Which technology prevents client devices from arbitrarily connecting to the network without state remediation?
B
Which protocol does an access point use to draw power from a connected switch?
B
An administrator must secure the WLC from receiving spoofed association requests. Which steps must be taken to configure the WLC to restrict the requests and force the user to wait 10 ms to retry an association request?
C
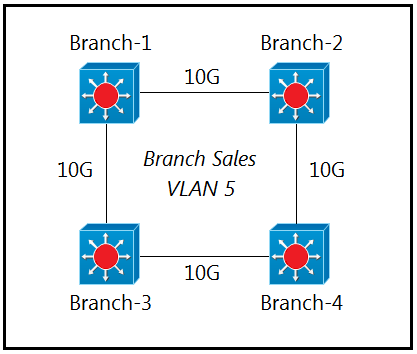
Refer to the exhibit. Only four switches are participating in the VLAN spanning-tree process.
Branch-1: priority 614440 -
Branch-2: priority 39391170 -
Branch-3: priority 0 -
Branch-4: root primary -
Which switch becomes the permanent root bridge for VLAN 5?
C
An engineer must configure traffic for a VLAN that is untagged by the switch as it crosses a trunk link. Which command should be used?
D
What are two benefits of using the PortFast feature? (Choose two.)
AD
What is the benefit of configuring PortFast on an interface?
B
DRAG DROP -
Drag and drop the functions of AAA supporting protocols from the left onto the protocols on the right.
Select and Place: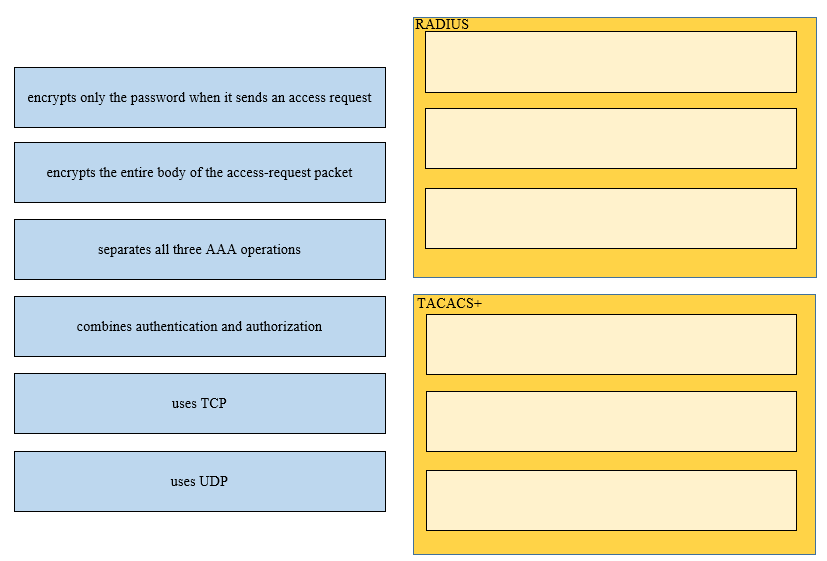
Why does a switch flood a frame to all ports?
B
An engineer configures interface Gi1/0 on the company PE router to connect to an ISP. Neighbor discovery is disabled.
Which action is necessary to complete the configuration if the ISP uses third-party network devices?
B