You have an Azure Active Directory (Azure AD) tenant named contoso.com that contains several administrative user accounts.
You need to recommend a solution to identify which administrative user accounts have NOT signed in during the previous 30 days.
Which service should you include in the recommendation?
Answer:
A
A company deploys Azure Active Directory (Azure AD) Connect to synchronize identity information from their on-premises Active Directory Domain Services (AD
DS) directory to their Azure AD tenant. The identity information that is synchronized includes user accounts, credential hashes for authentication (password sync), and group memberships. The company plans to deploy several Windows and Linux virtual machines (VMs) to support their applications.
The VMs have the following requirements:
✑ Support domain join, LDAP read, LDAP bind, NTLM and Kerberos authentication, and Group Policy.
✑ Allow users to sign in to the domain using their corporate credentials and connect remotely to the VM by using Remote Desktop.
You need to support the VM deployment.
Which service should you use?
Answer:
D
Azure AD Domain Services provides managed domain services such as domain join, group policy, LDAP, Kerberos/NTLM authentication that are fully compatible with Windows Server Active Directory.
Reference:
https://docs.microsoft.com/en-us/azure/active-directory-domain-services/active-directory-ds-overview
HOTSPOT -
You are designing a software as a service (SaaS) application that will enable Azure Active Directory (Azure AD) users to create and publish online surveys. The
SaaS application will have a front-end web app and a back-end web API. The web app will rely on the web API to handle updates to customer surveys.
You need to design an authorization flow for the SaaS application. The solution must meet the following requirements:
✑ To access the back-end web API, the web app must authenticate by using OAuth 2 bearer tokens.
✑ The web app must authenticate by using the identities of individual users.
What should you include in the solution? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area: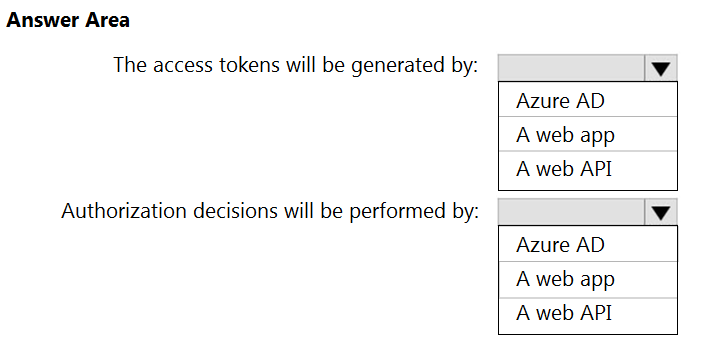
Answer:

Reference:
https://docs.microsoft.com/lb-lu/azure/architecture/multitenant-identity/web-api https://docs.microsoft.com/en-us/azure/active-directory/develop/quickstart-v1-dotnet-webapi
You have a hybrid deployment of Azure Active Directory (Azure AD).
You need to recommend a solution to ensure that the Azure AD tenant can be managed only from the computers on your on-premises network.
What should you include in the recommendation?
Answer:
A
You plan to automate the deployment of resources to Azure subscriptions.
What is a difference between using Azure Blueprints and Azure Resource Manager templates?
Answer:
C
With Azure Blueprints, the relationship between the blueprint definition (what should be deployed) and the blueprint assignment (what was deployed) is preserved.
This connection supports improved tracking and auditing of deployments. Azure Blueprints can also upgrade several subscriptions at once that are governed by the same blueprint.
Incorrect:
Not A: Nearly everything that you want to include for deployment in Azure Blueprints can be accomplished with a Resource Manager template. However, a
Resource Manager template is a document that doesn't exist natively in Azure ג€" each is stored either locally or in source control. The template gets used for deployments of one or more Azure resources, but once those resources deploy there's no active connection or relationship to the template.
Reference:
https://docs.microsoft.com/en-us/answers/questions/26851/how-is-azure-blue-prints-different-from-resource-m.html
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have an Azure Active Directory (Azure AD) tenant named contoso.com. The tenant contains a group named Group1. Group1 contains all the administrative user accounts.
You discover several login attempts to the Azure portal from countries where administrative users do NOT work.
You need to ensure that all login attempts to the Azure portal from those countries require Azure Multi-Factor Authentication (MFA).
Solution: Implement Azure AD Privileged Identity Management.
Does this solution meet the goal?
Answer:
A
Azure Active Directory (Azure AD) Privileged Identity Management (PIM) is a service that enables you to manage, control, and monitor access to important resources in your organization.
Reference:
https://docs.microsoft.com/en-us/azure/active-directory/privileged-identity-management/pim-configure
You manage an Azure environment for a company. The environment has over 25,000 licensed users and 100 mission-critical applications.
You need to recommend a solution that provides advanced user threat detection and remediation strategies.
What should you recommend?
Answer:
C
Reference:
https://docs.microsoft.com/en-us/azure/security/fundamentals/threat-detection
You store web access logs data in Azure Blob storage.
You plan to generate monthly reports from the access logs.
You need to recommend an automated process to upload the data to Azure SQL Database every month.
What should you include in the recommendation?
Answer:
C
Azure Data Factory is the platform that solves such data scenarios. It is the cloud-based ETL and data integration service that allows you to create data-driven workflows for orchestrating data movement and transforming data at scale. Using Azure Data Factory, you can create and schedule data-driven workflows (called pipelines) that can ingest data from disparate data stores. You can build complex ETL processes that transform data visually with data flows or by using compute services such as Azure HDInsight Hadoop, Azure Databricks, and Azure SQL Database.
Reference:
https://docs.microsoft.com/en-gb/azure/data-factory/introduction
HOTSPOT -
You have a resource group named RG1 that contains the objects shown in the following table.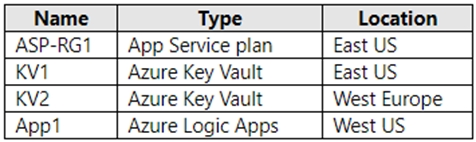
You need to configure permissions so that App1 can copy all the secrets from KV1 to KV2. App1 currently has the Get permission for the secrets in KV1.
Which additional permissions should you assign to App1? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area: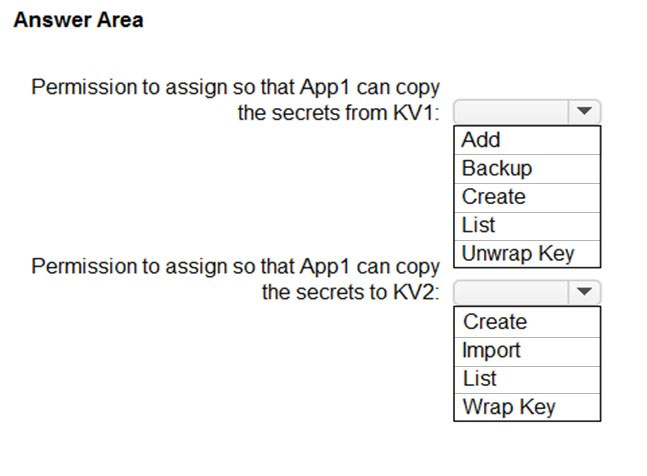
Answer:

Box 1: List -
Get: Gets the specified Azure key vault.
List: The List operation gets information about the vaults associated with the subscription.
Box 2: Create -
Create Or Update: Create or update a key vault in the specified subscription.
Reference:
https://docs.microsoft.com/en-us/rest/api/keyvault/
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
Your company has deployed several virtual machines (VMs) on-premises and to Azure. Azure ExpressRoute has been deployed and configured for on-premises to Azure connectivity.
Several VMs are exhibiting network connectivity issues.
You need to analyze the network traffic to determine whether packets are being allowed or denied to the VMs.
Solution: Install and configure the Microsoft Monitoring Agent and the Dependency Agent on all VMs. Use the Wire Data solution in Azure Monitor to analyze the network traffic.
Does the solution meet the goal?
Answer:
B
Instead use Azure Network Watcher to run IP flow verify to analyze the network traffic.
Note: Wire Data looks at network data at the application level, not down at the TCP transport layer. The solution doesn't look at individual ACKs and SYNs.
Reference:
https://docs.microsoft.com/en-us/azure/network-watcher/network-watcher-monitoring-overview https://docs.microsoft.com/en-us/azure/network-watcher/network-watcher-ip-flow-verify-overview