An administrator connects an HP printer to a dot1x enable port, but the printer is nor accessible.
Which feature must the administrator enable to access the printer?
B
Reference:
https://community.cisco.com/t5/network-access-control/ise-mab-soa/td-p/2214921
When configuring an authorization policy, an administrator cannot see specific Active Directory groups present in their domain to be used as a policy condition.
However, other groups that are in the same domain are seen.
What is causing this issue?
C
Reference:
https://www.cisco.com/c/en/us/td/docs/security/ise/2-3/ise_active_directory_integration/b_ISE_AD_integration_2x.html
An engineer is implementing network access control using Cisco ISE and needs to separate the traffic based on the network device ID and use the IOS device sensor capability.
Which probe must be used to accomplish this task?
C
Reference:
https://www.cisco.com/c/en/us/support/docs/security/identity-services-engine/200292-Configure-Device-Sensor-for-ISE-Profilin.html
What is an advantage of using EAP-TLS over EAP-MS-CHAPv2 for client authentication?
C
Reference:
https://www.securew2.com/blog/eap-tls-vs-peap-mschapv2-which-authentication-protocol-is-superior
What must be configured on the WLC to configure Central Web Authentication using Cisco ISE and a WLC?
D
Reference:
https://www.cisco.com/c/en/us/td/docs/wireless/controller/7-6/configuration-guide/b_cg76/b_cg76_chapter_0110001.pdf
A network administrator is configuring authorization policies in Cisco ISE. There is a requirement to use AD group assignments to control access to network resources. After a recent power failure and Cisco ISE rebooting itself, the AD group assignments no longer work.
What is the cause of this issue?
A
Reference:
https://www.cisco.com/c/en/us/td/docs/security/ise/2-3/ise_active_directory_integration/b_ISE_AD_integration_2x.html#ID612
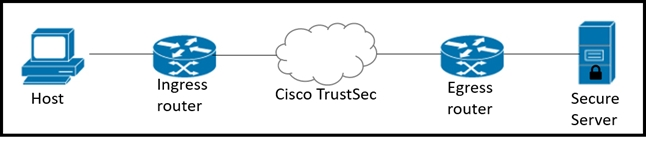
Refer to the exhibit.
Which component must be configured to apply the SGACL?
C
Reference:
https://www.cisco.com/c/en/us/td/docs/switches/lan/catalyst6500/ios/12-2SY/configuration/guide/sy_swcg/trustsec.pdf
A laptop was stolen and a network engineer added it to the block list endpoint identity group.
What must be done on a new Cisco ISE deployment to redirect the laptop and restrict access?
A
When creating a policy within Cisco ISE for network access control, the administrator wants to allow different access restrictions based upon the wireless SSID to which the device is connecting.
Which policy condition must be used in order to accomplish this?
D
Reference:
https://www.cisco.com/c/en/us/support/docs/security/identity-services-engine/115734-ise-policies-ssid-00.html
A company manager is hosting a conference. Conference participants must connect to an open guest SSID and only use a preassigned code that they enter into the guest portal prior to gaining access to the network.
How should the manager configure Cisco ISE to accomplish this goal?
C
Reference:
https://www.cisco.com/c/en/us/td/docs/security/ise/2-6/admin_guide/b_ISE_26_admin_guide/b_ISE_admin_26_guest.html