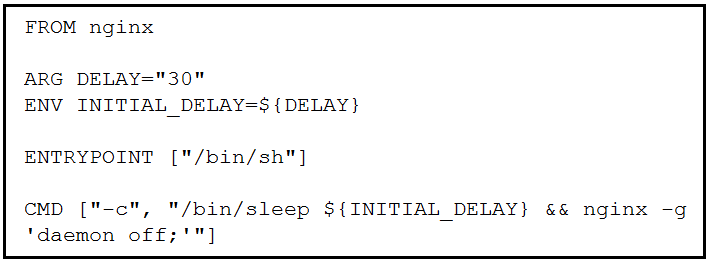
Refer to the exhibit. Which command, including arguments, is executed when the container starts?
A
A developer created a new secure API and is testing the functionality locally. The API was added to a container for further testing, and other team members and applications need to connect to the API. Which command exposes the API in the container as port 8443 and allows connections external to the host?
C
A developer has created a new image to use in a Docker build and has added a tag for the image by using the command:
$ docker tag 84fe411926287 local/app:0.4
Which command must be executed next to build the Docker image using the tag?
D
Access to the management interface of devices must be restricted by using SSH and HTTPS. Which two ports must be included in the ACLs for the protocols to work? (Choose two.)
AD
What is a benefit of using a code review process in application development?
D
Which OWASP threat takes advantage of a web application that the user has already authenticated to execute an attack?
D
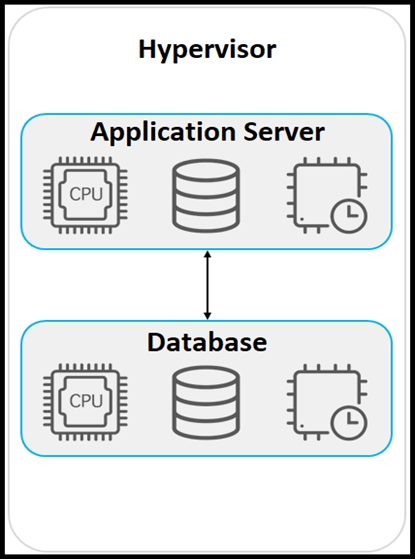
Refer to the exhibit. An application must be deployed on a server that has other applications installed. The server resources are to be allocated based on the deployment requirements. The OS for each application must be independent. Which type of deployment is used?
B
What is a benefit of a distributed version control system?
C
Reference:
https://about.gitlab.com/topics/version-control/benefits-distributed-version-control-system/
A company requires a new platform to store large volumes of log data that is generated in their assembly plant. The platform must be scalable, so the underlying technology must provide a path for fast deployment of new nodes for data and indexing? The data contains sensitive information, so specialist encryption tools must be used to secure the data. Which application deployment model meets the requirements?
B
Reference:
https://www.simform.com/blog/cloud-deployment-models/
What is a procedural component of CI/CD pipelines?
A