Which OWASP threat occurs when untrusted data is supplied as input to an interpreter as part of a command or query?
C
Reference:
https://owasp.org/www-community/Injection_Theory
Which product provides network controller-level management features?
B
Reference:
https://www.cisco.com/c/en/us/products/cloud-systems-management/index.html
What is the purpose of the Cisco VIRL software tool?
C
Reference:
https://www.speaknetworks.com/cisco-virl-better-gns3/
What are two advantages of the Model-View-Controller software design pattern? (Choose two.)
AB
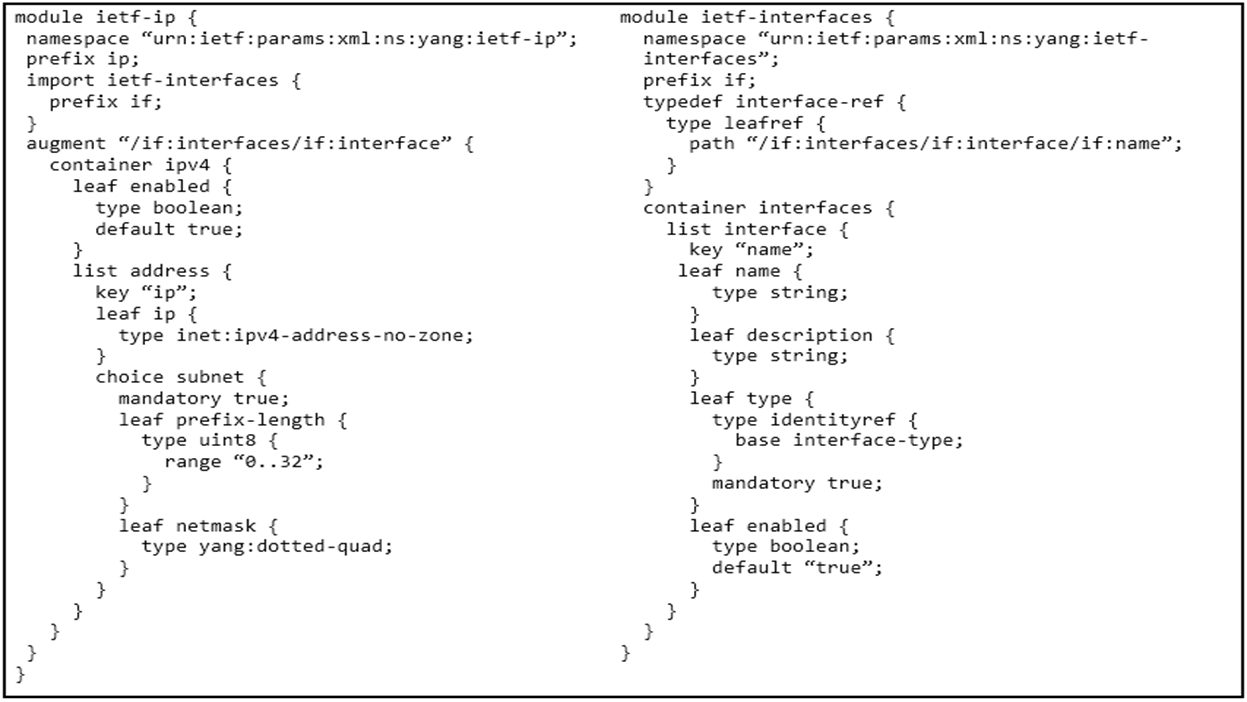
Refer to the exhibit. Which JSON snippet configures a new interface according to YANG model?
A.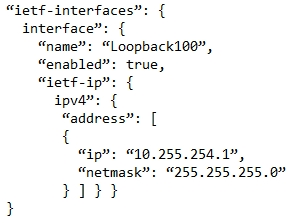
B.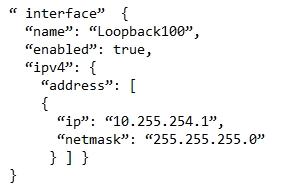
C.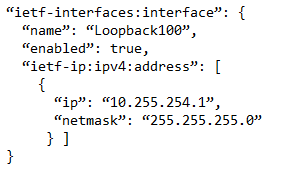
D.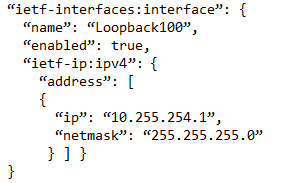
D
Refer to the exhibit.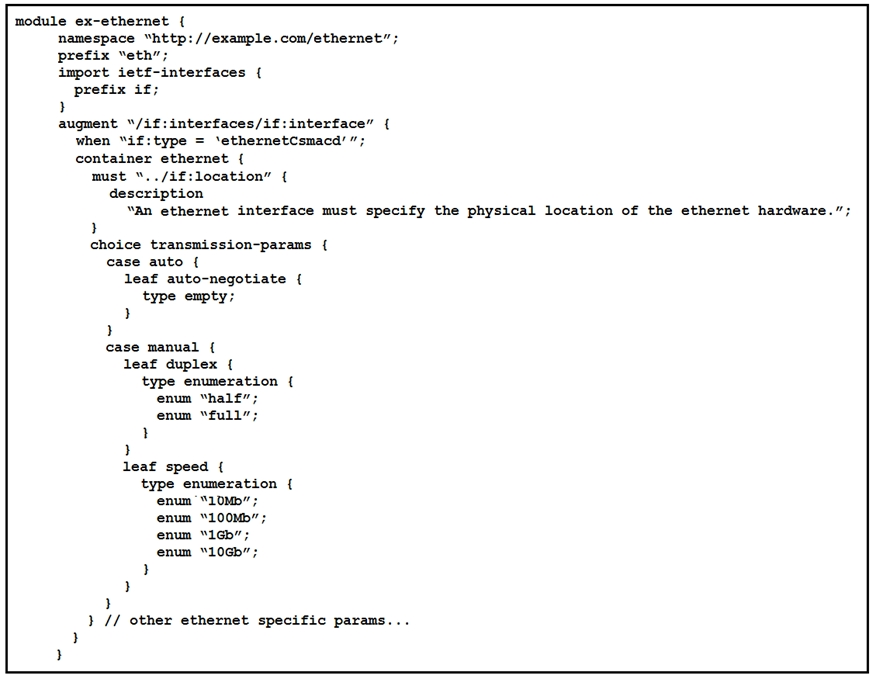
What is represented in this YANG module?
A
Reference:
https://github.com/CiscoDevNet/dnav3-code/blob/master/intro-mdp/yang/models/Cisco-IOS-XE-interfaces-oper.yang
Which CI/CD tool is an automation tool used to build, test, and deploy software?
D
Reference:
https://www.infoworld.com/article/3271126/what-is-cicd-continuous-integration-and-continuous-delivery-explained.html
An automation script fails to connect to an internal server exactly 1 out of 2 times it is executed. This behavior is seen from different clients. Which networking device must be at fault?
A
What are two advantages of YANG-based approaches for infrastructure automation? (Choose two.)
AC
Refer to the exhibit.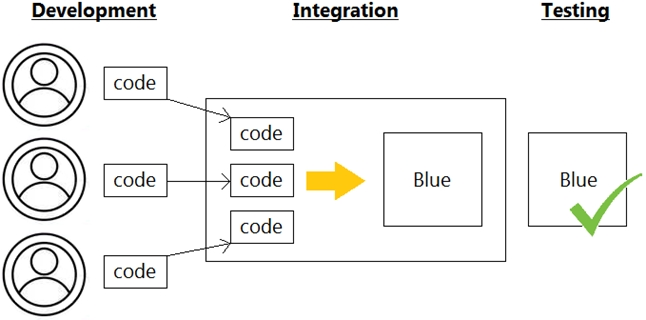
Which infrastructure automation method is shown?
A