You are designing an Azure web app that will use Azure Active Directory (Azure AD) for authentication.
You need to recommend a solution to provide users from multiple Azure AD tenants with access to App1. The solution must ensure that the users use Azure Multi-
Factor Authentication (MFA) when they connect to App1.
Which two types of objects should you include in the recommendation? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
Answer:
AF
A: The Conditional Access feature in Azure Active Directory (Azure AD) offers one of several ways that you can use to secure your app and protect a service.
Conditional Access enables developers and enterprise customers to protect services in a multitude of ways including:
✑ Multi-factor authentication
✑ Allowing only Intune enrolled devices to access specific services
✑ Restricting user locations and IP ranges
Conditional Access policies are powerful tools, we recommend excluding the following accounts from your policy:
✑ Service accounts and service principals.
If your organization has these accounts in use in scripts or code, consider replacing them with managed identities.
Incorrect Answers:
B: Managed Identity does not support cross-directory scenarios.
E: Application security groups enable you to configure network security as a natural extension of an application's structure, allowing you to group virtual machines and define network security policies based on those groups.
Note: The correct options should be application registration with Azure, this will allow the authentication of users on the AD to access the application. A default application registration validates that the user has valid login credentials. This can be your Active Directory or in case of a multi-tenant application the directory where the user is originated from.
Reference:
https://docs.microsoft.com/en-us/azure/active-directory/develop/v2-conditional-access-dev-guide https://docs.microsoft.com/en-us/azure/active-directory/conditional-access/howto-conditional-access-policy-azure-management https://www.re-mark-able.net/understanding-azure-active-directory-application-registrations/
You need to create an Azure Storage account that uses a custom encryption key.
What do you need to implement the encryption?
Answer:
A
You can use your own encryption key to protect the data in your storage account. When you specify a customer-managed key, that key is used to protect and control access to the key that encrypts your data.
You must use either Azure Key Vault or Azure Key Vault Managed Hardware Security Model (HSM) (preview) to store your customer-managed keys.
HOTSPOT -
You plan to create an Azure environment that will have a root management group and five child management groups. Each child management group will contain five Azure subscriptions. You plan to have between 10 and 30 resource groups in each subscription.
You need to design a solution for the planned environment. The solution must meet the following requirements:
Prevent users who are assigned the Owner role for the subscriptions from deleting the resource groups from their respective subscription.
✑ Ensure that you can update RBAC role assignments across all the subscriptions and resource groups.
✑ Minimize administrative effort.
What should you include in the solution? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area: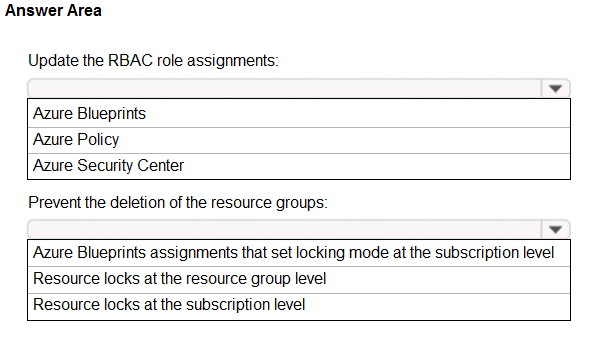
Answer:
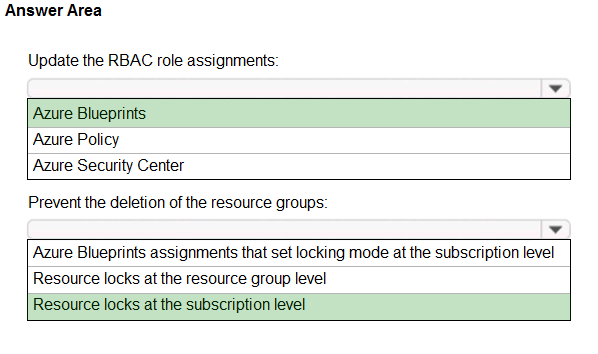
Box 1: Azure Blueprints -
Blueprints are a declarative way to orchestrate the deployment of various resource templates and other artifacts such as:
Role Assignments -
Policy Assignments -
Azure Resource Manager templates (ARM templates)
Resource Groups -
Incorrect:
A policy is a default allow and explicit deny system focused on resource properties during deployment and for already existing resources.
Box 2: Resource locks at the subscription level
To minimize administrative effort lock at the subscription level.
Note: As an administrator, you can lock a subscription, resource group, or resource to prevent other users in your organization from accidentally deleting or modifying critical resources.
Reference:
https://docs.microsoft.com/en-us/azure/governance/blueprints/overview https://docs.microsoft.com/en-us/azure/azure-resource-manager/management/lock-resources
Your company has the divisions shown in the following table.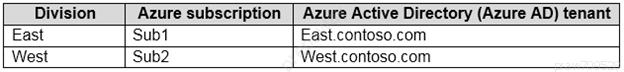
Sub1 contains an Azure web app that runs an ASP.NET application named App1. App1 uses the Microsoft identity platform (v2.0) to handle user authentication.
Users from east.contoso.com can authenticate to App1.
You need to recommend a solution to allow users from west.contoso.com to authenticate to App1.
What should you recommend for the west.contoso.com Azure AD tenant?
Answer:
D
There are several components that make up the Microsoft identity platform:
✑ OAuth 2.0 and OpenID Connect standard-compliant authentication service
Application management portal: A registration and configuration experience in the Azure portal, along with the other Azure management capabilities.
You register an application using the App registrations experience in the Azure portal so that your app can be integrated with the Microsoft identity platform and call Microsoft Graph.
Reference:
https://docs.microsoft.com/en-us/azure/active-directory/develop/v2-overview https://docs.microsoft.com/en-us/graph/auth-register-app-v2
You have an Azure Active Directory (Azure AD) tenant named contoso.com that has a security group named Group1. Group1 is configured for assigned membership. Group1 has 50 members, including 20 guest users.
You need to recommend a solution for evaluating the membership of Group1. The solution must meet the following requirements:
✑ The evaluation must be repeated automatically every three months.
✑ Every member must be able to report whether they need to be in Group1.
✑ Users who report that they do not need to be in Group1 must be removed from Group1 automatically.
✑ Users who do not report whether they need to be in Group1 must be removed from Group1 automatically.
What should you include in the recommendation?
Answer:
A
In Azure Active Directory (Azure AD), you can create complex attribute-based rules to enable dynamic memberships for groups. Dynamic group membership reduces the administrative overhead of adding and removing users.
When any attributes of a user or device change, the system evaluates all dynamic group rules in a directory to see if the change would trigger any group adds or removes. If a user or device satisfies a rule on a group, they are added as a member of that group. If they no longer satisfy the rule, they are removed.
Reference:
https://docs.microsoft.com/en-us/azure/active-directory/users-groups-roles/groups-dynamic-membership
Your company purchases an app named App1.
You need to recommend a solution to ensure that App1 can read and modify access reviews.
What should you recommend?
Answer:
B
The app must be registered. You can register the application in the Azure Active Directory admin center.
The Azure AD access reviews feature has an API in the Microsoft Graph endpoint.
You can register an Azure AD application and set it up for permissions to call the access reviews API in Graph.
Reference:
https://docs.microsoft.com/en-us/azure/active-directory/develop/quickstart-register-app
You have 200 resource groups across 20 Azure subscriptions.
Your company's security policy states that the security administrator must verify all assignments of the Owner role for the subscriptions and resource groups once a month. All assignments that are not approved by the security administrator must be removed automatically. The security administrator must be prompted every month to perform the verification.
What should you use to implement the security policy?
Answer:
B
Azure Active Directory (Azure AD) access reviews enable organizations to efficiently manage group memberships, access to enterprise applications, and role assignments. User's access can be reviewed on a regular basis to make sure only the right people have continued access.
Reference:
https://docs.microsoft.com/en-us/azure/active-directory/governance/access-reviews-overview
HOTSPOT -
Your company has 20 web APIs that were developed in-house.
The company is developing 10 web apps that will use the web APIs. The web apps and the APIs are registered in the company's Azure Active Directory (Azure
AD) tenant. The web APIs are published by using Azure API Management.
You need to recommend a solution to block unauthorized requests originating from the web apps from reaching the web APIs. The solution must meet the following requirements:
✑ Use Azure AD-generated claims.
✑ Minimize configuration and management effort.
What should you include in the recommendation? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area: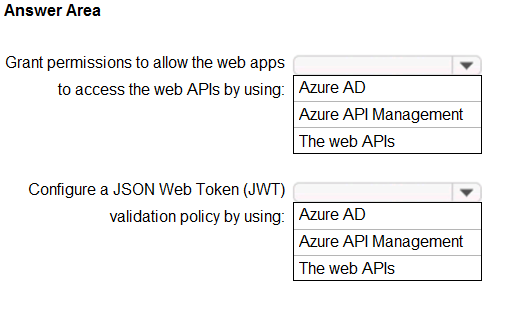
Answer:
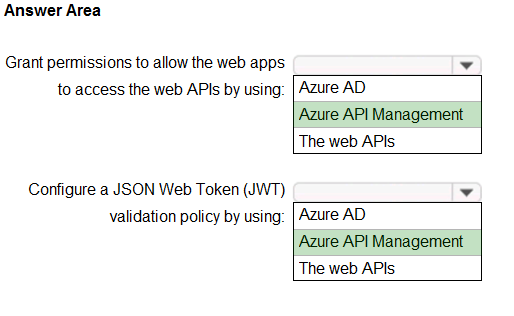
HOTSPOT -
You need to design a resource governance solution for an Azure subscription. The solution must meet the following requirements:
✑ Ensure that all ExpressRoute resources are created in a resource group named RG1.
✑ Delegate the creation of the ExpressRoute resources to an Azure Active Directory (Azure AD) group named Networking.
✑ Use the principle of least privilege.
What should you include in the solution? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area: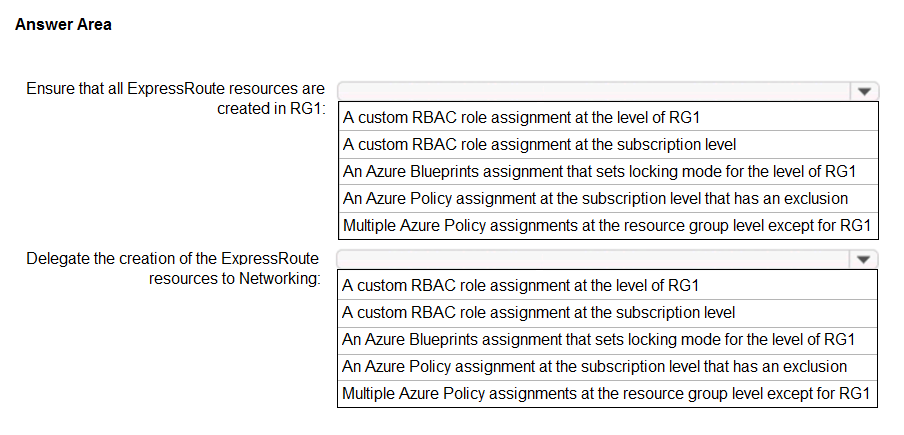
Answer:
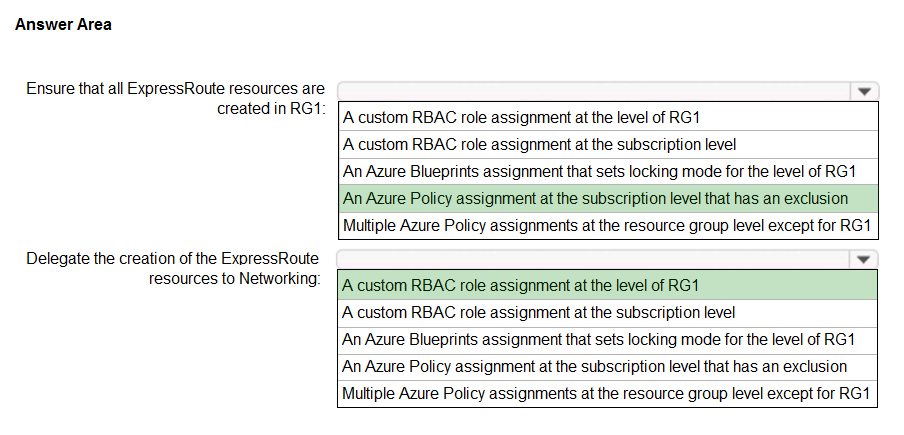
Box 1: An Azure policy assignment at the subscription level that has an exclusion
Box 2: A custom RBAC role assignment at the level of RG1
Azure role-based access control (Azure RBAC) is the authorization system you use to manage access to Azure resources. To grant access, you assign roles to users, groups, service principals, or managed identities at a particular scope.
Reference:
https://docs.microsoft.com/en-us/azure/governance/policy/tutorials/create-and-manage
You have an Azure Active Directory (Azure AD) tenant and Windows 10 devices.
You configure a conditional access policy as shown in the exhibit. (Click the Exhibit tab.)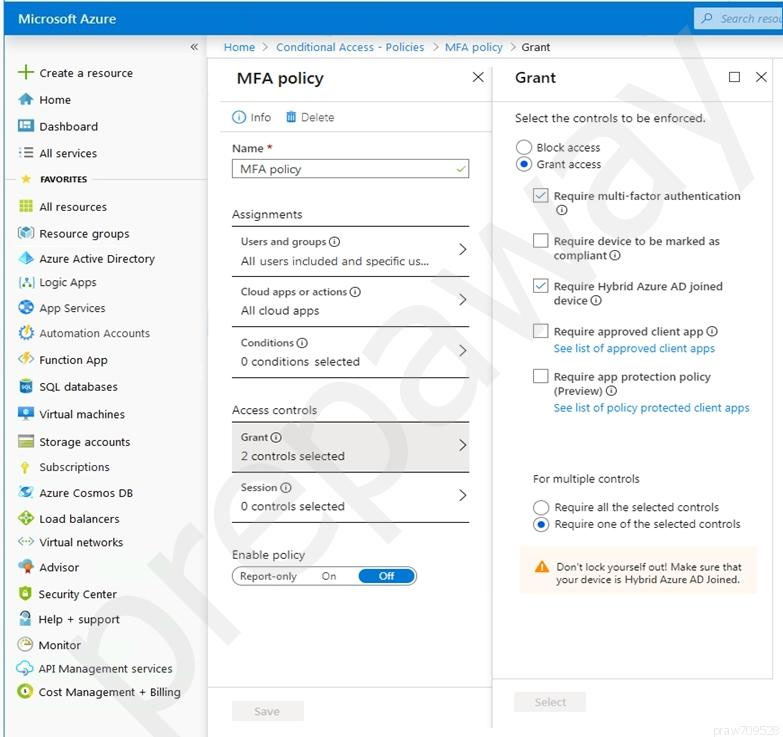
What is the result of the policy?
Answer:
B
Either the device should be joined to Azure AD or MFA must be used.