What is the role of disaggregation in controller-based networking?
A
What is a function performed by a web server?
D
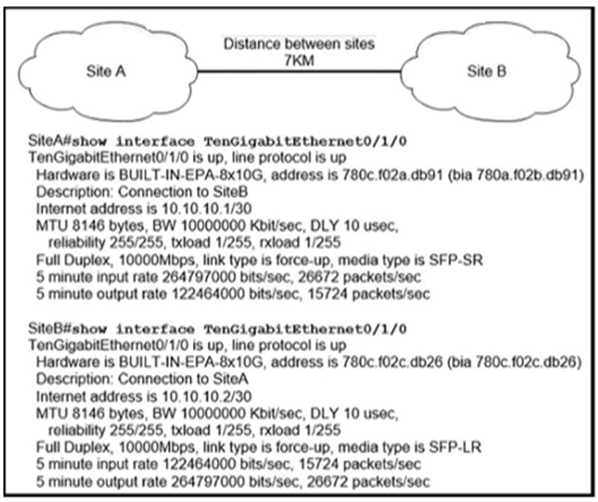
Refer to the exhibit. Site A was recently connected to site B over a new single-mode fiber path. Users at site A report intermittent connectivity issues with applications hosted at site B. What is the reason for the problem?
D
Why is UDP more suitable than TCP for applications that require low latency such as VoIP?
D
What are the two functions of SSIDs? (Choose two.)
AD
The SSID is a unique identifier that wireless networking devices use to establish and maintain wireless connectivity. The SSID can consist of up to 32 alphanumeric, case-sensitive, characters. Wireless clients connect using the SSID for secure communications. The SSID is a unique token that identifies an
802.11 wireless network. It is used by wireless devices to identify a network and to establish and maintain wireless connectivity. An SSID must be configured and assigned to a wireless client device interface before the device can associate with an access point.
Which two characteristics describe the access layer in a three-tier network architecture? (Choose two.)
BD
The Access Layer is the one closer to the users. In fact, at this layer, we find the users themselves and the access-layer switches. The main purpose of this layer is to physically connect users to the network. In other words, there is just a cable between end-user PCs, printers, and wireless access points and access-layer switches.
Which PoE mode enables powered-devices detection and guarantees power when the device detected?
A
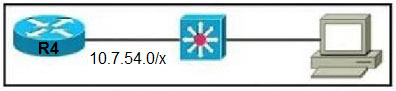
Refer to the exhibit. The router has been configured with a super net to accommodate the requirements for 380 users on a Subnet. The requirement already considers 30% future growth. Which configuration verifies the IP subnet on router R4?
D
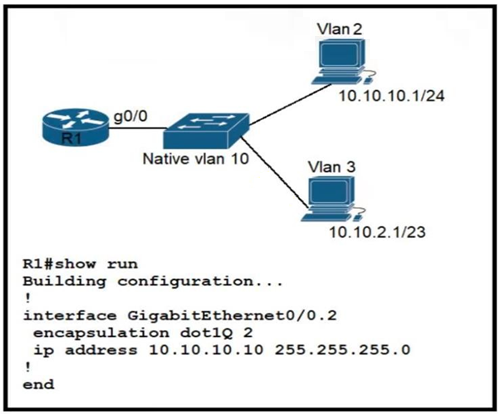
Refer to the exhibit. Configurations for the switch and PCs are complete. Which configuration must be applied so that VLANs 2 and 3 communicate back and forth?
B