What can be integrated with Cisco Threat Intelligence Director to provide information about security threats, which allows the SOC to proactively automate responses to those threats?
B
Which Cisco command enables authentication, authorization, and accounting globally so that CoA is supported on the device?
A
What is a characteristic of Firepower NGIPS inline deployment mode?
D
A mall provides security services to customers with a shared appliance. The mall wants separation of management on the shared appliance. Which ASA deployment mode meets these needs?
C
What is managed by Cisco Security Manager?
D
An organization is trying to improve their Defense in Depth by blocking malicious destinations prior to a connection being established. The solution must be able to block certain applications from being used within the network. Which product should be used to accomplish this goal?
A
An engineer notices traffic interruptions on the network. Upon further investigation, it is learned that broadcast packets have been flooding the network. What must be configured, based on a predefined threshold, to address this issue?
A
What is a feature of Cisco NetFlow Secure Event Logging for Cisco ASAs?
A
What is a key difference between Cisco Firepower and Cisco ASA?
D
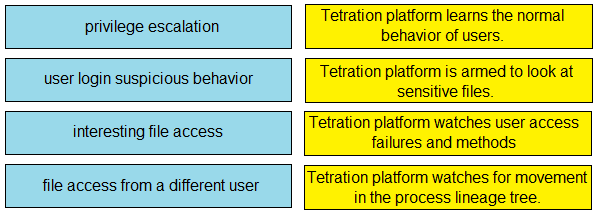
DRAG DROP -
Drag and drop the suspicious patterns for the Cisco Tetration platform from the left onto the correct definitions on the right.
Select and Place: