What is a role of NSO?
D
After a possible security breach, the network administrator of an ISP must verify the times that several different users logged into the network. Which command must the administrator enter to display the login time of each user that activated a session?
A
An engineer is developing a configuration script to enable dial-out telemetry streams using gRPC on several new devices. TLS must be disabled on the devices.
Which configuration must the engineer apply on the network?
C
Which additional configuration is required for NetFlow to provide traceback information?
A
What is the role of NSO in network automation?
A
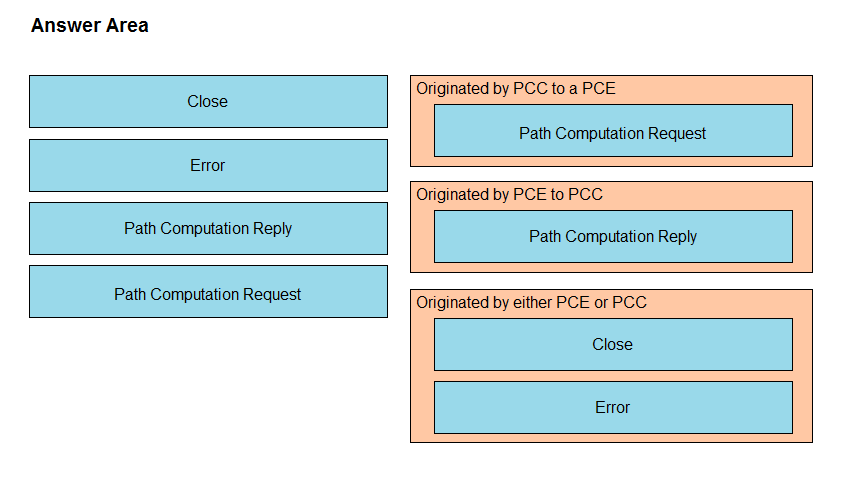
DRAG DROP -
Drag and drop the message types from the left onto the target field of the message originator on the right.
Select and Place: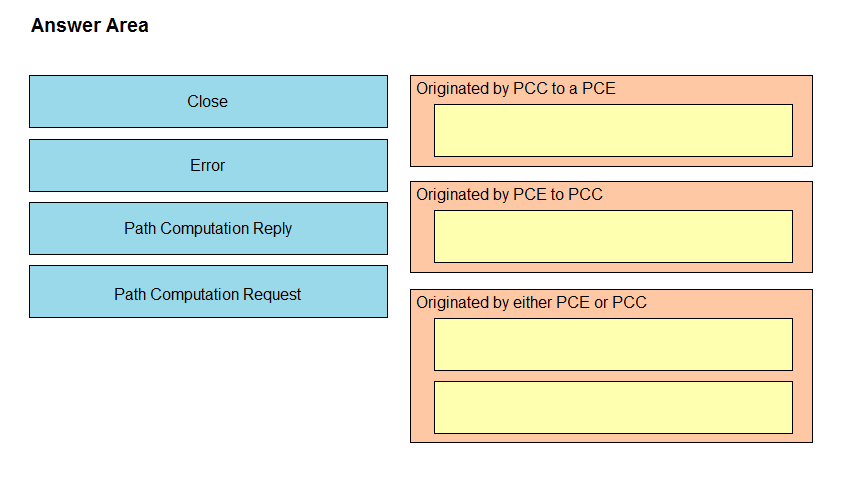
What do Chef and Puppet have in common?
C
How do intent APIs make it easier for network engineers to deploy and manage networks?
B
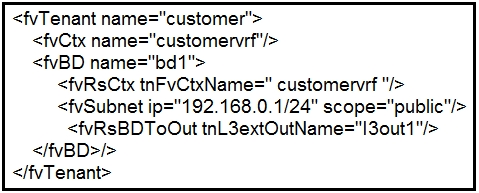
Refer to the exhibit. What does this REST API script configure?
B
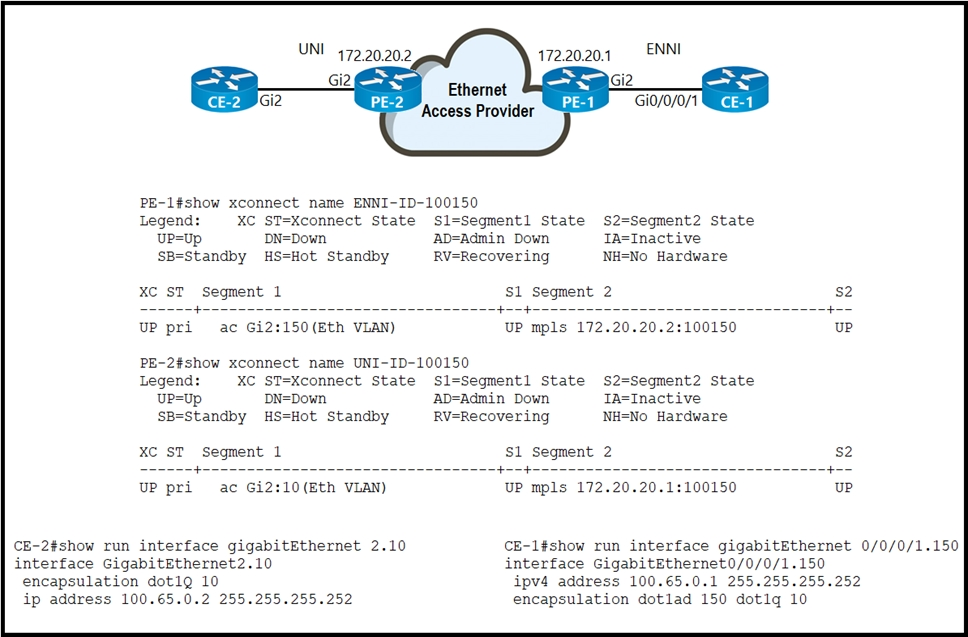
Refer to the exhibit. An Ethernet access provider is configuring routers PE-1 and PE-2 to provide E-Access EVPL service between UNI and ENNI. ENNI service multiplexing is based on 802.1ad tag 150, and service-multiplexed UNI is based on 802.1q tag 10. Which EFP configurations must the provider implement on PE-1 and PE-2 to establish end-to-end connectivity between CE-1 and CE-2?
C