Which method does Cisco SD-WAN use to avoid fragmentation issues?
A
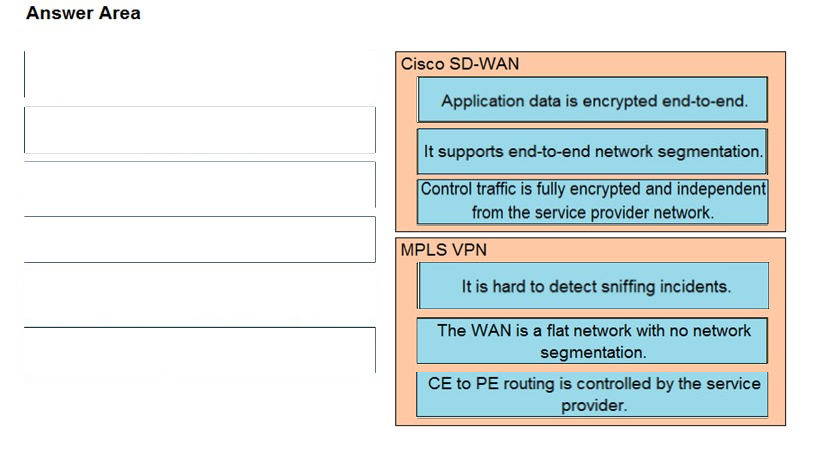
DRAG DROP -
Drag and drop the descriptions from the left onto the corresponding WAN connectivity types and categories on the right.
Select and Place: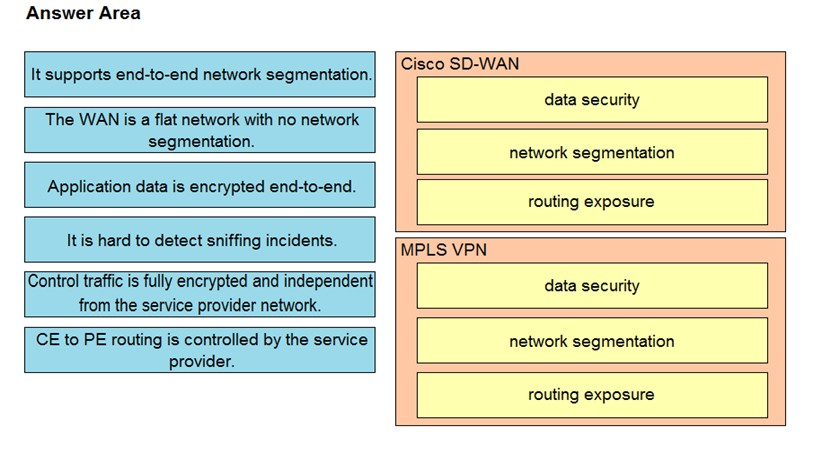
A global organization with several branches hired a network architect to design an overlay VPN solution. The branches communicate with each other frequently.
The customer expects to add more branches in the future. To meet the customer's security requirements, the architect plans to provide traffic protection using dynamic IPsec tunnels. Which solution should the architect choose?
A
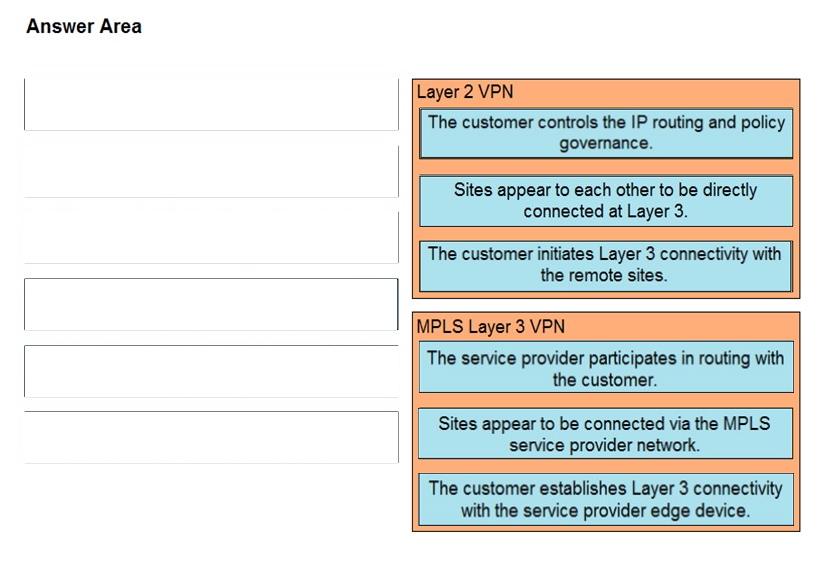
DRAG DROP -
Drag and drop the descriptions from the left onto the corresponding VPN types on the right.
Select and Place: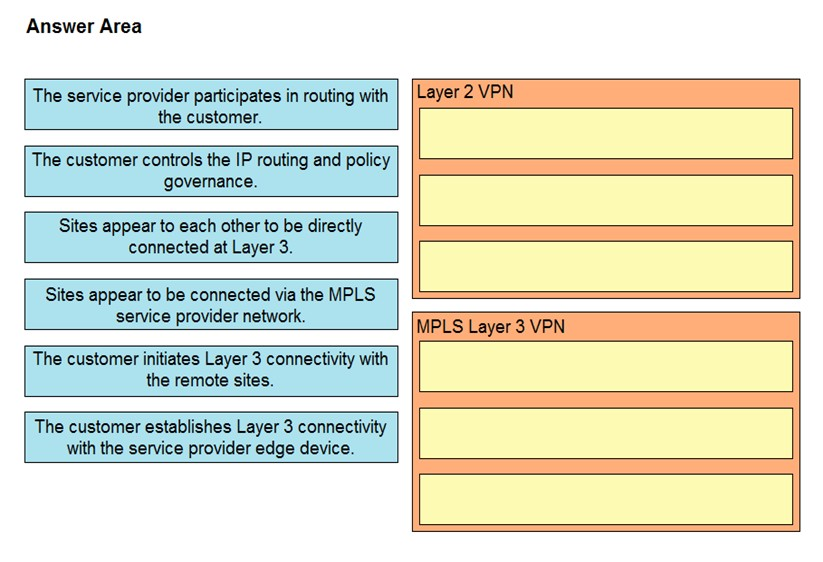
A customer requests a VPN solution to connect multiple sites with the company headquarters. All the sites use the same IP subnet. The engineer plans to use
VPLS. Which solution must the engineer include in the design?
C
An ISP provides Layer 3 VPN service over MPLS to a customer with four branches and multiple CE routers at each branch. To exchange the routes that are learned from the CE routers, which BGP address family should the ISP activate among the PE routers?
C
In the SD-WAN underlay network, which WAN Edge VPN ID is defined as the transport VPN and is used to carry control traffic?
A
A company's security policy requires that all connections between sites be encrypted in a manner that does not require maintenance of permanent tunnels. The sites are connected through a private MPLS-based service that uses a dynamically changing key and spoke-to-spoke communication. Which type of transport encryption must be used in this environment?
A
A network solution is being designed for a company that connects to multiple Internet service providers. Which Cisco proprietary BGP path attribute will influence outbound traffic flow?
C
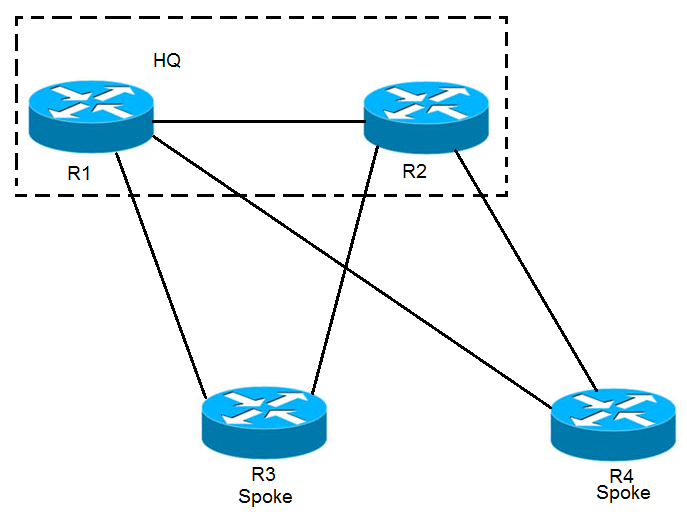
Refer to the exhibit. EIGRP has been configured on all links. The spoke nodes have been configured as EIGRP stubs, and the WAN links to R3 have higher bandwidth and lower delay than the WAN links to R4. When a link failure occurs at the R1-R2 link, what happens to traffic on R1 that is destined for a subnet attached to R2?
D