An engineer is using Cisco Prime Infrastructure reporting to monitor the state of security on the WLAN. Which output is produced when the Adaptive wIPS Top 10
AP report is run?
A
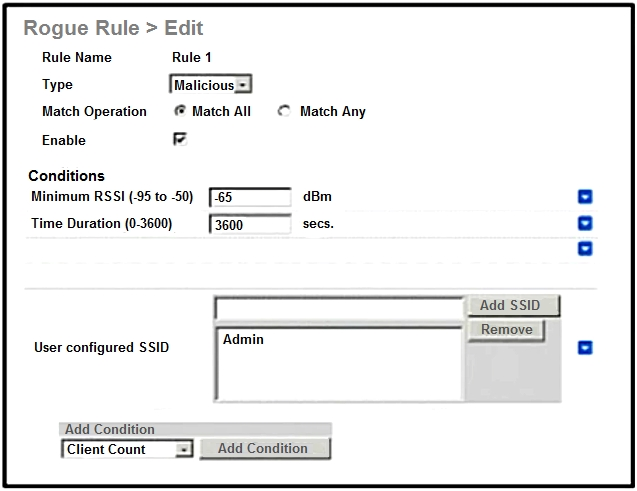
Refer to the exhibit. An engineer tries to manage the rogues on the Cisco WLC. Based on the configuration, which AP is marked as malicious by the controller?
D
Which devices can be tracked with the Cisco Context Aware Services?
A
Reference:
https://www.cisco.com/c/en/us/support/docs/wireless/context-aware-software/110836-cas-faq.html
Which two events are outcomes of a successful RF jamming attack? (Choose two.)
AE
An engineer must create an account to log in to the CLI of an access point for troubleshooting. Which configuration on the WLC will accomplish this?
D
A multitenant building contains known wireless networks in most of the suites. Rogues must be classified in the WLC. How are the competing wireless APs classified?
B
An enterprise has recently deployed a voice and video solution available to all employees using AireOS controllers. The employees must use this service over their laptops, but users report poor service when connected to the wireless network. The programs that consume bandwidth must be identified and restricted.
Which configuration on the WLAN aids in recognizing the traffic?
D
Which customizable security report on Cisco Prime Infrastructure will show rogue APs detected since a point in time?
C
An engineer configures a Cisco Aironet 600 Series OfficeExtend AP for a user who works remotely. What is configured on the Cisco WLC to allow the user to print a printer on his home network?
A
Reference:
https://www.cisco.com/c/en/us/support/docs/wireless/aironet-602-officeextend-access-point/117540-configure-splittunneloeap-00.html
An engineer must configure a Cisco WLC to support Cisco Aironet 600 Series OfficeExtend APs. Which two Layer 2 security options are supported in this environment? (Choose two.)
BC