DRAG DROP -
You have an Azure subscription that contains 100 virtual machines. Azure Diagnostics is enabled on all the virtual machines.
You are planning the monitoring of Azure services in the subscription.
You need to retrieve the following details:
✑ Identify the user who deleted a virtual machine three weeks ago.
✑ Query the security events of a virtual machine that runs Windows Server 2016.
What should you use in Azure Monitor? To answer, drag the appropriate configuration settings to the correct details. Each configuration setting may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.
Select and Place: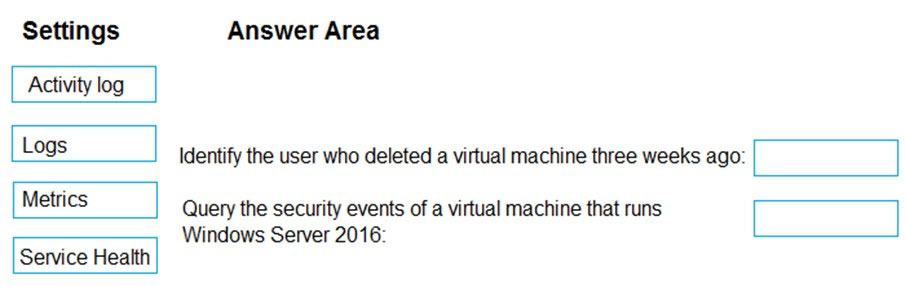
Answer:
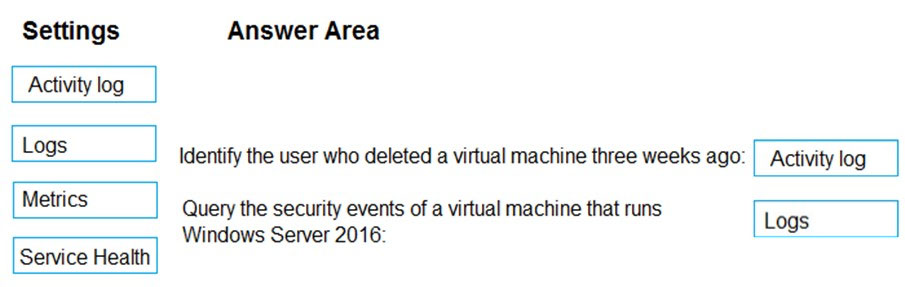
Box1: Activity log -
Azure activity logs provide insight into the operations that were performed on resources in your subscription. Activity logs were previously known as ג€audit logsג€ or
ג€operational logs,ג€ because they report control-plane events for your subscriptions.
Activity logs help you determine the ג€what, who, and whenג€ for write operations (that is, PUT, POST, or DELETE).
Box 2: Logs -
Log Integration collects Azure diagnostics from your Windows virtual machines, Azure activity logs, Azure Security Center alerts, and Azure resource provider logs. This integration provides a unified dashboard for all your assets, whether they're on-premises or in the cloud, so that you can aggregate, correlate, analyze, and alert for security events.
Reference:
https://docs.microsoft.com/en-us/azure/security/azure-log-audit
HOTSPOT -
You have an Azure subscription that contains the resources shown in the following table.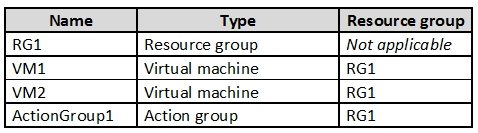
VM1 and VM2 are stopped.
You create an alert rule that has the following settings:
✑ Resource: RG1
✑ Condition: All Administrative operations
✑ Actions: Action groups configured for this alert rule: ActionGroup1
✑ Alert rule name: Alert1
You create an action rule that has the following settings:
✑ Scope: VM1
✑ Filter criteria: Resource Type = "Virtual Machines"
✑ Define on this scope: Suppression
✑ Suppression config: From now (always)
✑ Name: ActionRule1
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
Note: Each correct selection is worth one point.
Hot Area: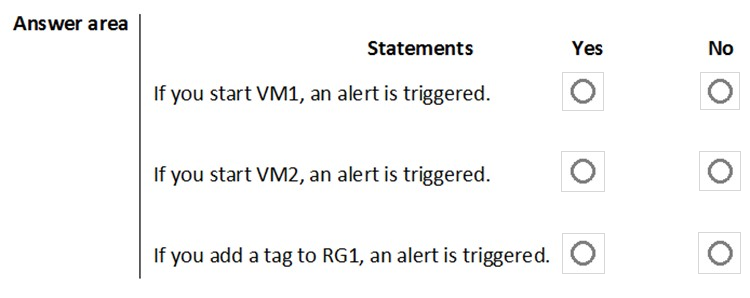
Answer:
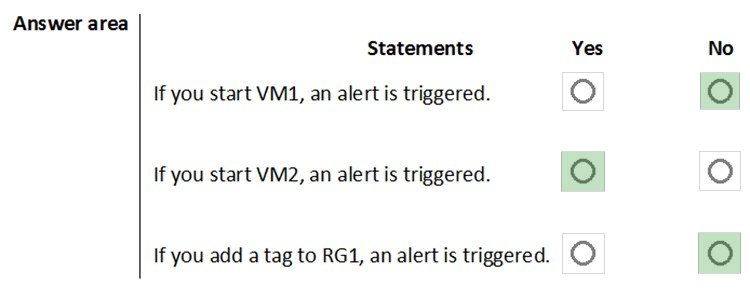
Box 1:
The scope for the action rule is set to VM1 and is set to suppress alerts indefinitely.
Box 2:
The scope for the action rule is not set to VM2.
Box 3:
Adding a tag is not an administrative operation.
References:
https://docs.microsoft.com/en-us/azure/azure-monitor/platform/alerts-activity-log https://docs.microsoft.com/en-us/azure/azure-monitor/platform/alerts-action-rules
DRAG DROP -
You have an Azure subscription named Sub1 that contains an Azure Log Analytics workspace named LAW1.
You have 500 Azure virtual machines that run Windows Server 2016 and are enrolled in LAW1.
You plan to add the System Update Assessment solution to LAW1.
You need to ensure that System Update Assessment-related logs are uploaded to LAW1 from 100 of the virtual machines only.
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.
Select and Place: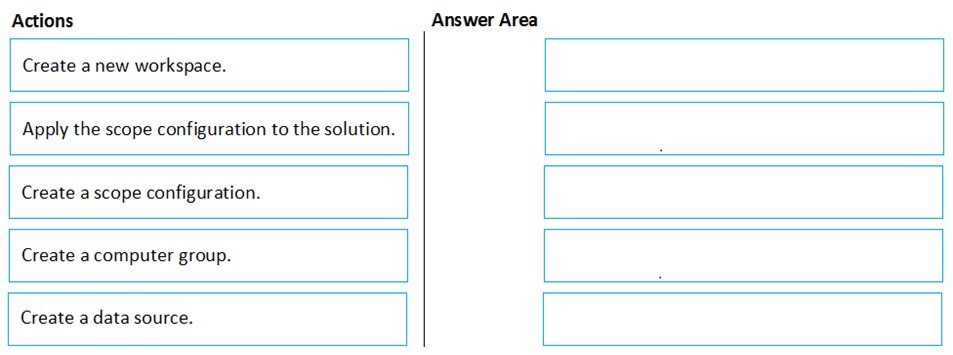
Answer:
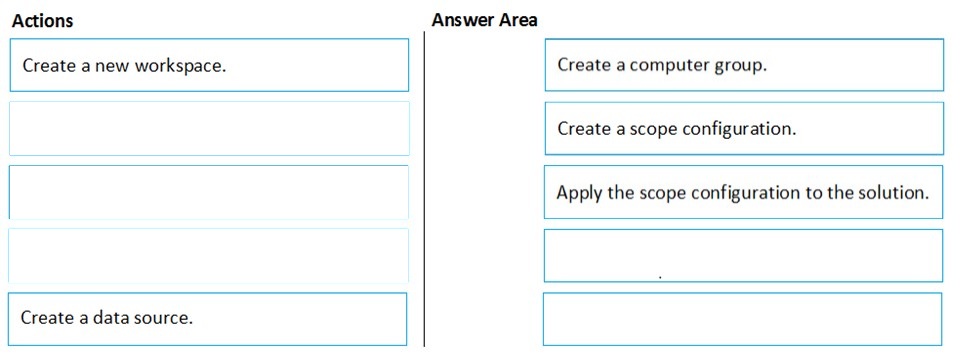
Reference:
https://docs.microsoft.com/en-us/azure/azure-monitor/insights/solution-targeting
You have an Azure subscription named Sub1 that contains the virtual machines shown in the following table.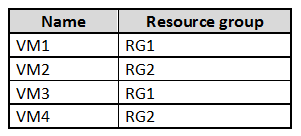
You need to ensure that the virtual machines in RG1 have the Remote Desktop port closed until an authorized user requests access.
What should you configure?
Answer:
D
Just-in-time (JIT) virtual machine (VM) access can be used to lock down inbound traffic to your Azure VMs, reducing exposure to attacks while providing easy access to connect to VMs when needed.
Note: When just-in-time is enabled, Security Center locks down inbound traffic to your Azure VMs by creating an NSG rule. You select the ports on the VM to which inbound traffic will be locked down. These ports are controlled by the just-in-time solution.
When a user requests access to a VM, Security Center checks that the user has Role-Based Access Control (RBAC) permissions that permit them to successfully request access to a VM. If the request is approved, Security Center automatically configures the Network Security Groups (NSGs) and Azure Firewall to allow inbound traffic to the selected ports and requested source IP addresses or ranges, for the amount of time that was specified. After the time has expired, Security
Center restores the NSGs to their previous states. Those connections that are already established are not being interrupted, however.
Reference:
https://docs.microsoft.com/en-us/azure/security-center/security-center-just-in-time
SIMULATION -
You need to ensure that web1234578 is protected from malware by using Microsoft Antimalware for Virtual Machines and is scanned every Friday at 01:00.
To complete this task, sign in to the Azure portal.
Answer:
See the explanation below.
You need to install and configure the Microsoft Antimalware extension on the virtual machine named web1234578.
1. In the Azure portal, type Virtual Machines in the search box, select Virtual Machines from the search results then select web1234578. Alternatively, browse to Virtual Machines in the left navigation pane.
2. In the properties of web11597200, click on Extensions.
3. Click the Add button to add an Extension.
4. Scroll down the list of extensions and select Microsoft Antimalware.
5. Click the Create button. This will open the settings pane for the Microsoft Antimalware Extension.
6. In the Scan day field, select Friday.
7. In the Scan time field, enter 60. The scan time is measured in minutes after midnight so 60 would be 01:00, 120 would be 02:00 etc.
8. Click the OK button to save the configuration and install the extension.
SIMULATION -
You need to ensure that the events in the NetworkSecurityGroupRuleCounter log of the VNET01-Subnet0-NSG network security group (NSG) are stored in the logs1234578 Azure Storage account for 30 days.
To complete this task, sign in to the Azure portal.
Answer:
See the explanation below.
You need to configure the diagnostic logging for the NetworkSecurityGroupRuleCounter log.
1. In the Azure portal, type Network Security Groups in the search box, select Network Security Groups from the search results then select VNET01-
Subnet0-NSG. Alternatively, browse to Network Security Groups in the left navigation pane.
2. In the properties of the Network Security Group, click on Diagnostic Settings.
3. Click on the Add diagnostic setting link.
4. Provide a name in the Diagnostic settings name field. It doesn't matter what name you provide for the exam.
5. In the Log section, select NetworkSecurityGroupRuleCounter.
6. In the Destination details section, select Archive to a storage account.
7. In the Storage account field, select the logs1234578 storage account.
8. In the Retention (days) field, enter 30.
9. Click the Save button to save the changes.
HOTSPOT -
On Monday, you configure an email notification in Azure Security Center to email notifications to [email protected] about alerts that have a severity level of
Low, Medium, or High.
On Tuesday, Security Center generates the security alerts shown in the following table.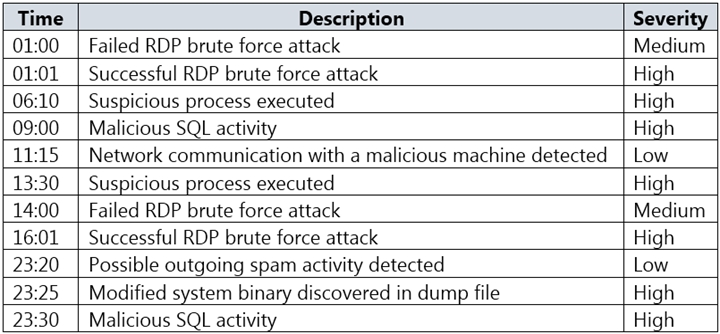
How many email notifications will [email protected] receive on Tuesday? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area: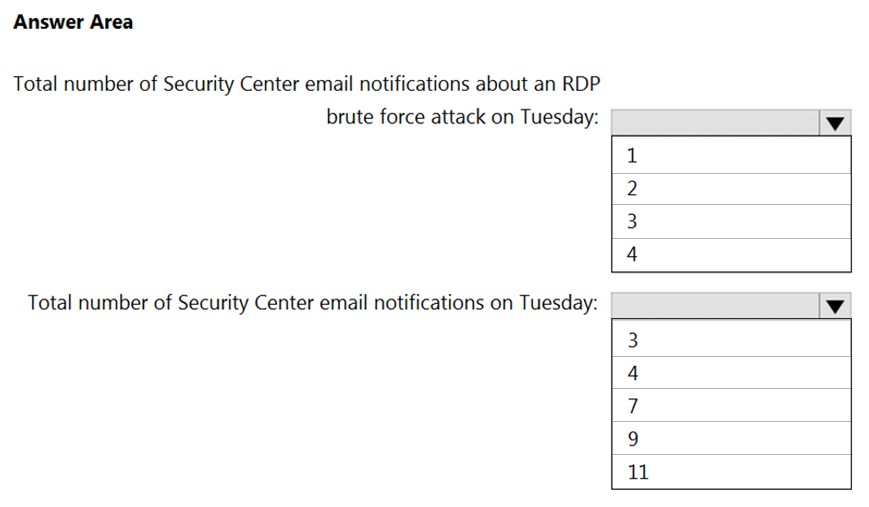
Answer:
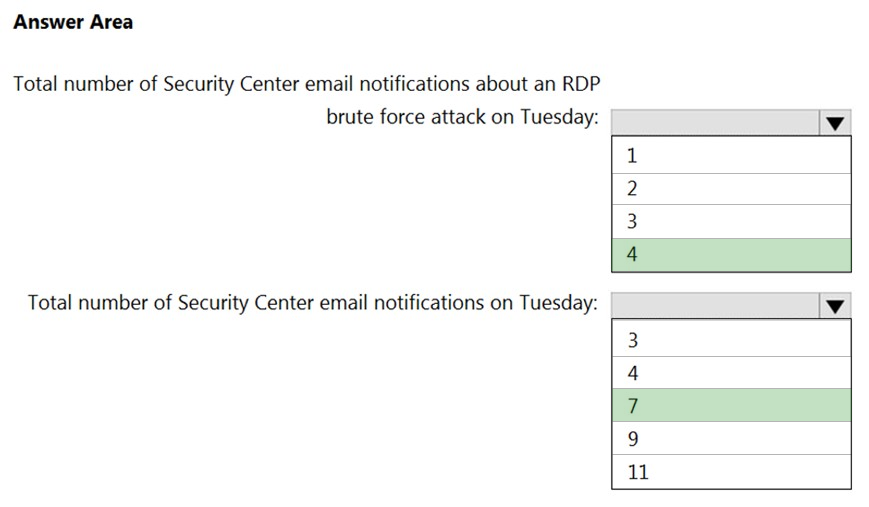
Reference:
https://docs.microsoft.com/en-us/azure/security-center/security-center-provide-security-contact-details
You are troubleshooting a security issue for an Azure Storage account.
You enable the diagnostic logs for the storage account.
What should you use to retrieve the diagnostics logs?
Answer:
B
Reference:
https://docs.microsoft.com/en-us/azure/storage/blobs/monitor-blob-storage?tabs=azure-portal
You have an Azure subscription that contains the resources shown in the following table.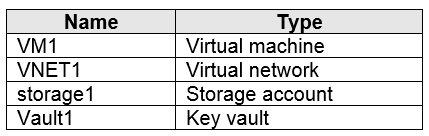
You plan to enable Azure Defender for the subscription.
Which resources can be protected by using Azure Defender?
Answer:
A
Reference:
https://docs.microsoft.com/en-us/azure/security-center/azure-defender
DRAG DROP -
You have an Azure subscription that contains the following resources:
✑ A network virtual appliance (NVA) that runs non-Microsoft firewall software and routes all outbound traffic from the virtual machines to the internet
✑ An Azure function that contains a script to manage the firewall rules of the NVA
✑ Azure Security Center standard tier enabled for all virtual machines
✑ An Azure Sentinel workspace
✑ 30 virtual machines
You need to ensure that when a high-priority alert is generated in Security Center for a virtual machine, an incident is created in Azure Sentinel and then a script is initiated to configure a firewall rule for the NVA.
How should you configure Azure Sentinel to meet the requirements? To answer, drag the appropriate components to the correct requirements. Each component may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.
Select and Place: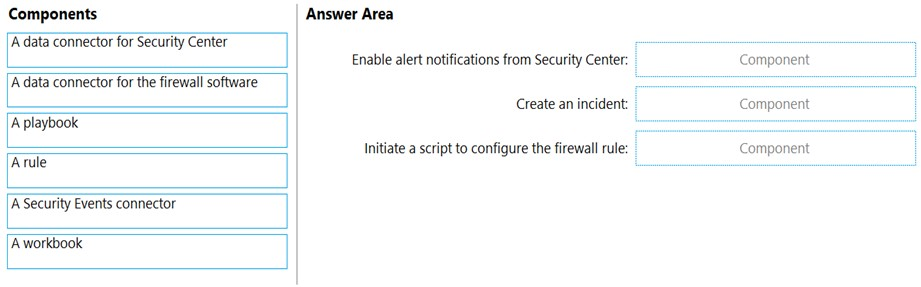
Answer:
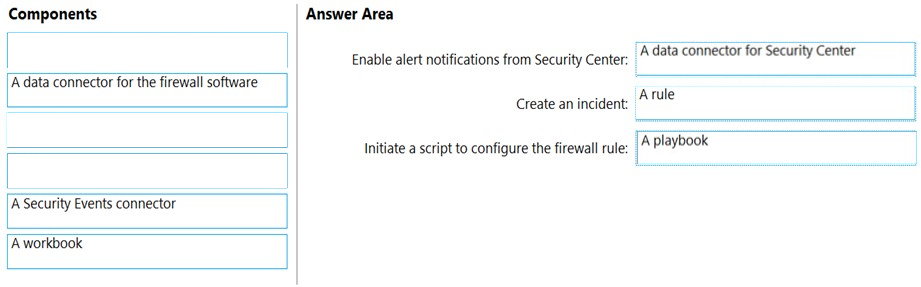
Reference:
https://docs.microsoft.com/en-us/azure/sentinel/create-incidents-from-alerts https://docs.microsoft.com/en-us/azure/sentinel/connect-azure-security-center