Company XYZ asks for design recommendations for Layer 2 redundancy. The company wants to prioritize fast convergence and resiliency elements in the design.
Which two technologies are recommended? (Choose two.)
BE
Company XYZ has a hub-and-spoke topology over an SP-managed infrastructure. To measure traffic performance metrics, they implemented IP SLA senders on all spoke CE routers and an IP SLA responder on the hub CE router. What must they monitor to have visibility on the potential performance impact due to the constantly increasing number of spoke sites?
C
Which two application requirements are mandatory for traffic to receive proper treatment when placed in the priority queue? (Choose two.)
AB
Company XYZ is redesigning their QoS policy. Some of the applications used by the company are real-time applications. The QoS design must give these applications preference in terms of transmission. Which QoS strategy can be used to fulfill the requirement?
D
According to the CIA triad principles for network security design, which principle should be priority for a Zero Trust network?
A
Company XYZ wants to secure the data plane of their network. Which two technologies can be included in the security design? (Choose two.)
CD
Reference:
https://www.ciscopress.com/articles/article.asp?p=2928193&seqNum=4
A healthcare provider discovers that protected health information of patients was altered without patient consent. The healthcare provider is subject to HIPAA compliance and is required to protect PHI data. Which type of security safeguard should be implemented to resolve this issue?
D
Which three items do you recommend for control plane hardening of an infrastructure device? (Choose three.)
BCF
Reference:
https://www.cisco.com/c/en/us/support/docs/ip/access-lists/13608-21.html#anc54
What is a characteristic of a secure cloud architecture model?
A
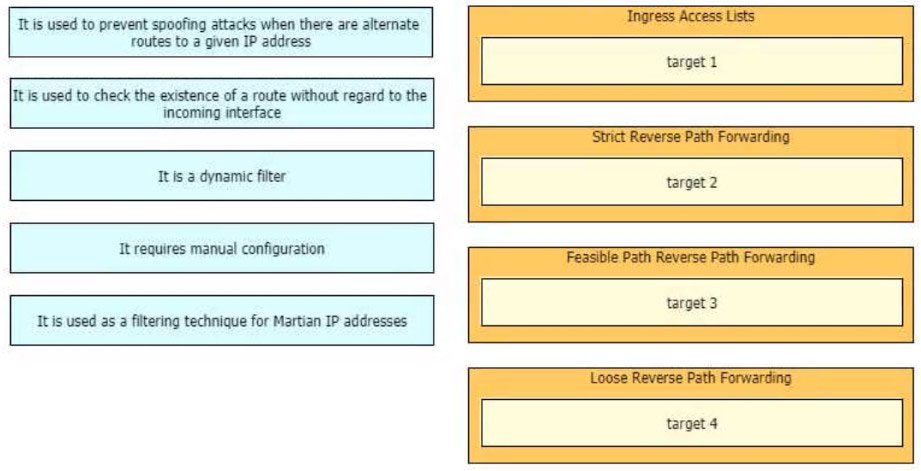
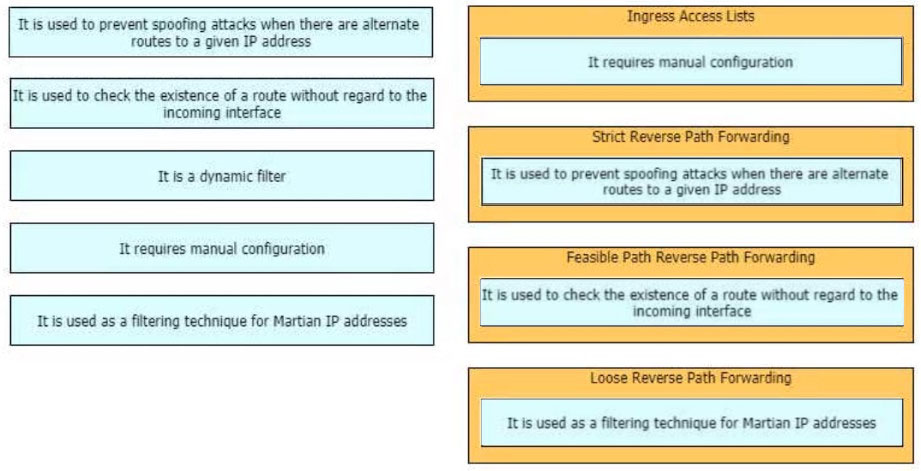
DRAG DROP -
Drag and drop the design characteristics from the left onto the correct network filter techniques on the right. Not all options are used.
Select and Place: