Which Talos reputation center allows you to track the reputation of IP addresses for email and web traffic?
D
What is the primary role of the Cisco Email Security Appliance?
B
Which two services must remain as on-premises equipment when a hybrid email solution is deployed? (Choose two.)
DE
Reference:
https://www.cisco.com/c/dam/en/us/td/docs/security/ces/overview_guide/Cisco_Cloud_Hybrid_Email_Security_Overview_Guide.pdf
An organization is receiving SPAM emails from a known malicious domain. What must be configured in order to prevent the session during the initial TCP communication?
B
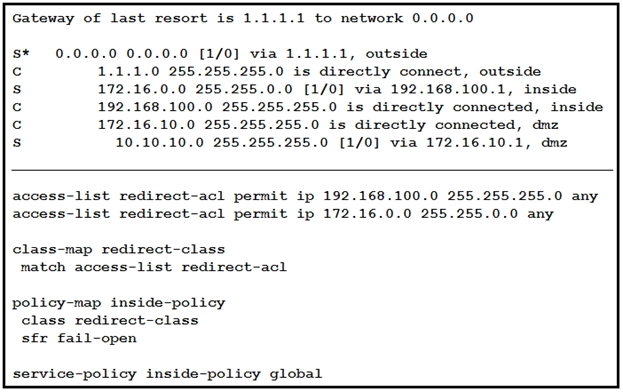
Refer to the exhibit. What is a result of the configuration?
D
An organization received a large amount of SPAM messages over a short time period. In order to take action on the messages, it must be determined how harmful the messages are and this needs to happen dynamically. What must be configured to accomplish this?
D
What are two differences between a Cisco WSA that is running in transparent mode and one running in explicit mode? (Choose two.)
AD
Which technology is used to improve web traffic performance by proxy caching?
A
Which proxy mode must be used on Cisco WSA to redirect TCP traffic with WCCP?
A
Reference:
https://www.cisco.com/c/en/us/support/docs/security/web-security-appliance/117940-qa-wsa-00.html
What is the purpose of the Decrypt for Application Detection feature within the WSA Decryption options?
D
Reference:
https://www.cisco.com/c/en/us/td/docs/security/wsa/wsa11-7/user_guide/b_WSA_UserGuide_11_7/b_WSA_UserGuide_11_7_chapter_01011.html