A customer has various external HTTP resources available including Intranet, Extranet, and Internet, with a proxy configuration running in explicit mode. Which method allows the client desktop browsers to be configured to select when to connect direct or when to use proxy?
C
What is a benefit of using Cisco CWS compared to an on-premises Cisco WSA?
D
Reference:
https://www.cisco.com/c/en/us/products/collateral/security/web-security-appliance/guide-c07-742373.html
An engineer needs to add protection for data in transit and have headers in the email message. Which configuration is needed to accomplish this goal?
B
Which Cisco platform processes behavior baselines, monitors for deviations, and reviews for malicious processes in data center traffic and servers while performing software vulnerability detection?
A
Reference:
https://www.cisco.com/c/en/us/td/docs/switches/datacenter/aci/apic/white_papers/Cisco-IT-Tetration-Deployment-Part-2-of-2.html
A network engineer must configure a Cisco ESA to prompt users to enter two forms of information before gaining access. The Cisco ESA must also join a cluster machine using preshared keys. What must be configured to meet these requirements?
A
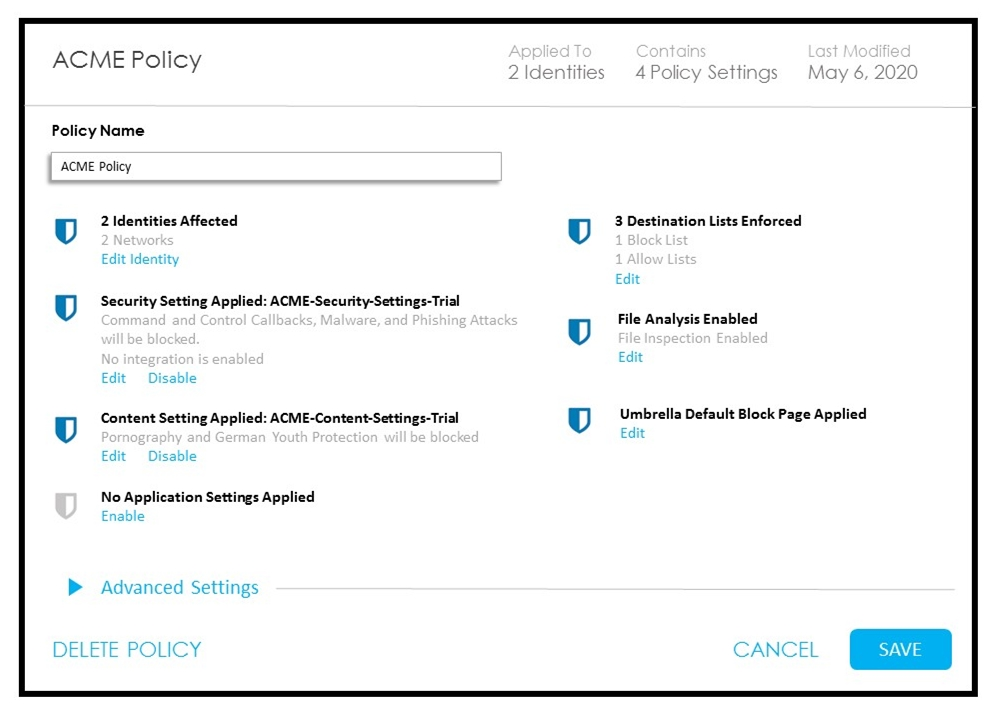
Refer to the exhibit. How does Cisco Umbrella manage traffic that is directed toward risky domains?
B
An organization wants to improve its cybersecurity processes and to add intelligence to its data. The organization wants to utilize the most current intelligence data for URL filtering, reputations, and vulnerability information that can be integrated with the Cisco FTD and Cisco WSA. What must be done to accomplish these objectives?
A
An organization is implementing URL blocking using Cisco Umbrella. The users are able to go to some sites but other sites are not accessible due to an error.
Why is the error occurring?
A
Which feature within Cisco Umbrella allows for the ability to inspect secure HTTP traffic?
C
When web policies are configured in Cisco Umbrella, what provides the ability to ensure that domains are blocked when they host malware, command and control, phishing, and more threats?
B
Reference:
https://support.umbrella.com/hc/en-us/articles/115004563666-Understanding-Security-Categories