DRAG DROP -
Drag and drop the definitions from the left to the configuration on the right.
Select and Place: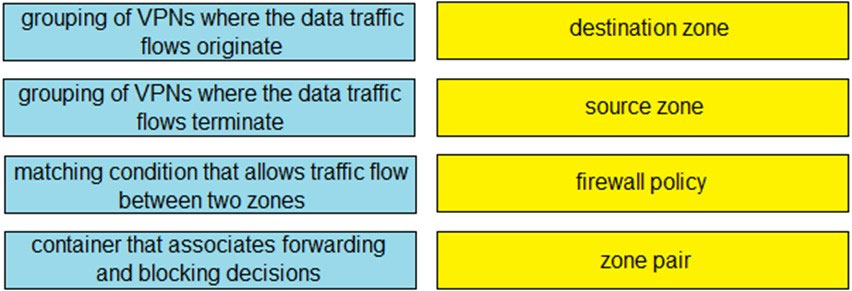
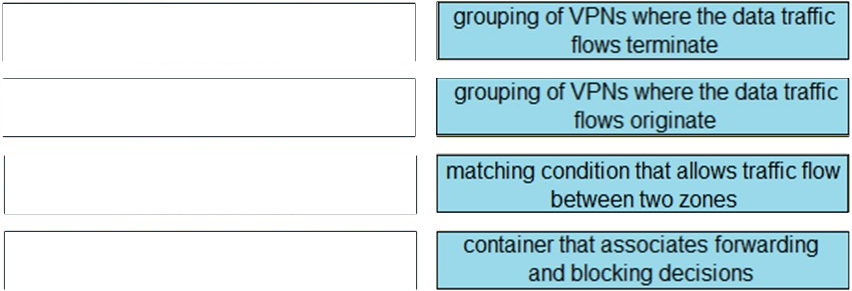
Reference:
https://www.cisco.com/c/en/us/td/docs/routers/sdwan/configuration/security/vedge/security-book/ent-firewall-app-aware.html#:~:text=Source%20zone
%E2%80%94A%20grouping%20of,part%20of%20only%20one%20zone.&text=A%20VPN%20can%20be%20part%20of%20only%20one%20zone.,-Firewall%
20policy%E2%80%94A
An engineer is configuring a centralized policy to influence network route advertisement. Which controller delivers this policy to the fabric?
A
Reference:
https://www.cisco.com/c/en/us/td/docs/routers/sdwan/configuration/policies/vedge-20-x/policies-book/policy-overview.html
Which VPN connects the transport-side WAN Edge interface to the underlay/WAN network?
B
Reference:
https://www.ciscolive.com/c/dam/r/ciscolive/emea/docs/2020/pdf/R6BGArNQ/TECRST-2191.pdf page 13
An engineer is configuring a list that matches all IP prefixes with lengths from /1 to /16 in a centralized control policy. Which list accomplishes this task?
B
Refer to the exhibit. An engineer is configuring service chaining. Which set of configurations is required for all traffic from Site ID 1 going toward Site ID 2 to get filtered through the firewall on the hub site?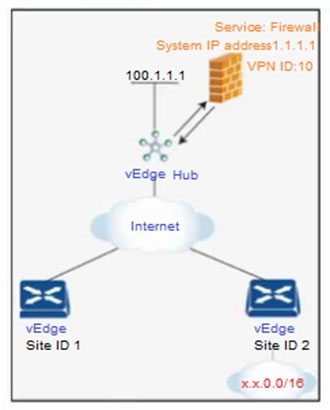
A.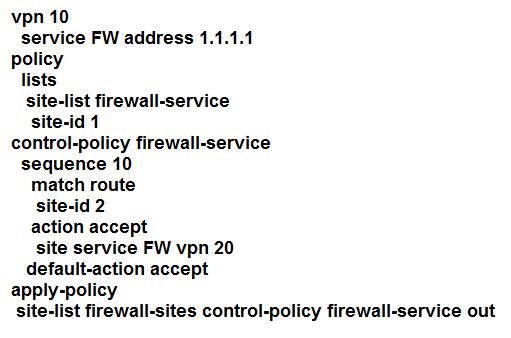
B.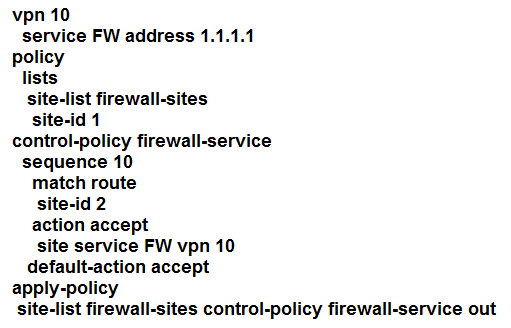
C.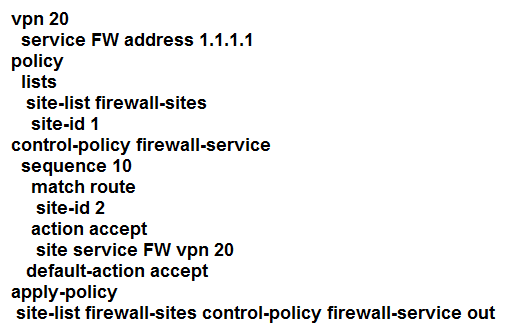
D.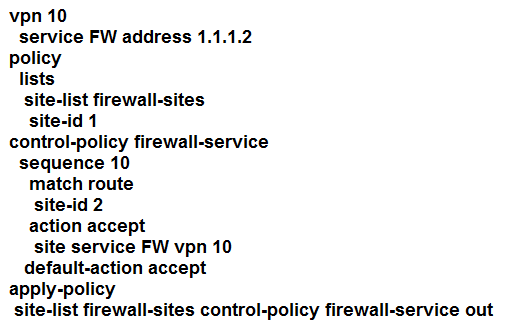
B
An engineer is configuring a data policy for packets that must be captured through the policy. Which command accomplishes this task?
C
Reference:
https://www.cisco.com/c/dam/en/us/td/docs/routers/sdwan/configuration/config-18-4.pdf#page=357
An administrator must configure an ACL for traffic coming in from the service-side VPN on a specific WAN Edge device with circuit ID 123456789. Which policy must be used to configure this ACL?
D
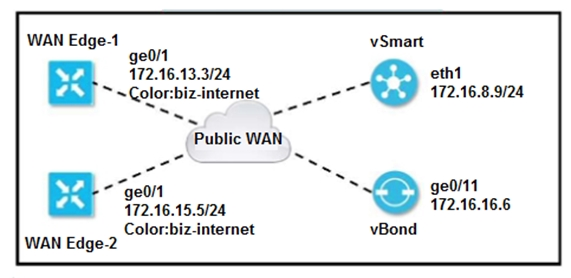
Refer to the exhibit. The tunnel interface configuration on both WAN Edge routers is:
Which configuration for WAN Edge routers will connect to the Internet?
A.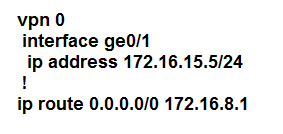
B.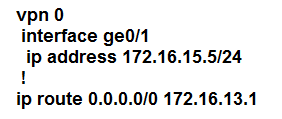
C.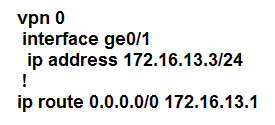
D.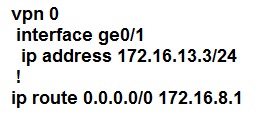
B
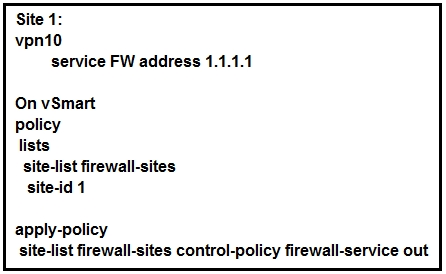
Refer to the exhibit. Which configuration routes Site 2 through the firewall in Site 1?
A.
B.
C.
D.
C
A customer is receiving routes via OMP from vSmart controller for a specific VPN. The customer must provide access to the W2 loopback received via OMP to the
OSPF neighbor on the service-side VPN. Which configuration fulfills these requirements?
A.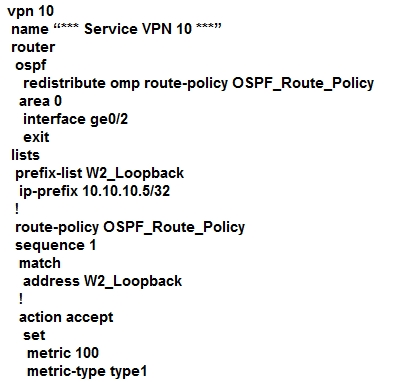
B.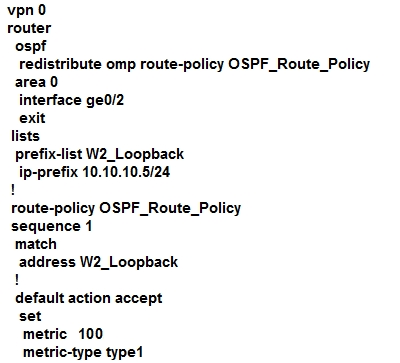
C.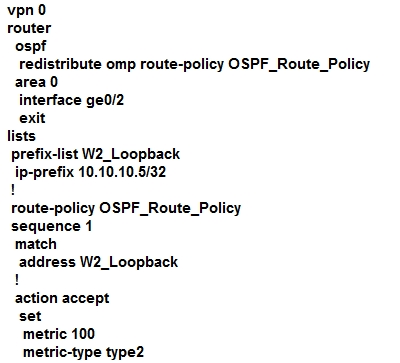
D.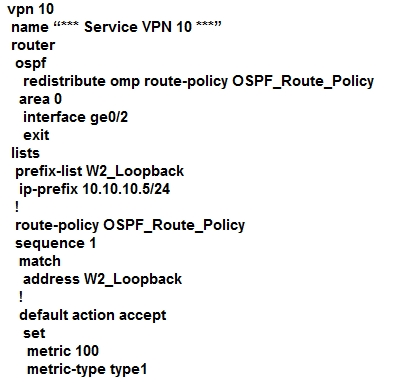
D