
Refer to the exhibits. Which information is provided for traceback analysis when this configuration is applied?
C
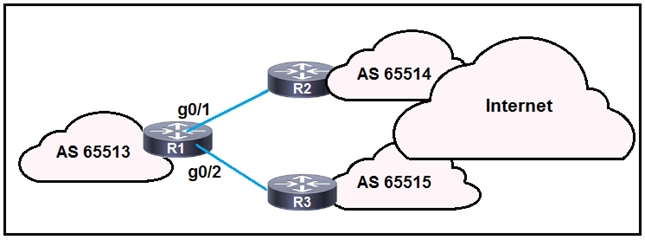
Refer to the exhibit. R1 is connected to two service providers and is under a DDoS attack.
Which statement about this design is true if URPF in strict mode is configured on both interfaces?
A
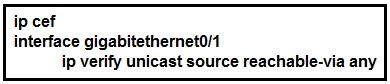
Refer to the exhibit. Router 1 was experiencing a DDoS attack that was traced to interface gigabitethernet0/1.
Which statement about this configuration is true?
C
Reference:
https://www.cisco.com/c/en/us/td/docs/switches/datacenter/sw/4_1/nx-os/security/configuration/guide/sec_nx-os-cfg/sec_urpf.html
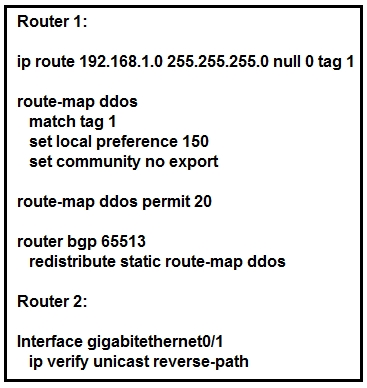
Refer to the exhibit. An engineer is preparing to implement data plane security configuration.
Which statement about this configuration is true?
C
Which configuration modifies Local Packet Transport Services hardware policies?
A.
B.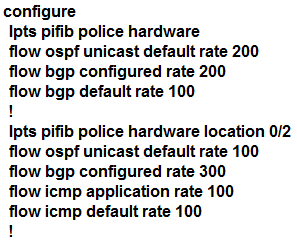
C.
D.
C
Reference:
https://www.cisco.com/c/en/us/td/docs/routers/crs/software/crs_r4-1/addr_serv/command/reference/b_ipaddr_cr41crs/ b_ipaddr_cr41crs_chapter_0111.html#wp1754734006
Which additional feature does MPLS DiffServ tunneling support?
B
Reference:
https://www.cisco.com/c/en/us/td/docs/ios-xml/ios/mp_te_diffserv/configuration/15-mt/mp-te-diffserv-15-mt-book/mp-diffserv-tun-mode.html
You are creating new Cisco MPLS TE tunnels. Which type of RSVP message does the headend router send to reserve bandwidth on the path to the tailend router?
A
Reference:
https://packetpushers.net/rsvp-te-protocol-deep-dive/
Which statement describes the advantage of a Multi-Layer control plane?
A
DRAG DROP -
Drag and drop the technologies from the left onto the correct definitions on the right.
Select and Place: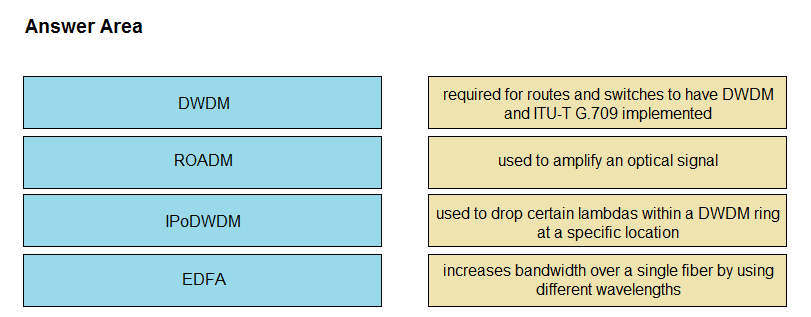
An engineer is setting up overlapping VPNs to allow VRF ABC and XYZ to communicate with VRF CENTRAL but wants to make sure that VRF ABC and XYZ cannot communicate.
Which configuration accomplishes these objectives?
A.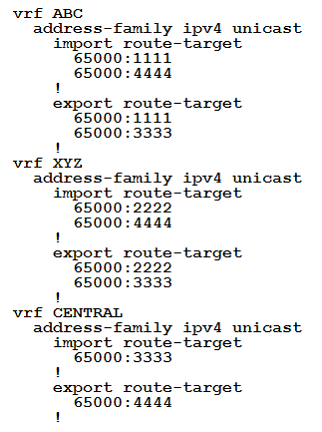
B.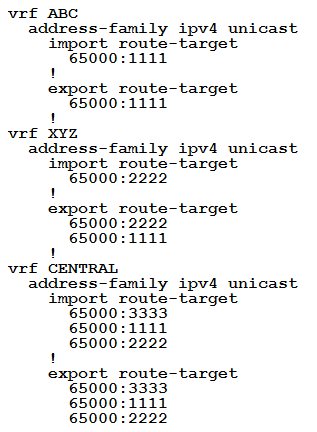
C.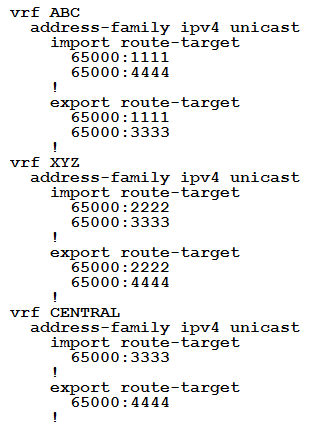
D.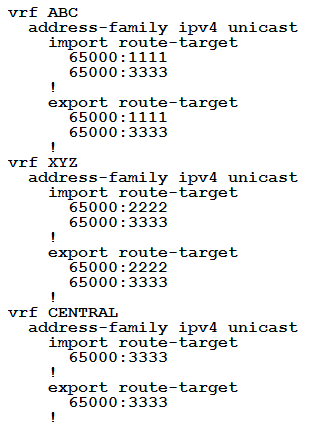
A