When configuring ISAKMP for IKEv1 Phase 1 on a Cisco IOS router, an administrator needs to input the command crypto isakmp key cisco address 0.0.0.0.
The administrator is not sure what the IP address in this command is used for. What would be the effect of changing the IP address from 0.0.0.0 to 1.2.3.4?
D
A network administrator is configuring SNMPv3 on a new router. The users have already been created, however an additional configuration is needed to facilitate access to the SNMP views. What must the administrator do to accomplish this?
C
DRAG DROP -
Drag and drop the NetFlow export formats from the left onto the descriptions on the right.
Select and Place: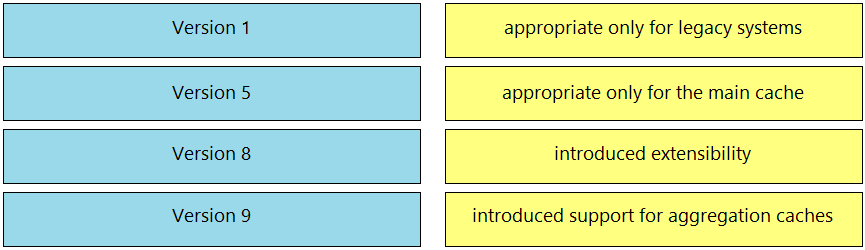
Reference:
https://www.ciscolive.com/c/dam/r/ciscolive/emea/docs/2015/pdf/BRKNMS-3132.pdf
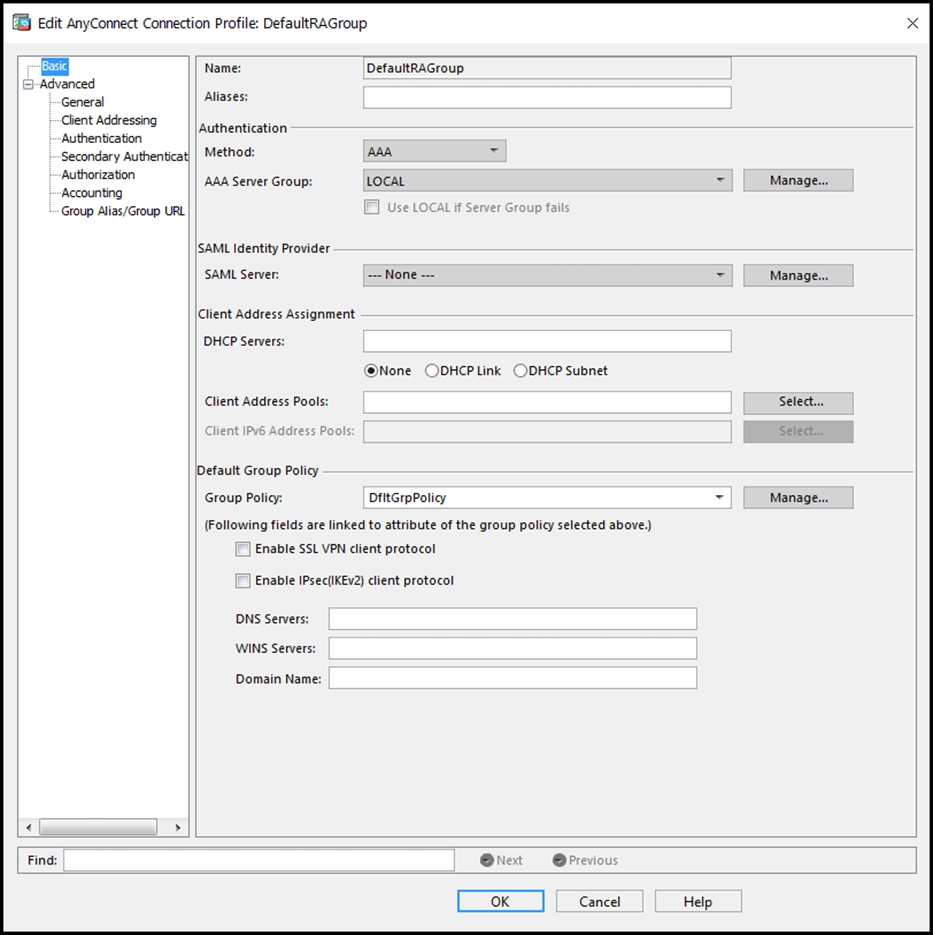
Refer to the exhibit. When configuring a remote access VPN solution terminating on the Cisco ASA, an administrator would like to utilize an external token authentication mechanism in conjunction with AAA authentication using machine certificates. Which configuration item must be modified to allow this?
C
An administrator is trying to determine which applications are being used in the network but does not want the network devices to send metadata to Cisco
Firepower. Which feature should be used to accomplish this?
D
An engineer is implementing NTP authentication within their network and has configured both the client and server devices with the command ntp authentication-key 1 md5 Cisc392481137. The server at 1.1.1.1 is attempting to authenticate to the client at 1.1.1.2, however is unable to do so. Which command is required to enable the client to accept the server's authentication key?
C
Reference:
https://www.oreilly.com/library/view/cisco-ios-cookbook/0596527225/ch14s13.html
Due to a traffic storm on the network, two interfaces were error-disabled, and both interfaces sent SNMP traps. Which two actions must be taken to ensure that interfaces are put back into service? (Choose two.)
CE
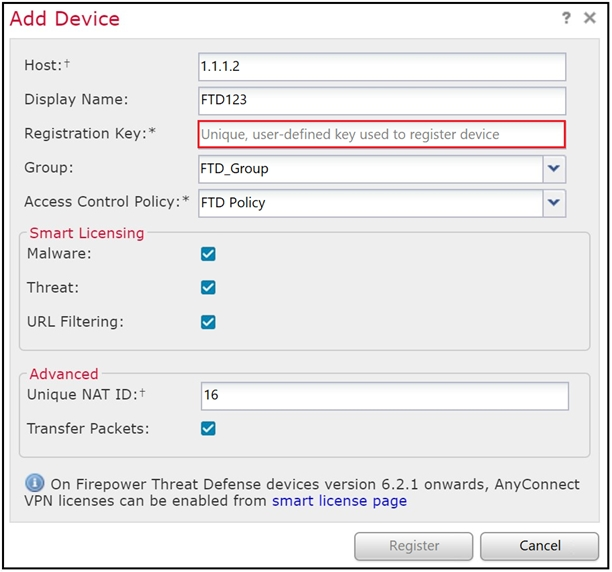
Refer to the exhibit. An administrator is adding a new Cisco FTD device to their network and wants to manage it with Cisco FMC. The Cisco FTD uses a registration key of Cisc392481137 and is not behind a NAT device. Which command is needed to enable this on the Cisco FTD?
C
Reference:
https://www.cisco.com/c/en/us/td/docs/security/firepower/620/configuration/guide/fpmc-config-guide-v62/firepower_command_line_reference.html#ID-
2201-000004b4
A network administrator needs to find out what assets currently exist on the network. Third-party systems need to be able to feed host data into Cisco Firepower.
What must be configured to accomplish this?
C
Which suspicious pattern enables the Cisco Tetration platform to learn the normal behavior of users?
A