What mechanism does PIM use to forward multicast traffic?
A
Refer to the exhibit.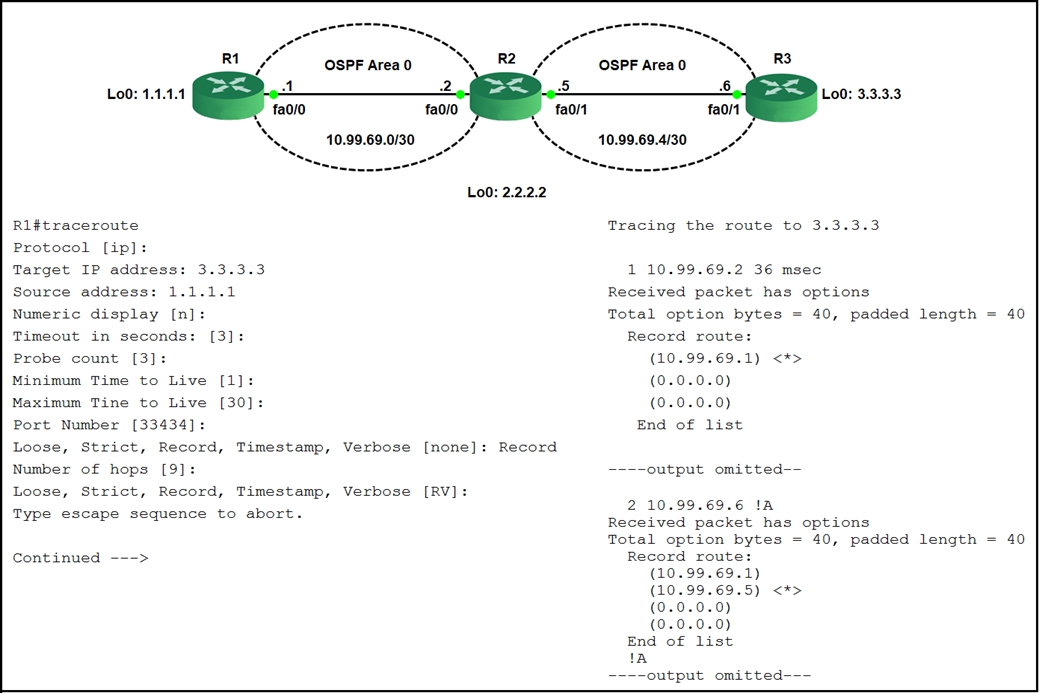
The traceroute fails from R1 to R3.
What is the cause of the failure?
D
Refer to the exhibit.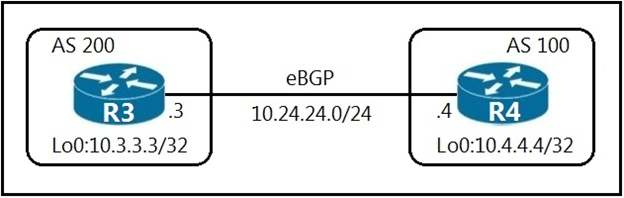
An engineer must establish eBGP peering between router R3 and router R4. Both routers should use their loopback interfaces as the BGP router ID.
Which configuration set accomplishes this task?
A
An engineer is configuring GigabitEthernet1/0/0 for VRRP. When the router has the highest priority in group 5, it must assume the master role.
Which command set should the engineer add to the configuration to accomplish this task? interface GigabitEthernet1/0/0 description To IDF A 38-70-774-10 ip address 172.16.13.2 255.255.255.0
C
Which two security features are available when implementing NTP? (Choose two.)
AE
How does the EIGRP metric differ from the OSPF metric?
C
By default, EIGRP metric is calculated:
metric = bandwidth + delay
While OSPF is calculated by:
OSPF metric = Reference bandwidth / Interface bandwidth in bps
Refer to the exhibit.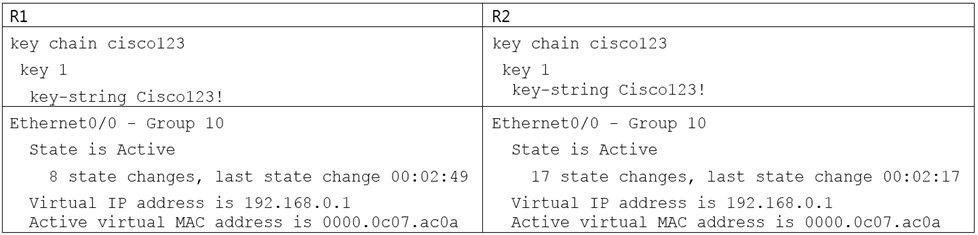
An engineer is installing a new pair of routers in a redundant configuration.
Which protocol ensures that traffic is not disrupted in the event of a hardware failure?
A
The ג€virtual MAC addressג€ is 0000.0c07.acXX (XX is the hexadecimal group number) so it is using HSRPv1. HSRP Version 2 uses a new MAC address which ranges from 0000.0C9F.F000 to 0000.0C9F.FFFF.
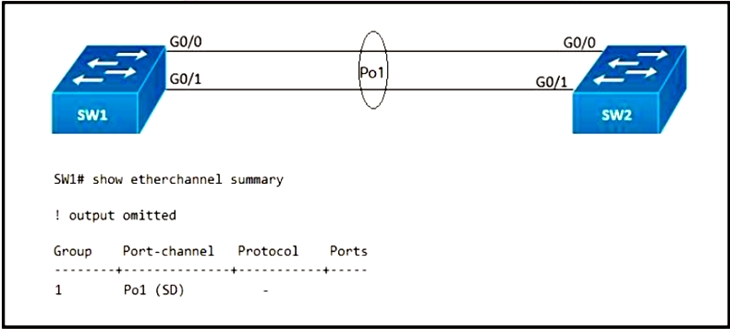
Refer to the exhibit. After an engineer configures an EtherChannel between switch SW1 and switch SW2, this error message is logged on switch SW2:
SW2#
09:45:32: %PM-4-ERR_DISABLE: channel-misconfig error detected on Gi0/0, putting Gi0/0 in err-disable state
09:45:32: %PM-4-ERR_DISABLE: channel-misconfig error detected on Gi0/1, putting Gi0/1 in err-disable state
Based on the output from switch SW1 and the log message received on switch SW2, what action should the engineer take to resolve this issue?
A
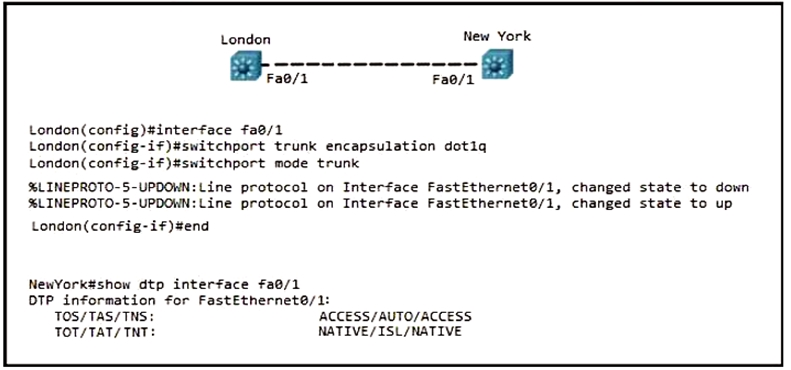
Refer to the exhibit. Communication between London and New York is down. Which command set must be applied to resolve this issue?
B
Which encryption hashing algorithm does NTP use for authentication?
B