Which term refers to an endpoint agent that tries to join an 802.1X-enabled network?
C
Which port does Cisco ISE use for native supplicant provisioning of a Windows laptop?
B
Reference:
https://www.cisco.com/c/en/us/td/docs/security/ise/2-1/admin_guide/b_ise_admin_guide_21/b_ise_admin_guide_20_chapter_010101.html
DRAG DROP -
Drag the Cisco ISE node types from the left onto the appropriate purposes on the right.
Select and Place: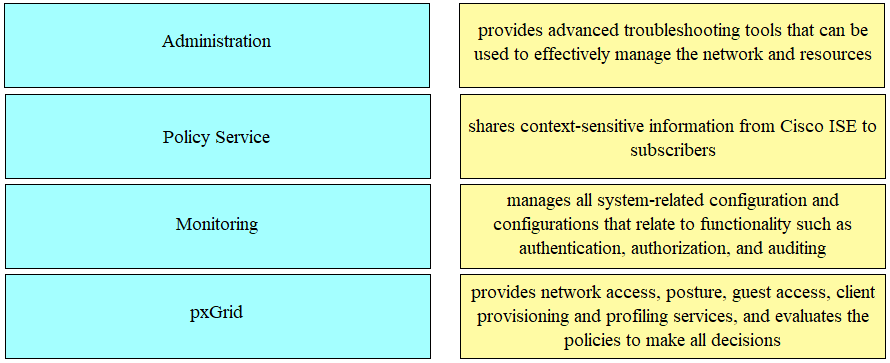
What must match between Cisco ISE and the network access device to successfully authenticate endpoints?
A
Reference:
https://www.cisco.com/en/US/docs/security/ise/1.0/user_guide/ise10_man_network_devices.html
When planning for the deployment of Cisco ISE, an organization's security policy dictates that they must use network access authentication via RADIUS. It also states that the deployment needs to provide an adequate amount of security and visibility for the hosts on the network.
Why should the engineer configure MAB in this situation?
D
An organization is implementing Cisco ISE posture services and must ensure that a host-based firewall is in place on every Windows and Mac computer that attempts to access the network. They have multiple vendors' firewall applications for their devices, so the engineers creating the policies are unable to use a specific application check in order to validate the posture for this.
What should be done to enable this type of posture check?
B
An administrator is configuring posture with Cisco ISE and wants to check that specific services are present on the workstations that are attempting to access the network.
What must be configured to accomplish this goal?
C
Reference:
https://www.cisco.com/c/en/us/td/docs/security/ise/2-1/admin_guide/b_ise_admin_guide_21/b_ise_admin_guide_20_chapter_010001.html
What is a function of client provisioning?
C
Reference:
https://www.cisco.com/c/en/us/td/docs/security/ise/1-3/admin_guide/b_ise_admin_guide_13/b_ise_admin_guide_sample_chapter_010111.html
A network administrator must use Cisco ISE to check whether endpoints have the correct version of antivirus installed.
Which action must be taken to allow this capability?
A
MacOS users are complaining about having to read through wordy instructions when remediating their workstations to gain access to the network.
Which alternate method should be used to tell users how to remediate?
D