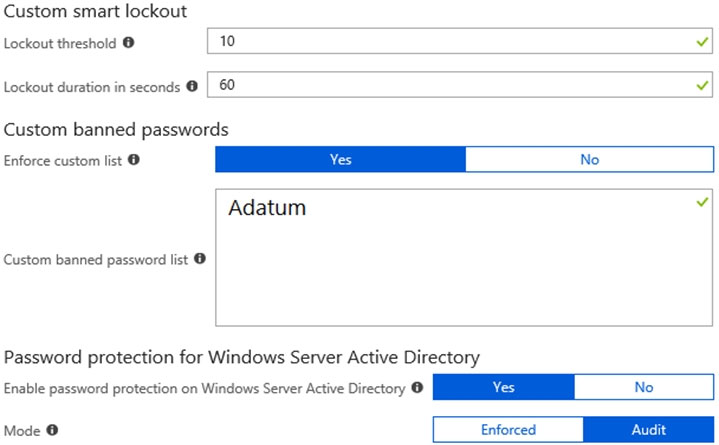
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area: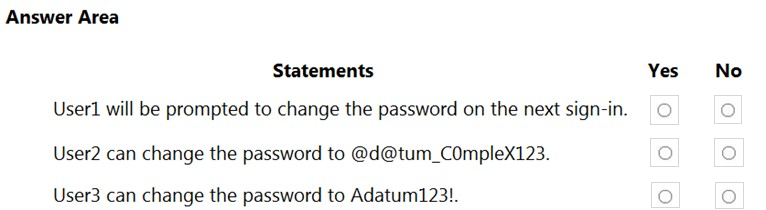
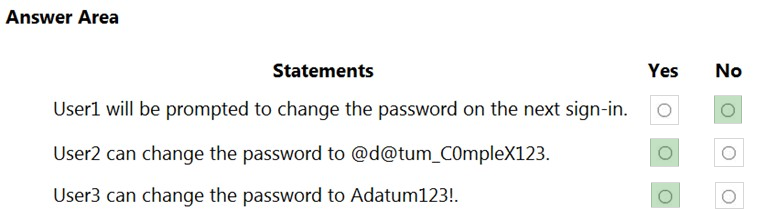
Answer:
Reference:
https://docs.microsoft.com/en-us/azure/active-directory/authentication/howto-password-ban-bad-on-premises-deploy https://docs.microsoft.com/en-us/azure/active-directory/authentication/concept-password-ban-bad
HOTSPOT -
Your company has an Azure subscription named Subscription1. Subscription1 is associated with the Azure Active Directory tenant that includes the users shown in the following table.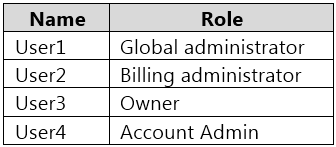
The company is sold to a new owner.
The company needs to transfer ownership of Subscription1.
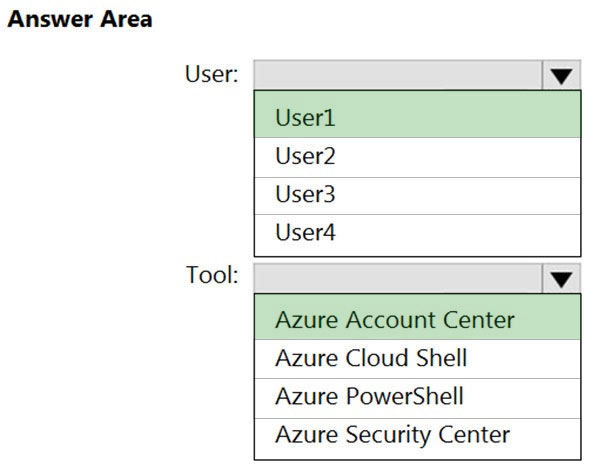
Which user can transfer the ownership and which tool should the user use? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:
Answer:
Reference:
https://docs.microsoft.com/en-us/azure/cost-management-billing/manage/billing-subscription-transfer
You have an Azure subscription that uses Azure Active Directory (Azure AD) Privileged Identity Management (PIM).
A PIM user that is assigned the User Access Administrator role reports receiving an authorization error when performing a role assignment or viewing the list of assignments.
You need to resolve the issue by ensuring that the PIM service principal has the correct permissions for the subscription. The solution must use the principle of least privilege.
Which role should you assign to the PIM service principle?
Answer:
B
You have an Azure Active Directory (Azure AD) tenant that contains a user named Admin1. Admin1 is assigned the Application developer role.
You purchase a cloud app named App1 and register App1 in Azure AD.
Admin1 reports that the option to enable token encryption for App1 is unavailable.
You need to ensure that Admin1 can enable token encryption for App1 in the Azure portal.
What should you do?
Answer:
C
This is a tricky one because uploading a certificate is also required. However, the question states that the Token Encryption option is unavailable. This is because the app is not added as an enterprise application. When the app is added as an enterprise application, the Token Encryption option will be available.
Then you can upload the certificate.
Reference:
https://docs.microsoft.com/en-us/azure/active-directory/manage-apps/howto-saml-token-encryption
You plan to deploy an app that will modify the properties of Azure Active Directory (Azure AD) users by using Microsoft Graph.
You need to ensure that the app can access Azure AD.
What should you configure first?
Answer:
A
Reference:
https://docs.microsoft.com/en-us/azure/active-directory/develop/active-directory-how-applications-are-added
HOTSPOT -
You have an Azure subscription named Subscription1 that contains the resources shown in the following table.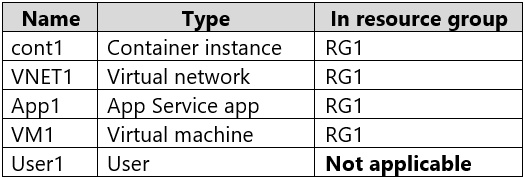
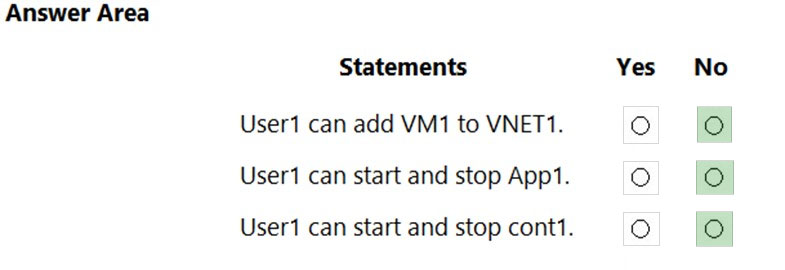
You create a custom RBAC role in Subscription1 by using the following JSON file.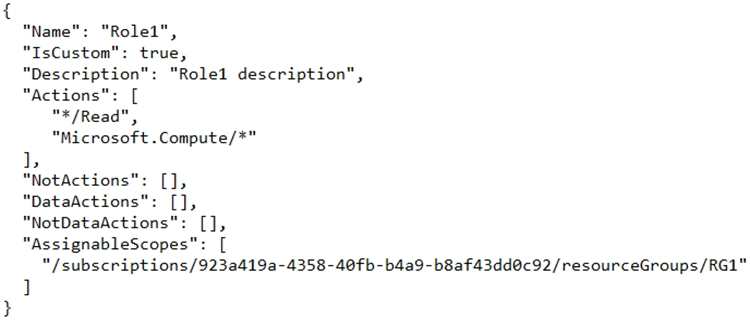
You assign Role1 to User1 on RG1.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area:
Answer:
Reference:
https://docs.microsoft.com/en-us/azure/role-based-access-control/resource-provider-operations#microsoftcompute