An engineer is configuring their router to send NetfFow data to Stealthwatch which has an IP address of 1.1.1.1 using the flow record Stealthwatch406143794 command. Which additional command is required to complete the flow record?
C
Reference:
https://www.cisco.com/c/dam/en/us/td/docs/security/stealthwatch/netflow/config-trouble-netflow-stealth.pdf
An engineer is adding a Cisco DUO solution to the current TACACS+ deployment using Cisco ISE. The engineer wants to authenticate users using their account when they log into network devices. Which action accomplishes this task?
B
Reference:
https://duo.com/docs/authproxy-reference
What is the function of the crypto isakmp key cisc406143794 address 0.0.0.0 0.0.0.0 command when establishing an IPsec VPN tunnel?
B
This command is used to configure pre-shared-key for IPsec remote acess users on the Cisco router. Address is mentioned as 0.0.0.0 0.0.0.0 because the users will be connecting from random ip addresses and it is almost impossible to mention all the ip addresses. Hence, 0.0.0.0 0.0.0.0 is used to allow all public ip addresses.
An administrator is adding a new switch onto the network and has configured AAA for network access control. When testing the configuration, the RADIUS authenticates to Cisco ISE but is being rejected. Why is the ip radius source-interface command needed for this configuration?
A
Reference:
https://www.cisco.com/c/en/us/td/docs/ios/12_2/security/command/reference/srfrad.html#wp1027454
Which statement about the configuration of Cisco ASA NetFlow v9 Secure Event Logging is true?
D
Which feature requires a network discovery policy on the Cisco Firepower NGIPS?
B
Which policy is used to capture host information on the Cisco Firepower Next Generation Intrusion Prevention System?
D
What is a characteristic of traffic storm control behavior?
A
Reference:
https://www.cisco.com/c/en/us/td/docs/routers/7600/ios/12-1E/configuration/guide/storm.html
DRAG DROP -
Drag and drop the Firepower Next Generation Intrusion Prevention System detectors from the left onto the correct definitions on the right.
Select and Place: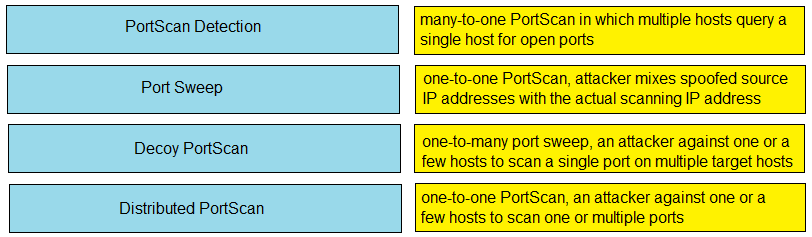
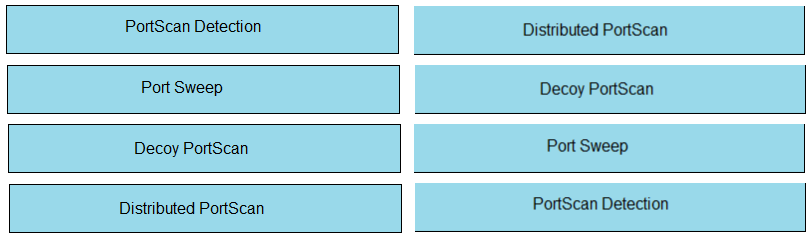
Reference:
https://www.cisco.com/c/en/us/td/docs/security/firepower/640/configuration/guide/fpmc-config-guide-v64/detecting_specific_threats.html
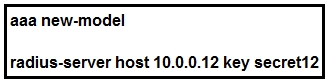
Refer to the exhibit. Which statement about the authentication protocol used in the configuration is true?
C