Which Cisco product provides malware and content filtering through DNS?
D
Which Cisco platform provides organization-wide automation, security, policy enforcement, and agility across wired and wireless networks?
B
What is a characteristic of the Cisco Finesse platform?
C
Reference:
https://developer.cisco.com/docs/finesse/#!finesse-overview/what-are-the-business-benefits
An engineer needs to retrieve a list of locally available Firepower Threat Defense upgrade packages by using the Firepower Management Center REST API. The engineer uses a GET request with the URL:
/api/fmc_platform/v1/updates/upgradepackages/f413afeb-e6f6-75f4-9169-6d9bd49s625e
What does `f413afeb-e6f6-75f4-9169-6d9bd49s625e` represent?
B
Reference:
https://www.cisco.com/c/en/us/td/docs/security/firepower/640/api/REST/Firepower_Management_Center_REST_API_Quick_Start_Guide_640.html
Refer to the exhibit.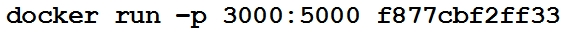
A process running on the host wants to access the service running inside this Docker container. Which port or ports are used to make a connection?
D
DRAG DROP -
Drag and drop the Dockerfile instructions from the left onto the descriptions on the right. Not all options are used.
Select and Place: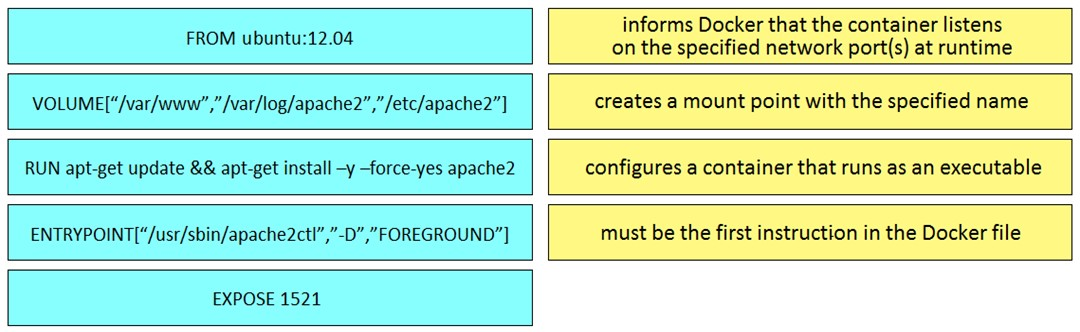
What are two security benefits of a Docker-based application? (Choose two.)
CE
A local Docker alpine image has been created with an image ID of a391665405fe and tagged as `latest`. Which command creates a running container based on the tagged image, with the container port 8080 bound to port 80 on the host?
D
Refer to the exhibit.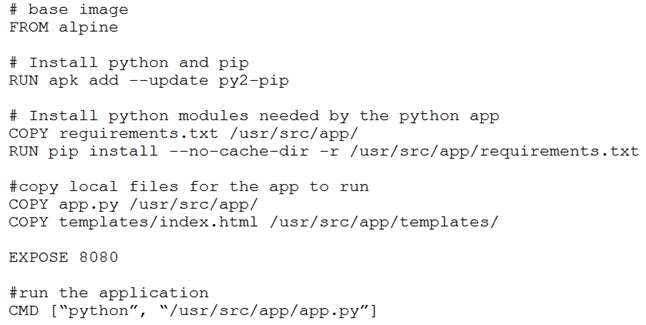
Which function does the EXPOSE line perform when building an image from this Dockerfile?
C
Which two elements are foundational principles of DevOps? (Choose two.)
AD