You are configuring and securing a network environment.
You deploy an Azure virtual machine named VM1 that is configured to analyze network traffic.
You need to ensure that all network traffic is routed through VM1.
What should you configure?
Answer:
C
Although the use of system routes facilitates traffic automatically for your deployment, there are cases in which you want to control the routing of packets through a virtual appliance. You can do so by creating user defined routes that specify the next hop for packets flowing to a specific subnet to go to your virtual appliance instead, and enabling IP forwarding for the VM running as the virtual appliance.
Note: User Defined Routes -
For most environments you will only need the system routes already defined by Azure. However, you may need to create a route table and add one or more routes in specific cases, such as:
✑ Force tunneling to the Internet via your on-premises network.
✑ Use of virtual appliances in your Azure environment.
✑ In the scenarios above, you will have to create a route table and add user defined routes to it.
Reference:
https://github.com/uglide/azure-content/blob/master/articles/virtual-network/virtual-networks-udr-overview.md
HOTSPOT -
You have a network security group (NSG) bound to an Azure subnet.
You run Get-AzNetworkSecurityRuleConfig and receive the output shown in the following exhibit.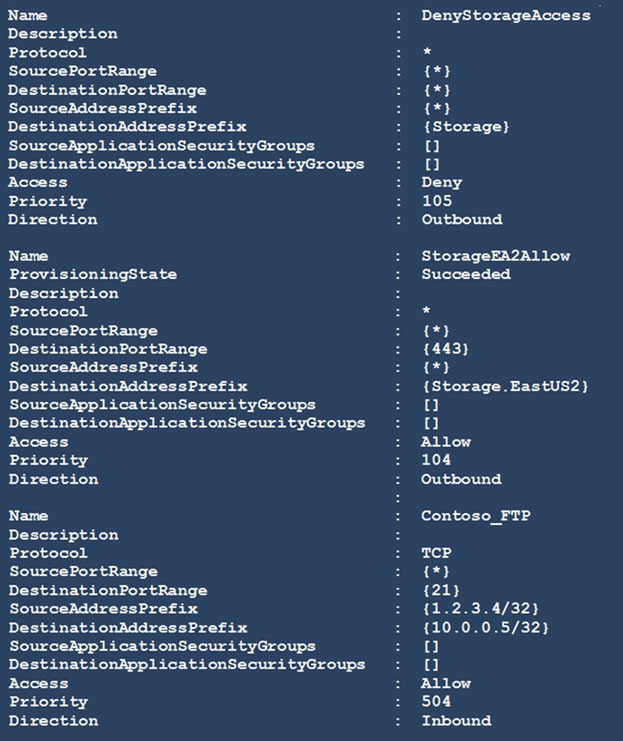
Use the drop-down menus to select the answer choice that completes each statement based on the information presented in the graphic.
NOTE: Each correct selection is worth one point.
Hot Area: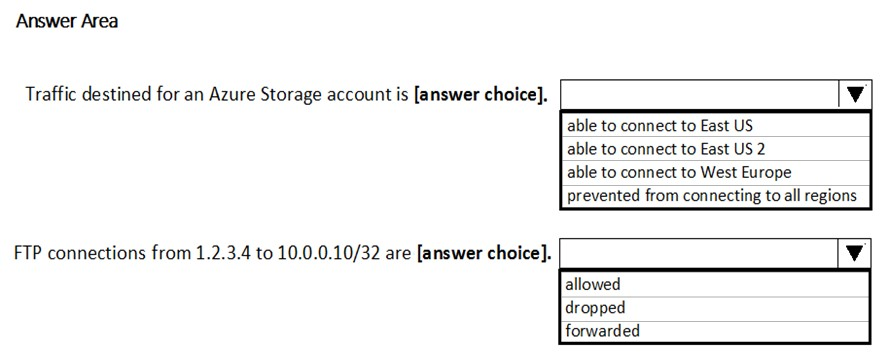
Answer:
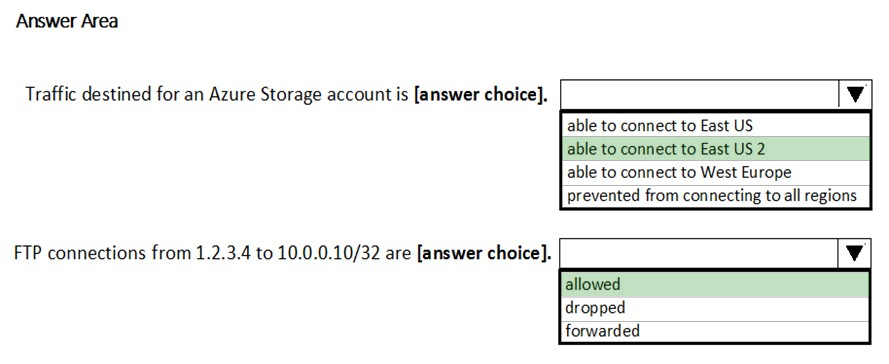
Box 1: able to connect to East US 2
The StorageEA2Allow has DestinationAddressPrefix {Storage/EastUS2}
Box 2: allowed -
TCP Port 21 controls the FTP session. Contoso_FTP has SourceAddressPrefix {1.2.3.4/32} and DestinationAddressPrefix {10.0.0.5/32}
Note:
The Get-AzureRmNetworkSecurityRuleConfig cmdlet gets a network security rule configuration for an Azure network security group.
Security rules in network security groups enable you to filter the type of network traffic that can flow in and out of virtual network subnets and network interfaces.
Reference:
https://docs.microsoft.com/en-us/azure/virtual-network/manage-network-security-group
You have an Azure subscription that contains the virtual networks shown in the following table.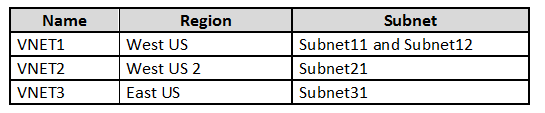
The subscription contains the virtual machines shown in the following table.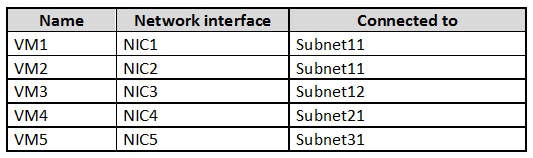
On NIC1, you configure an application security group named ASG1.
On which other network interfaces can you configure ASG1?
Answer:
C
Only network interfaces in NVET1, which consists of Subnet11 and Subnet12, can be configured in ASG1, as all network interfaces assigned to an application security group have to exist in the same virtual network that the first network interface assigned to the application security group is in.
Reference:
https://azure.microsoft.com/es-es/blog/applicationsecuritygroups/
You have 15 Azure virtual machines in a resource group named RG1.
All the virtual machines run identical applications.
You need to prevent unauthorized applications and malware from running on the virtual machines.
What should you do?
Answer:
B
Adaptive application control is an intelligent, automated end-to-end application whitelisting solution from Azure Security Center. It helps you control which applications can run on your Azure and non-Azure VMs (Windows and Linux), which, among other benefits, helps harden your VMs against malware. Security
Center uses machine learning to analyze the applications running on your VMs and helps you apply the specific whitelisting rules using this intelligence.
Reference:
https://docs.microsoft.com/en-us/azure/security-center/security-center-adaptive-application
You have a web app hosted on an on-premises server that is accessed by using a URL of https://www.contoso.com.
You plan to migrate the web app to Azure. You will continue to use https://www.contoso.com.
You need to enable HTTPS for the Azure web app.
What should you do first?
Answer:
B
Reference:
https://docs.microsoft.com/en-us/azure/app-service/configure-ssl-certificate#private-certificate-requirements
You plan to deploy Azure container instances.
You have a containerized application that is comprised of two containers: an application container and a validation container. The application container is monitored by the validation container. The validation container performs security checks by making requests to the application container and waiting for responses after every transaction.
You need to ensure that the application container and the validation container are scheduled to be deployed together. The containers must communicate to each other only on ports that are not externally exposed.
What should you include in the deployment?
Answer:
D
Azure Container Instances supports the deployment of multiple containers onto a single host using a container group. A container group is useful when building an application sidecar for logging, monitoring, or any other configuration where a service needs a second attached process.
Reference:
https://docs.microsoft.com/en-us/azure/container-instances/container-instances-container-groups
DRAG DROP -
You are configuring network connectivity for two Azure virtual networks named VNET1 and VNET2.
You need to implement VPN gateways for the virtual networks to meet the following requirements:
✑ VNET1 must have six site-to-site connections that use BGP.
✑ VNET2 must have 12 site-to-site connections that use BGP.
✑ Costs must be minimized.
Which VPN gateway SKU should you use for each virtual network? To answer, drag the appropriate SKUs to the correct networks. Each SKU may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.
Select and Place:
Answer:
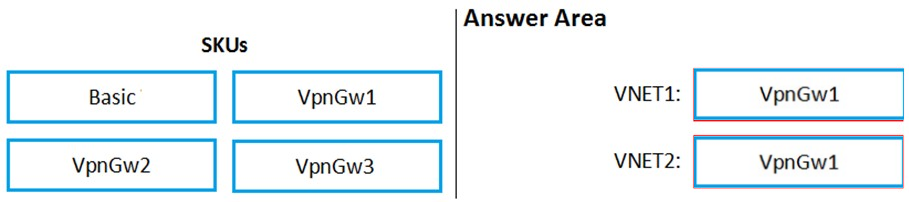
References:
https://docs.microsoft.com/en-us/azure/vpn-gateway/vpn-gateway-about-vpngateways#gwsku
You are securing access to the resources in an Azure subscription.
A new company policy states that all the Azure virtual machines in the subscription must use managed disks.
You need to prevent users from creating virtual machines that use unmanaged disks.
What should you use?
Answer:
B
HOTSPOT -
You have an Azure subscription that contains a storage account named storage1 and several virtual machines. The storage account and virtual machines are in the same Azure region. The network configurations of the virtual machines are shown in the following table.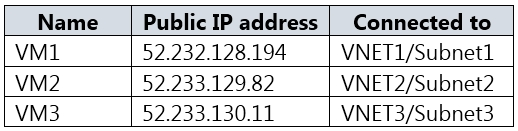
The virtual network subnets have service endpoints defined as shown in the following table.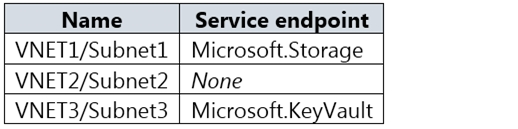
You configure the following Firewall and virtual networks settings for storage1:
✑ Allow access from: Selected networks
✑ Virtual networks: VNET3\Subnet3
Firewall `" Address range: 52.233.129.0/24
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area:
Answer:
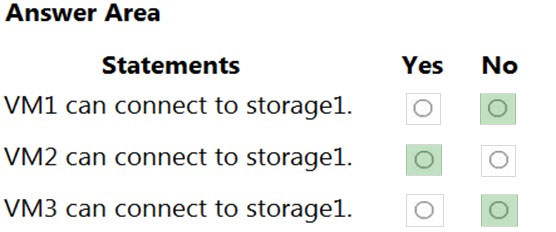
Box 1: No -
VNet1 has a service endpoint configure for Azure Storage. However, the Azure storage does not allow access from VNet1 or the public IP address of VM1.
Box 2: Yes -
VNet2 does not have a service endpoint configured. However, the Azure storage allows access from the public IP address of VM2.
Box 3: No -
Azure storage allows access from VNet3. However, VNet3 does not have a service endpoint for Azure storage. The Azure storage also does not allow access from the public IP of VM3.
You plan to create an Azure Kubernetes Service (AKS) cluster in an Azure subscription.
The manifest of the registered server application is shown in the following exhibit.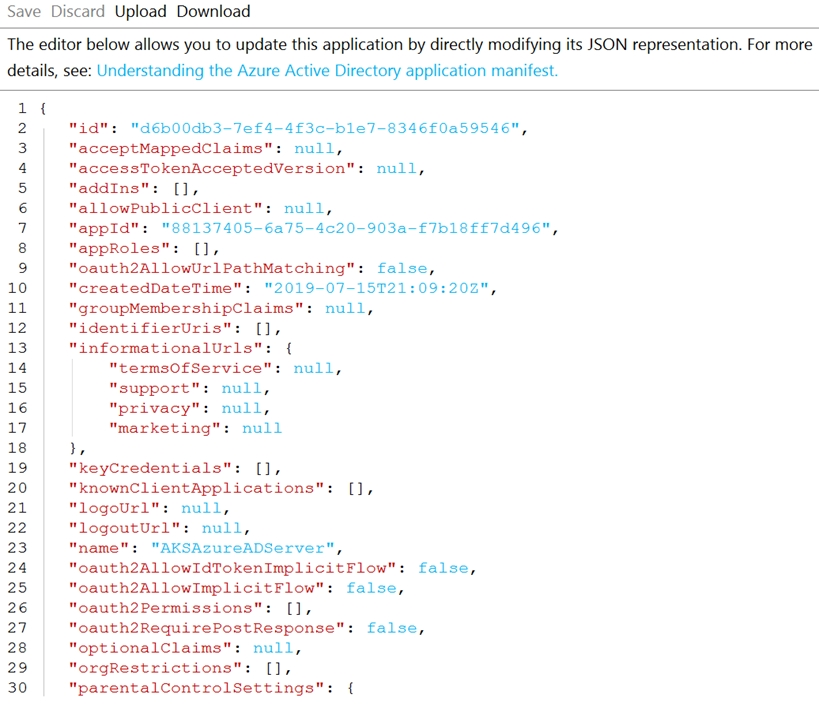
You need to ensure that the AKS cluster and Azure Active Directory (Azure AD) are integrated.
Which property should you modify in the manifest?
Answer:
C
Reference:
https://docs.microsoft.com/en-us/azure/aks/azure-ad-integration-cli https://www.codeproject.com/Articles/3211864/Operation-and-Maintenance-of-AKS-Applications