Your customers are concerned about the security of their sensitive data and their inquiry asks about what happens to old storage devices on AWS. What would be the best answer to this question?
B
When a storage device has reached the end of its useful life, AWS procedures include a decommis-sioning process that is designed to prevent customer data from being exposed to unauthorized indi-viduals.
AWS uses the techniques detailed in DoD 5220.22-M ("National Industrial Security Program Oper-ating Manual ") or NIST 800-88 ("Guidelines for Media
Sanitization") to destroy data as part of the decommissioning process.
All decommissioned magnetic storage devices are degaussed and physically destroyed in accord-ance with industry-standard practices.
Reference:
https://d0.awsstatic.com/whitepapers/aws-security-whitepaper.pdf
In AWS Identity and Access Management (IAM), you can make use of the ______ APIs to grant users temporary access to your resources.
D
AWS Security Token Service enables the creation of temporary credentials that can be used along with IAM in order to grant access to trusted entities and users to your AWS resources for a prede-fined amount of time.
Reference:
http://docs.aws.amazon.com/IAM/latest/UserGuide/id_credentials_temp.html
An IAM user has two conflicting policies as part of two separate groups. One policy allows him to access an S3 bucket, while another policy denies him the access. Can the user access that bucket?
B
When a request is made, the AWS IAM policy decides whether a given request should be allowed or denied. The evaluation logic follows these rules:
By default, all requests are denied. (In general, requests made using the account credentials for re-sources in the account are always allowed.)
An explicit allow policy overrides this default.
An explicit deny policy overrides any allows.
In this case since there is an explicit deny policy, it will over ride everything and the request will be denied.
Reference:
http://docs.aws.amazon.com/IAM/latest/UserGuide/AccessPolicyLanguage_EvaluationLogic.html
An organization has launched 5 instances: 2 for production and 3 for testing. The organization wants a particular group of IAM users to access only the test instances and not the production ones. They want to deploy the instances in various locations based on the factors that will change from time to time, especially in the test group. They expect instances will often need to be churned, i.e. deleted and replaced, especially in the testing group. This means the five instances they have created now will soon be replaced by a different set of five instances. The members of each group, produc-tion and testing, will not change in the foreseeable future. Given the situation, what choice below is the most efficient and time-saving strategy to define the IAM policy?
D
AWS Identity and Access Management is a web service that allows organizations to manage users and user permissions for various AWS services. The user can add conditions as a part of the IAM policies. The condition can be set on AWS Tags, Time, and Client IP as well as on various parame-ters. If the organization wants the user to access only specific instances, he should define proper tags and add to the IAM policy condition. The sample policy is shown below.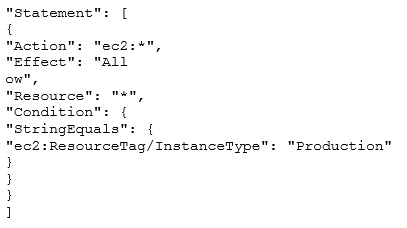
Reference:
http://docs.aws.amazon.com/IAM/latest/UserGuide/ExampleIAMPolicies.html
For IAM user, a virtual Multi-Factor Authentication (MFA) device uses an application that gener-ates ______-digit authentication codes that are compatible with the time-based one-time password (TOTP) standard.
C
A virtual MFA device uses an application that generates six-digit authentication codes that are com-patible with the time-based one-time password (TOTP) standard. Therefore, any application that you wish to use in order to make your smart phone your virtual MFA device needs to conform with the standard.
Reference:
http://docs.aws.amazon.com/IAM/latest/UserGuide/id_credentials_mfa_enable_virtual.html
The ______ IAM policy element describes the specific action or actions that will be allowed or de-nied.
B
The Action element describes the specific action or actions that will be allowed or denied.
Statements must include either an Action or NotAction element. Each AWS service has its own set of actions that describe tasks that you can perform with that service.
Reference:
http://docs.aws.amazon.com/IAM/latest/UserGuide/reference_policies_elements.html
A company wants to review the security requirements of Glacier. Which of the below mentioned statements is true with respect to the AWS Glacier data security?
B
For Amazon Web Services, all the data stored on Amazon Glacier is protected using serverside en-cryption. AWS generates separate unique encryption keys for each Amazon Glacier archive, and en-crypts it using AES-256. The encryption key then encrypts itself using AES-256 with a master key that is stored in a secure location.
Reference:
https://aws.amazon.com/glacier/faqs/
A user has configured two security groups which allow traffic as given below:
1: SecGrp1:
Inbound on port 80 for 0.0.0.0/0
Inbound on port 22 for 0.0.0.0/0
2: SecGrp2:
Inbound on port 22 for 10.10.10.1/32
If both the security groups are associated with the same instance, which of the below mentioned statements is true?
B
A user can attach more than one security group to a single EC2 instance. In this case, the rules from each security group are effectively aggregated to create one set of rules. AWS uses this set of rules to determine whether to allow access or not. Thus, here the rule for port 22 with IP 10.10.10.1/32 will merge with IP
0.0.0.0/0 and open ports 22 and 80 for all.
Reference:
http://docs.aws.amazon.com/AWSEC2/latest/UserGuide/using-network-security.html
Is it possible to create an S3 bucket accessible only by a certain IAM user using policies in a Cloud-Formation template?
A
With AWS Identity and Access Management (IAM), you can create IAM users to control who has access to which resources in your AWS account. You can use
IAM with AWS CloudFormation to control what AWS CloudFormation actions users can perform, such as view stack templates, create stacks, or delete stacks.
In addition to AWS CloudFormation actions, you can manage what AWS services and resources are available to each user.
Reference:
http://docs.aws.amazon.com/AWSCloudFormation/latest/UserGuide/using-iam-template.html
In Amazon CloudFront, if you have chosen On for Logging, the access logs are stored in _______________.
A
In Amazon CloudFront, if you chose On for Logging, the logs store in the Amazon S3 bucket that you want CloudFront to store access logs in. For example: myawslogbucket.s3.amazonaws.com
If you enable logging, CloudFront records information about each end-user request for an object and stores the files in the specified Amazon S3 bucket.
Reference:
http://docs.aws.amazon.com/AmazonCloudFront/latest/DeveloperGuide/distribution-web-values-specify.html#DownloadDistValuesLoggingOnOff