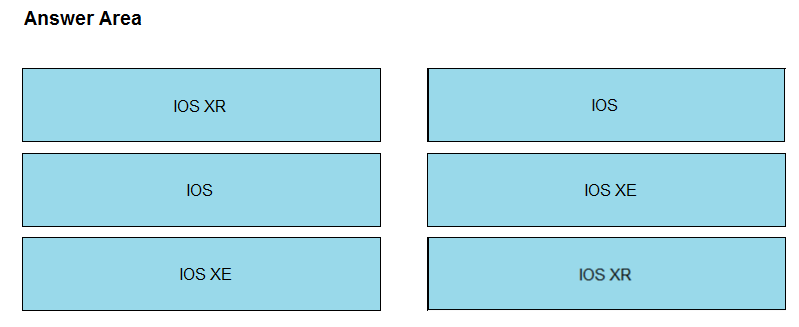
DRAG DROP -
Drag and drop the OSs from the left onto the correct descriptions on the right.
Select and Place: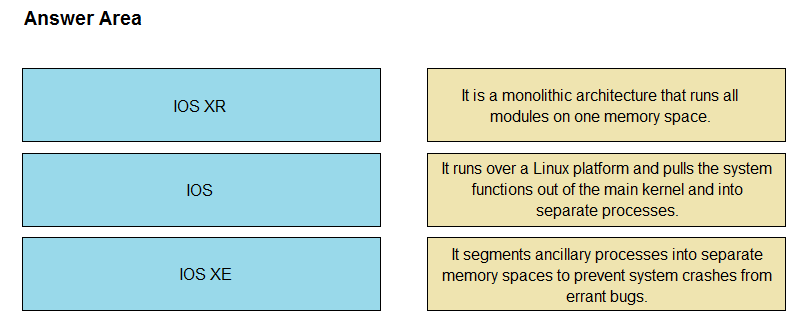
Reference:
https://specialties.bayt.com/en/specialties/q/276369/what-is-the-key-difference-between-ios-ios-xe-and-ios-xr-for-cisco-devices/
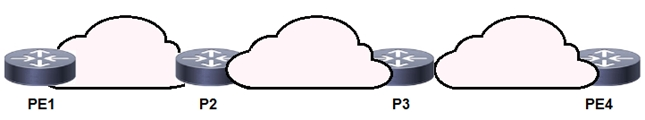
Refer to the exhibit. P3 and PE4 are at the edge of the service provider core and serve as ABR routers. Aggregation areas are on either side of the core.
Which statement about the architecture is true?
B
Reference:
https://www.cisco.com/c/en/us/td/docs/switches/lan/catalyst9600/software/release/16-12/configuration_guide/mpls/b_1612_mpls_9600_cg/ configuring_seamless_mpls.html
Which component is similar to an EVPN instance?
D
Why do Cisco MPLS TE tunnels require a link-state routing protocol?
D
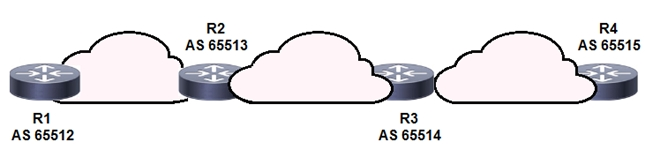
Refer to the exhibit. BGPsec is implemented on R1, R2, R3, and R4. BGP peering is established between neighboring autonomous systems.
Which statement about implementation is true?
D
You are configuring MPLS traffic-engineering tunnels in the core. Which two ways exist for the tunnel path across the core? (Choose two.)
BE
Which configuration mode do you use to apply the mpls ldp graceful-restart command in IOS XE Software?
D
Reference:
https://www.cisco.com/c/en/us/td/docs/ios-xml/ios/mp_ha/configuration/xe-3s/mp-ha-xe-3s-book/mp-ldp-grace-rstrt.html
After you analyze your network environment, you decide to implement a full separation model for Internet access and MPLS L3VPN services.
For which reason do you make this decision?
B
Which statement about the Cisco MPLS TE forwarding adjacency feature is true?
B
Reference:
https://www.cisco.com/c/en/us/td/docs/ios-xml/ios/mp_te_path_setup/configuration/xe-16/mp-te-path-setup-xe-16-book/mpls-traffic-engineering- forwarding-adjacency.pdf
While implementing TTL security, you issue the PE(config-router-af)#neighbor 2.2.2.2 ttl-security hops 2 command.
After you issue this command, which BGP packets does the PE accept?
D
Reference:
https://www.cisco.com/c/en/us/td/docs/ios/12_2sx/feature/guide/fsxebtsh.html#wp1059215