Refer to the exhibit.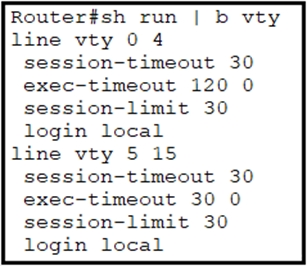
Security policy requires all idle exec sessions to be terminated in 600 seconds.
Which configuration achieves this goal?
C
Refer to the exhibit.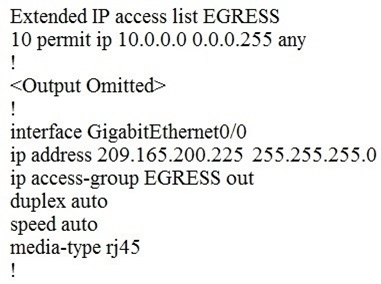
An engineer must block all traffic from a router to its directly connected subnet 209.165.200.0/24. The engineer applies access control list EGRESS in the outbound direction on the GigabitEthernet0/0 interface of the router. However, the router can still ping hosts on the 209.165.200.0/24 subnet.
What explains this behavior?
A
What is a characteristic of a next-generation firewall?
D
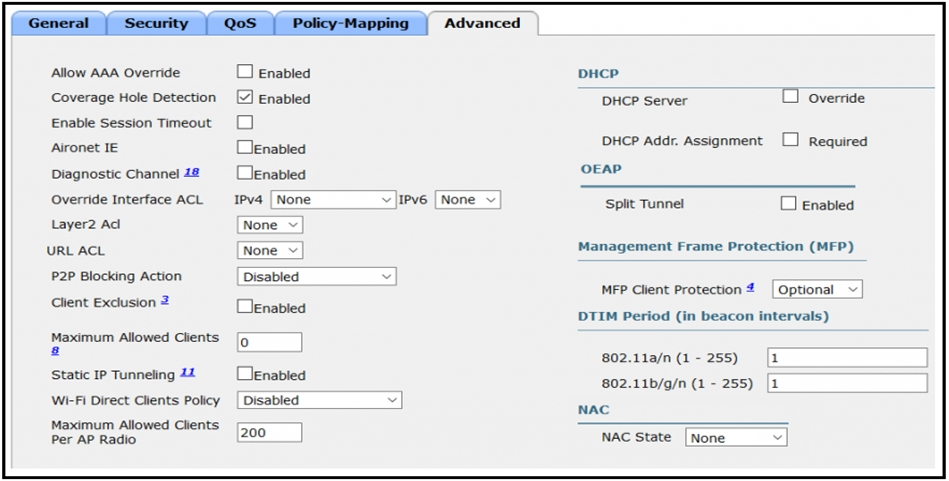
Refer to the exhibit. An engineer is investigating why guest users are able to access other guest user devices when the users are connected to the customer guest
WLAN. What action resolves this issue?
A
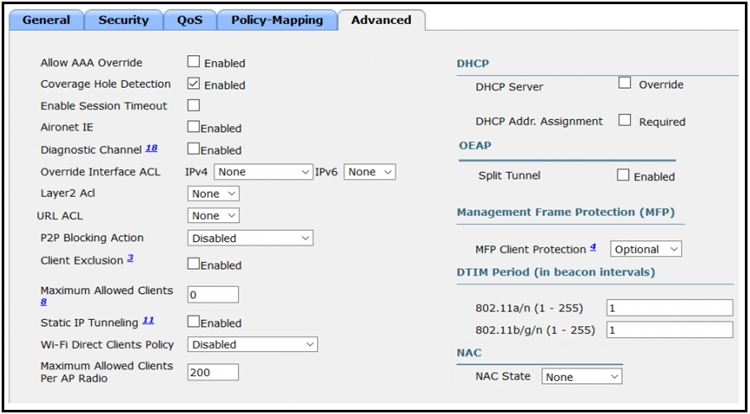
Refer to the exhibit. An engineer has configured Cisco ISE to assign VLANs to clients based on their method of authentication, but this is not working as expected.
Which action will resolve this issue?
C
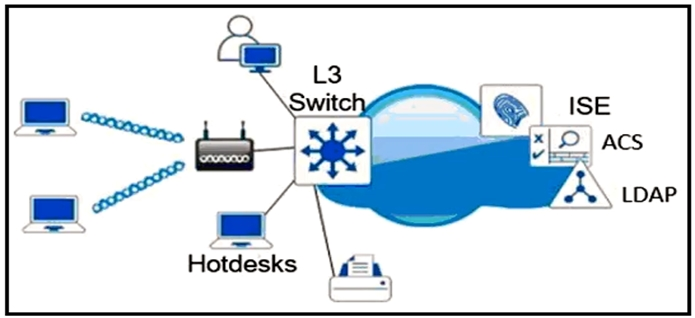
Refer to the exhibit. Which single security feature is recommended to provide Network Access Control in the enterprise?
B
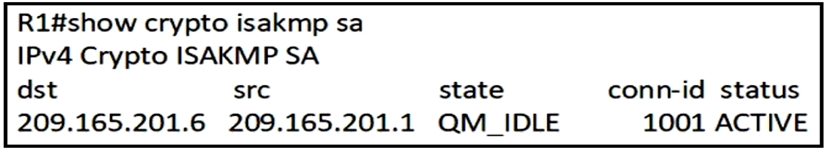
Refer to the exhibit. After configuring an IPsec VPN, an engineer enters the show command to verify the ISAKMP SA status. What does the status show?
C
Which two threats does AMP4E have the ability to block? (Choose two.)
AE
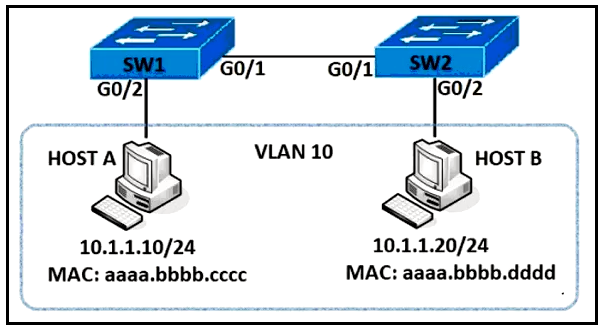
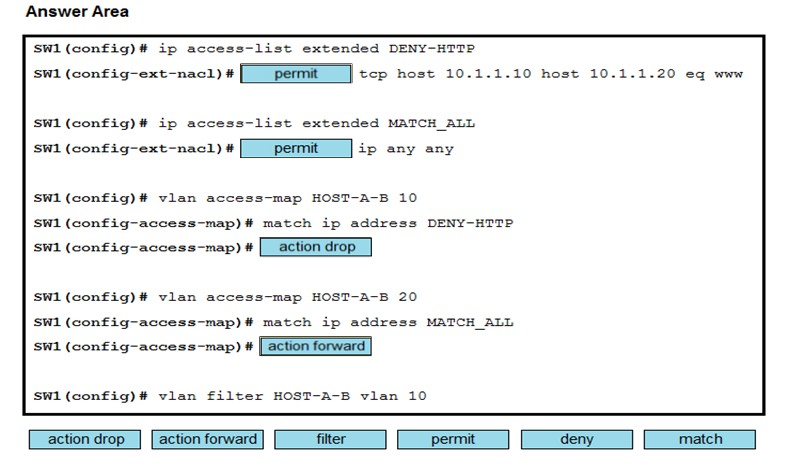
Refer to the exhibit. An engineer must deny HTTP traffic from host A to host B while allowing all other communication between the hosts. Drag and drop the commands into the configuration to achieve these results. Some commands may be used more than once. Not all commands are used.
Select and Place: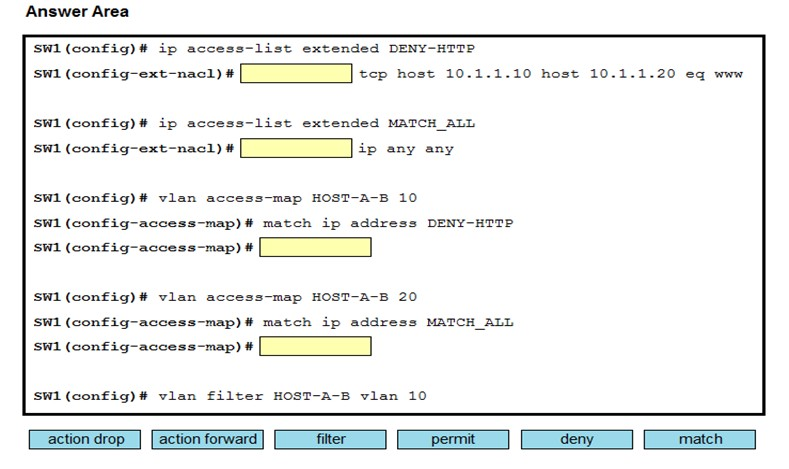
An engineer must configure the strongest password authentication to locally authenticate on a router. Which configuration must be used?
B
Reference:
https://learningnetwork.cisco.com/s/article/cisco-routers-password-types