DRAG DROP -
You have an Azure subscription that uses Azure Monitor and contains a Log Analytics workspace.
You have an encryption key.
You need to configure Azure Monitor to use the key to encrypt log data.
Which five actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.
NOTE: More than one order of answer choices is correct. You will receive credit for any of the correct orders you select.
Select and Place: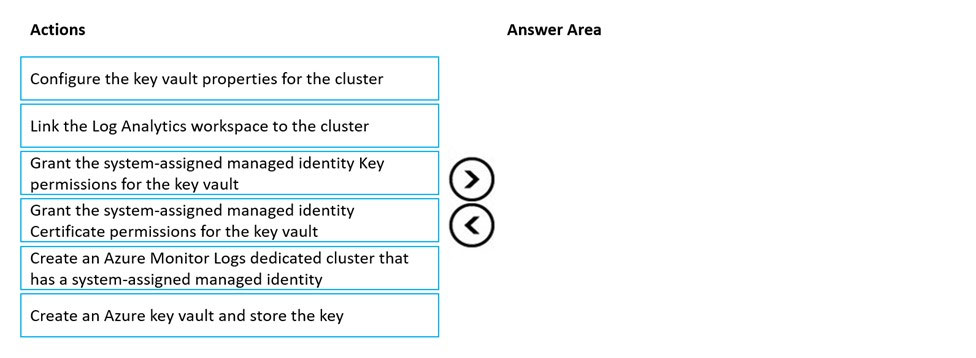
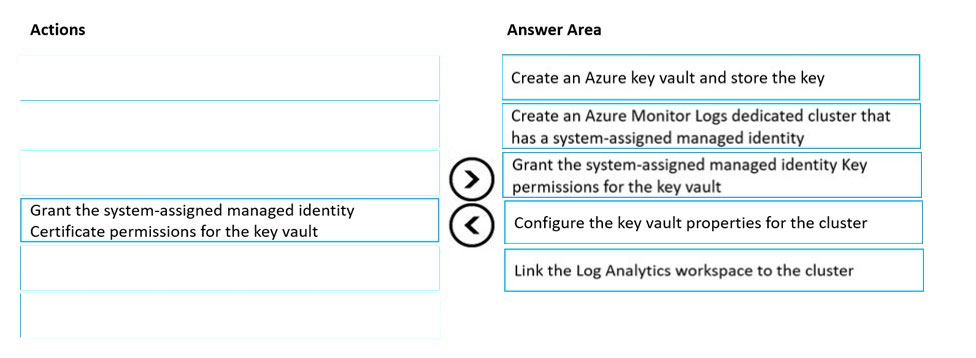
Answer:
Customer-Managed key provisioning steps:
Step 1: Create an Azure Key vault and store the key.
Creating Azure Key Vault and storing key. Create or use an existing Azure Key Vault in the region that the cluster is planed, and generate or import a key to be used for logs encryption.
Step 2: Create an Azure Monitor Logs dedicate cluster that has a system-assigned managed identity
Clusters uses managed identity for data encryption with your Key Vault. Configure identity type property to SystemAssigned when creating your cluster to allow access to your Key Vault for "wrap" and "unwrap" operations.
Step 3: Grant the system-assigned managed Identity Key permissions for the key vault.
Grant Key Vault permissions.
Create Access Policy in Key Vault to grants permissions to your cluster. These permissions are used by the underlay cluster storage. Open your Key Vault in
Azure portal and click Access Policies then + Add Access Policy to create a policy with these settings:
Key permissionsג€"select Get, Wrap Key and Unwrap Key.
Etc.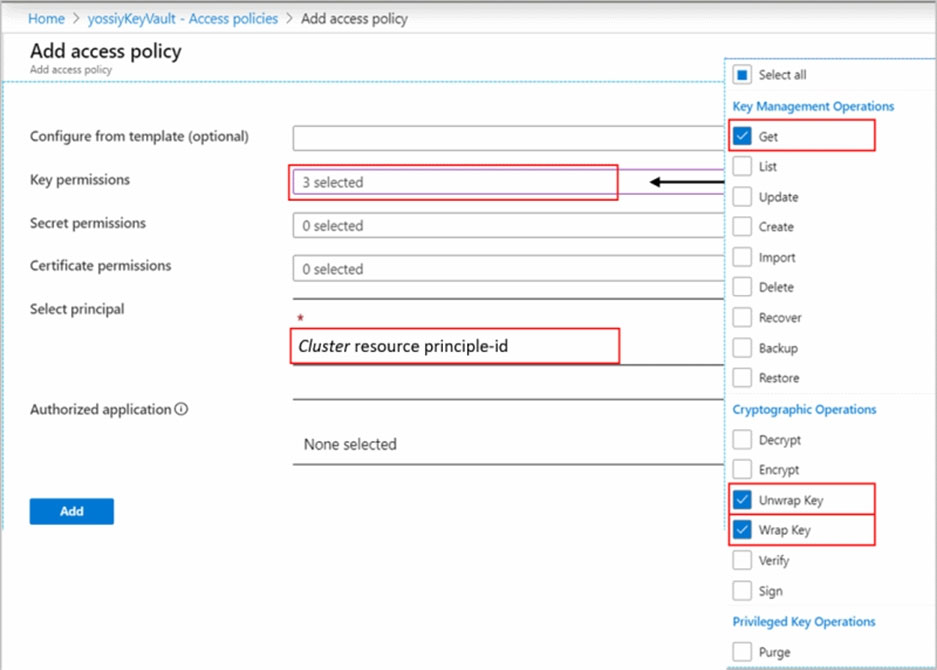
1. Creating cluster
2. Granting permissions to your Key Vault
3. Updating cluster with key identifier details
4. Linking workspaces
Step 4: Configure the key vault properties for the cluster.
Update cluster with key identifier details.
Step 5: Link the Log Analytics workspace to the cluster
Link workspace to cluster.
This step should be performed only after the cluster provisioning. If you link workspaces and ingest data prior to the provisioning, ingested data will be dropped and won't be recoverable.
Reference:
https://docs.microsoft.com/en-us/azure/azure-monitor/logs/customer-managed-keys
DRAG DROP -
You have an Azure Key Vault that contains an encryption key named key1.
You plan to create a Log Analytics workspace that will store logging data.
You need to encrypt the workspace by using key1.
Which four actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.
Select and Place: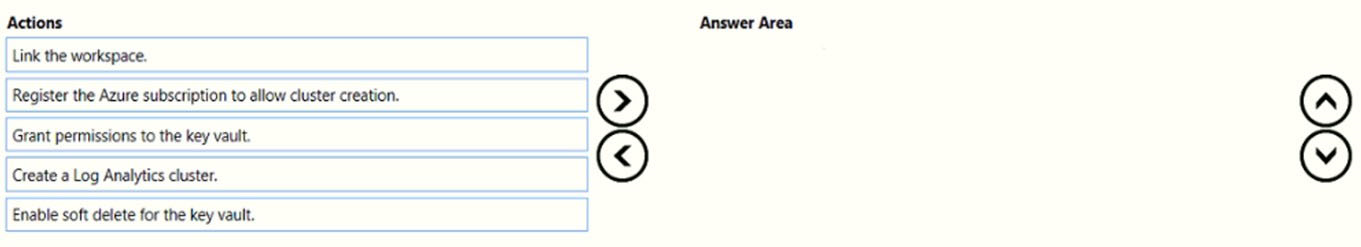
Answer:
Customer-Managed key provisioning steps (assuming there already is an Azure Key Vault):
Step 1: Enable soft delete for the key vault.
The Azure Key Vault must be configured as recoverable, to protect your key and the access to your data in Azure Monitor. You can verify this configuration under properties in your Key Vault, both Soft delete and Purge protection should be enabled.
Step 2: Create a Log Analytics cluster.
Clusters uses managed identity for data encryption with your Key Vault. Configure identity type property to SystemAssigned when creating your cluster to allow access to your Key Vault for "wrap" and "unwrap" operations.
Step 3: Grant permissions to the key vault.
Grant Key Vault permissions.
Create Access Policy in Key Vault to grants permissions to your cluster. These permissions are used by the underlay cluster storage. Open your Key Vault in
Azure portal and click Access Policies then + Add Access Policy to create a policy with these settings:
Key permissionsג€"select Get, Wrap Key and Unwrap Key.
Etc.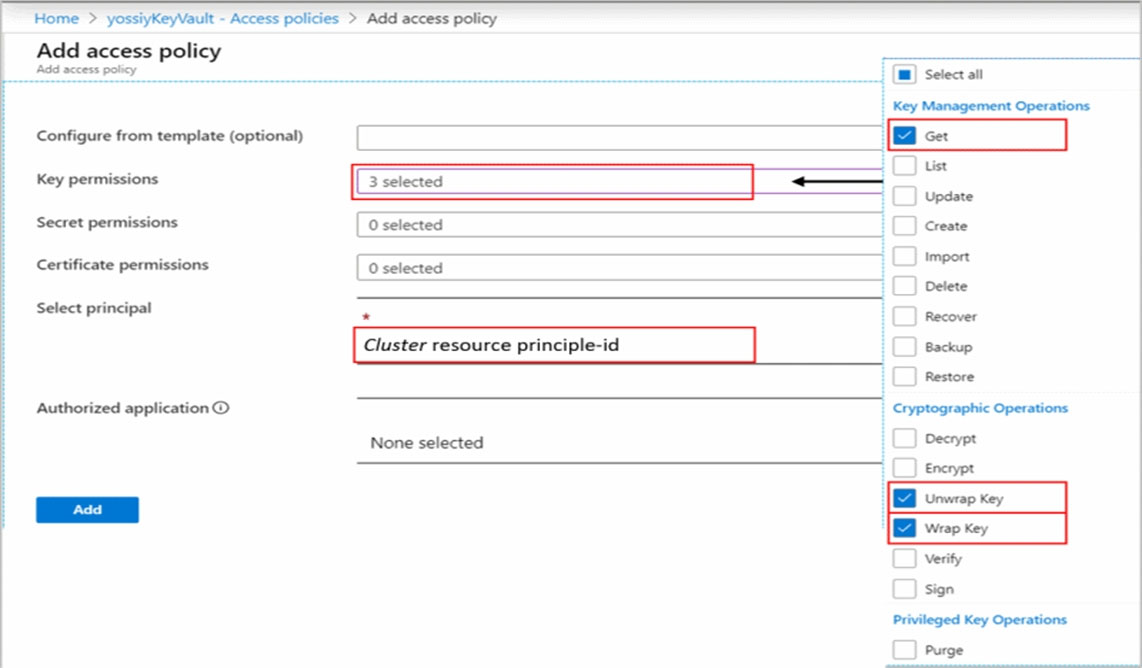
1. Creating cluster
2. Granting permissions to your Key Vault
3. Updating cluster with key identifier details
4. Linking workspaces
Step 4: Link workspace -
Link workspace to cluster.
This step should be performed only after the cluster provisioning. If you link workspaces and ingest data prior to the provisioning, ingested data will be dropped and won't be recoverable.
Reference:
https://docs.microsoft.com/en-us/azure/azure-monitor/logs/customer-managed-keys
You use release pipelines in Azure Pipelines to deploy an app. Secrets required be the pipeline are stored as pipeline variables. Logging of commands is enabled for the Azure Pipelines agent.
You need to prevent the values of the secrets from being logged.
What should you do?
Answer:
A
Don't set secret variables in your YAML file. Operating systems often log commands for the processes that they run, and you wouldn't want the log to include a secret that you passed in as an input. Use the script's environment or map the variable within the variables block to pass secrets to your pipeline.
Incorrect Answers:
B: Never pass secrets on the command line.
C: Adding a prefix does not make the variable a secret. The issecret property makes it secret but does not prevent logging of the secret.
D: Never echo secrets as output.
Reference:
https://docs.microsoft.com/en-us/azure/devops/pipelines/process/variables?view=azure-devops&tabs=yaml%2Cbatch https://docs.microsoft.com/en-us/azure/devops/pipelines/scripts/logging-commands?view=azure-devops&tabs=bash
DRAG DROP -
You need to deploy a new project in Azure DevOps that has the following requirements:
* The lead developer must be able to create repositories, manage permissions, manage policies, and contribute to the repository.
* Developers must be able to contribute to the repository and create branches, but NOT bypass policies when pushing builds.
* Project managers must only be able to view the repository.
* The principle of least privilege must be used.
You create a new Azure DevOps project team for each role.
To which Azure DevOps groups should you add each team? To answer, drag the appropriate groups to the correct teams. Each group may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.
Select and Place:
Answer:

Box 1: Readers -
Project managers must only be able to view the repository.
Only read permission necessary.
Box 2: Project Administrators -
The lead developer must be able to create repositories, manage permissions, manage policies, and contribute to the repository.
Add to the Project Collection Administrators security group users tasked with managing organization or collection resources.
Box 3: Contributors -
Developers must be able to contribute to the repository and create branches, but NOT bypass policies when pushing builds.
Add to the Contributors security group full-time workers who contribute to the code base or manage projects.
Reference:
https://docs.microsoft.com/en-us/azure/devops/organizations/security/look-up-project-collection-administrators
DRAG DROP -
You have an Azure subscription that contains a project in Azure DevOps named Project1. You have three Azure Active Directory (Azure AD) users that require access to Project1 as shown in the following table.
You need to ensure that the users have the appropriate permissions. The solution must use the principle of least privilege.
To which permission group in Azure DevOps should you add each user? To answer, drag the appropriate permission groups to the correct users. Each permission group may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.
Answer:

You have an Azure subscription linked to an Azure Active Directory Premium Plan 1 tenant.
A security review indicates that too many users have privileged access to resources.
You need to deploy a privileged access management solution that meets the following requirements:
• Enforces time limits on the use of privileged access
• Requires approval to activate privileged access
• Minimizes costs
What should you do first?
Answer:
D
You plan to create a GitHub workflow that will use GitHub Actions. The actions will require a 256-KB secret.
You need to recommend a solution to store and encrypt the secret. The secret value must be accessible only to the workflow. The solution must minimize administrative effort
What should you recommend?
Answer:
C
You have a GitHub Enterprise account.
You need to enable push protection for secret scanning of the account repositories.
What should you do first?
Answer:
A
DRAG DROP -
Your company has a project in Azure DevOps named Project1.
All the developers at the company have Windows 10 devices.
You need to create a Git repository for Project1. The solution must meet the following requirements:
• Support large binary files.
• Store binary files outside of the repository.
• Use a standard Git workflow to maintain the metadata of the binary files by using commits to the repository.
Which three actions should you perform in sequence on each developer’s device? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.
Answer:

You are designing the development process for your company.
You need to recommend a solution for continuous inspection of the company's code base to locate common code patterns that are known to be problematic.
What should you include in the recommendation?
Answer:
C
SonarCloud is a cloud service offered by SonarSource and based on SonarQube. SonarQube is a widely adopted open source platform to inspect continuously the quality of source code and detect bugs, vulnerabilities and code smells in more than 20 different languages.
Note: The SonarCloud Azure DevOps extension brings everything you need to have your projects analyzed on SonarCloud very quickly.
Incorrect Answers:
A: Test plans are used to group together test suites and individual test cases. This includes static test suites, requirement-based suites, and query-based suites.
Reference:
https://docs.travis-ci.com/user/sonarcloud/
https://sonarcloud.io/documentation/integrations/vsts/