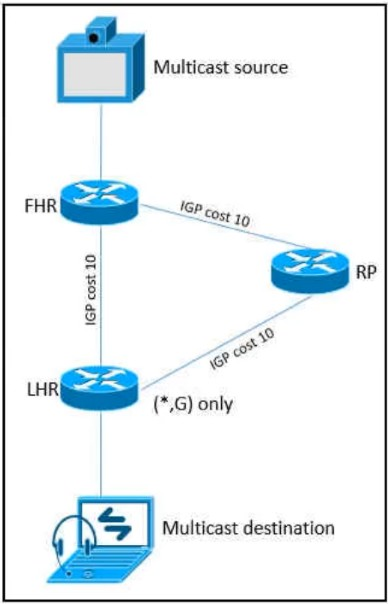
Refer to the exhibit. As part of a redesign project, you must predict multicast behavior. What happens to the multicast traffic received on the shared tree (*, G), if it is received on the LHR interface indicated?
B
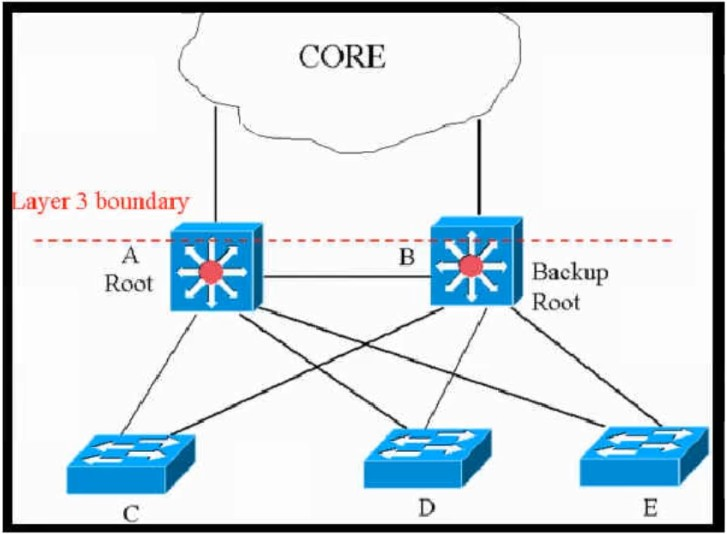
Refer to the exhibit. This network is running legacy STP 802.1d. Assuming "hello_timer" is fixed to 2 seconds, which parameters can be modified to speed up convergence times after single link/node failure?
B
Reference:
https://www.cisco.com/c/en/us/support/docs/lan-switching/spanning-tree-protocol/19120-122.html
Company XYZ is running a redundant private WAN network using OSPF as the underlay protocol. The current design accommodates for redundancy in the network, but it is taking over 30 seconds for the network to reconverge upon failure. Which technique can be implemented in the design to detect such a failure in a subsecond?
E
Which three elements help network designers to construct secure systems that protect information and resources (such as devices, communication, and data) from unauthorized access, modification, inspection, or destruction? (Choose three.)
BDE
Which relationship between iBGP and the underlying physical topology is true?
A
Which two statements describe the hierarchical LAN design model? (Choose two.)
AC
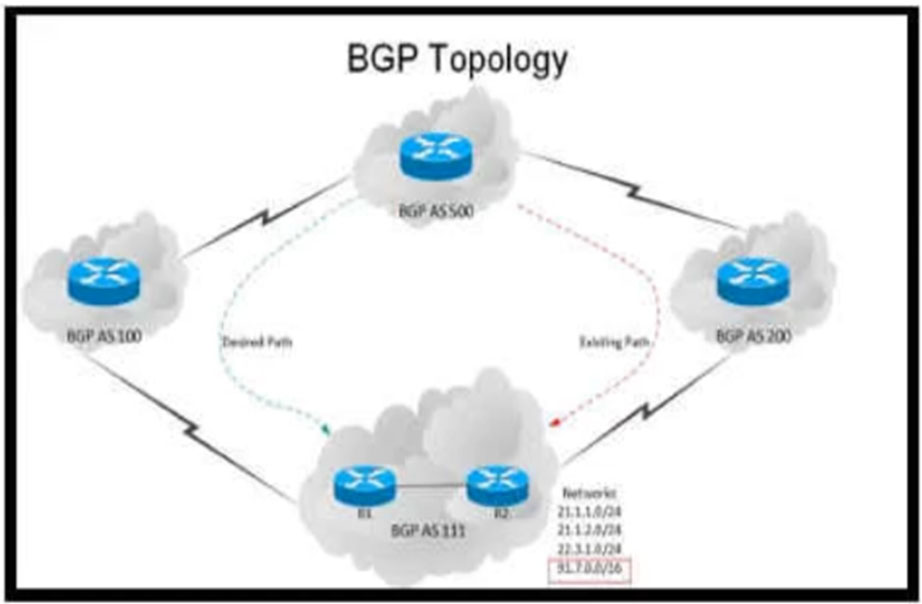
Refer to the exhibit. An engineer has been asked to redesign the traffic flow toward AS 111 coming from AS 500. Traffic destined to AS 111 network 91.7.0.0/16 should come in via AS 100, while traffic destined to all other networks in AS 111 should continue to use the existing path. Which BGP attributes are best suited to control this inbound traffic coming from BGP AS 500 into the 91.7.0.0/16 network?
B
An enterprise that runs numerous proprietary applications has major issues with its on-premises server estate hardware, to the point where business-critical functions are compromised. The enterprise accelerates plans to migrate services to the cloud. Which cloud service should be used if the enterprise wants to avoid hardware issues yet have control of its applications and operating system?
C
How must the queue sizes be designed to ensure that an application functions correctly?
D
An enterprise requires MPLS connected branches to access cloud-based Microsoft 365 services over an SD-WAN solution. Internet access is available only at dual regional hub sites that are connected to the MPLS network. Which connectivity method provides an optimum access method to the cloud-based services if one ISP suffers loss or latency?
C
Reference:
https://www.cisco.com/c/en/us/solutions/collateral/enterprise-networks/sd-wan/white_paper-c11-741353.html