A SysOps administrator is examining the following AWS CloudFormation template: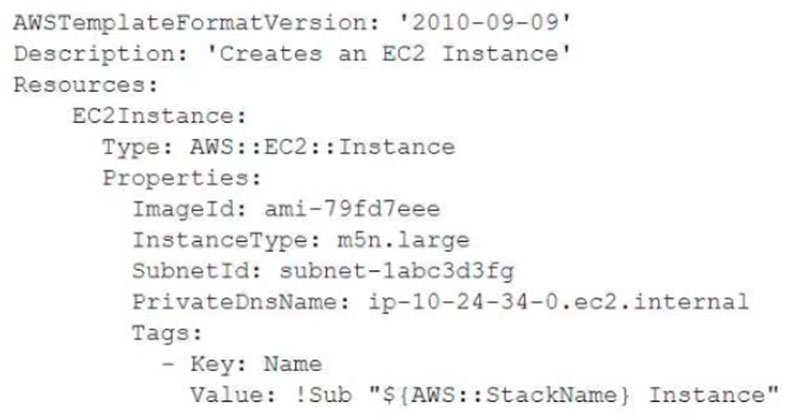
Why will the stack creation fail?
C
A new application runs on Amazon EC2 instances and accesses data in an Amazon RDS database instance. When fully deployed in production, the application fails. The database can be queried from a console on a bastion host. When looking at the web server logs, the following error is repeated multiple times:
*** Error Establishing a Database Connection
Which of the following may be causes of the connectivity problems? (Choose two.)
CE
A compliance team requires all administrator passwords for Amazon RDS DB instances to be changed at least annually.
Which solution meets this requirement in the MOST operationally efficient manner?
A
A SysOps administrator is responsible for managing a fleet of Amazon EC2 instances. These EC2 instances upload build artifacts to a third-party service. The third-party service recently implemented a strict IP allow list that requires all build uploads to come from a single IP address.
What change should the systems administrator make to the existing build fleet to comply with this new requirement?
A
A company uses an Amazon CloudFront distribution to deliver its website. Traffic logs for the website must be centrally stored, and all data must be encrypted at rest.
Which solution will meet these requirements?
C
An organization created an Amazon Elastic File System (Amazon EFS) volume with a file system ID of fs-85ba41fc, and it is actively used by 10 Amazon EC2 hosts. The organization has become concerned that the file system is not encrypted.
How can this be resolved?
D
A company uses an AWS Service Catalog portfolio to create and manage resources. A SysOps administrator must create a replica of the company's existing AWS infrastructure in a new AWS account.
What is the MOST operationally efficient way to meet this requirement?
D
A SysOps administrator must manage the security of an AWS account. Recently, an IAM user's access key was mistakenly uploaded to a public code repository.
The SysOps administrator must identify anything that was changed by using this access key.
How should the SysOps administrator meet these requirements?
C
A company runs a retail website on multiple Amazon EC2 instances behind an Application Load Balancer (ALB). The company must secure traffic to the website over an HTTPS connection.
Which combination of actions should a SysOps administrator take to meet these requirements? (Choose two.)
BD
SIMULATION -
Instructions -
If the copy-paste functionality is not working in your environment, refer to the instructions file on the VM desktop and use Ctrl+C, Ctrl+V or Command-C,
Command-V.
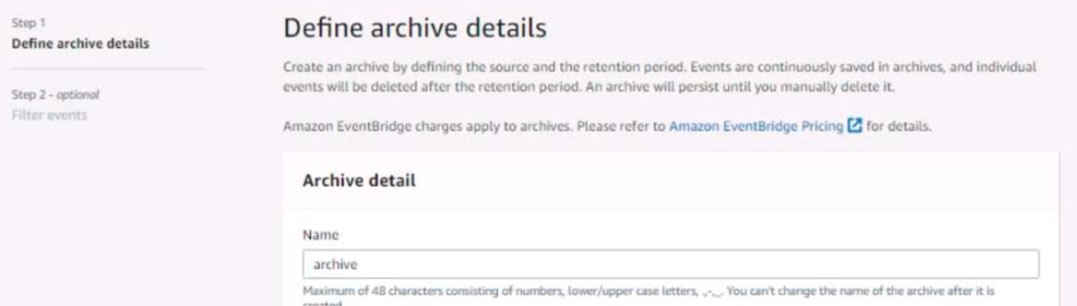
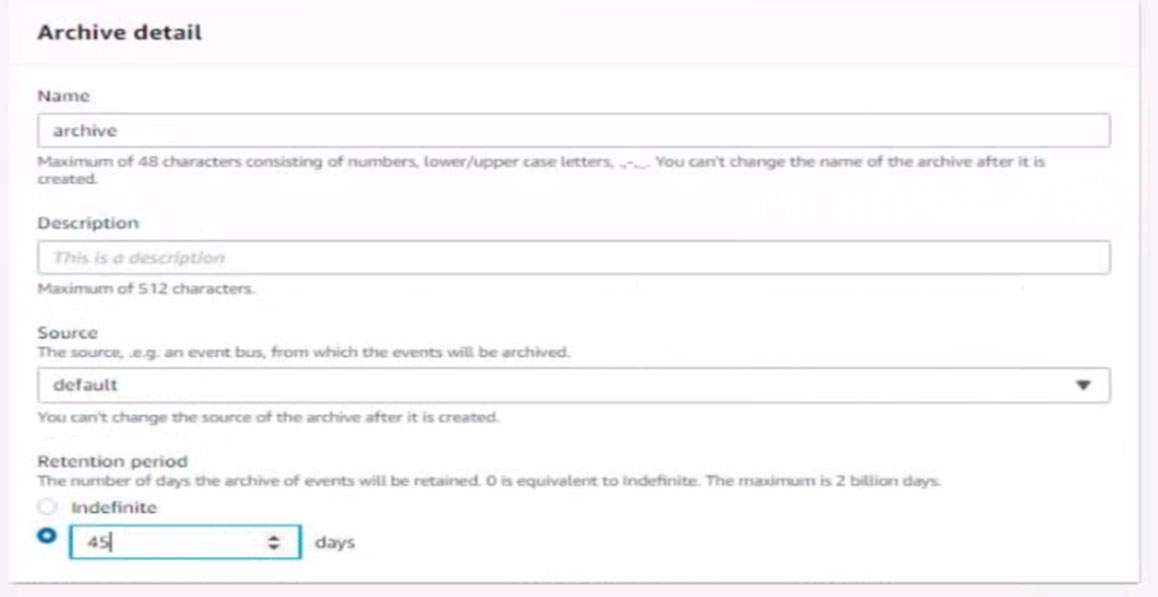
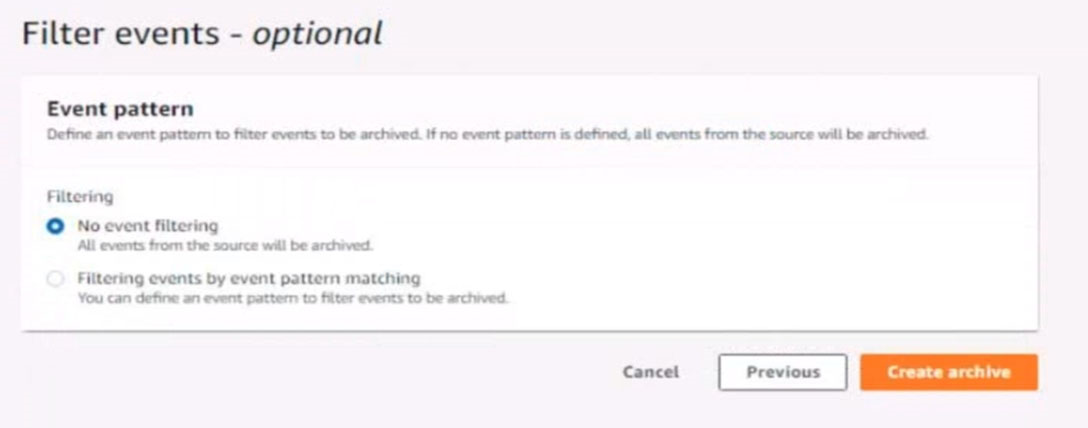
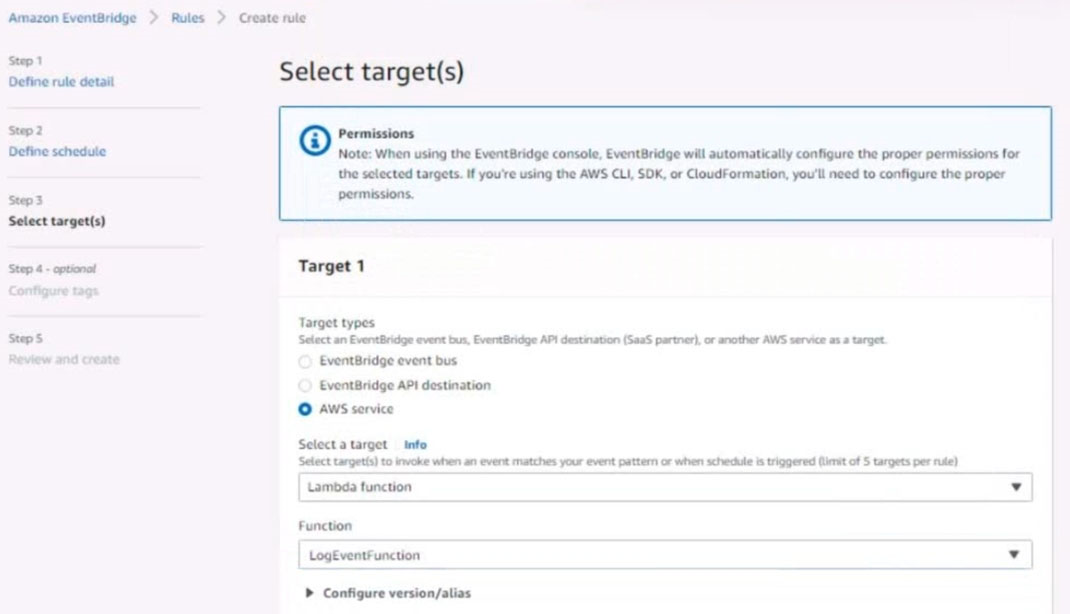
Configure Amazon EventBridge to meet the following requirements.
1. Use the us-east-2 Region for all resources.
2. Unless specified below, use the default configuration settings.
3. Use your own resource naming unless a resource name is specified below.
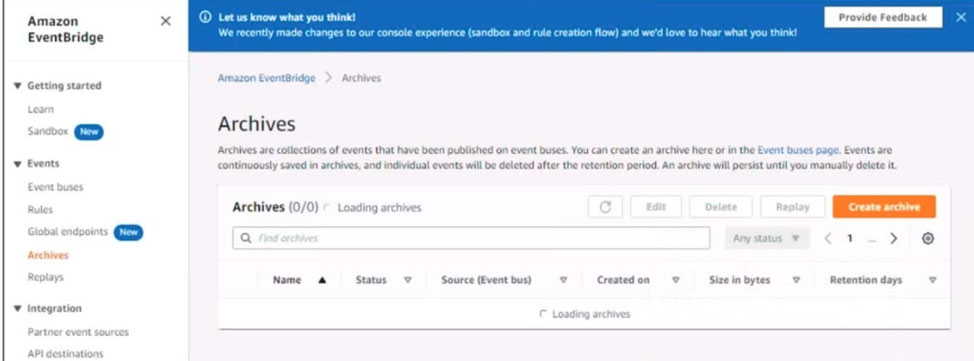
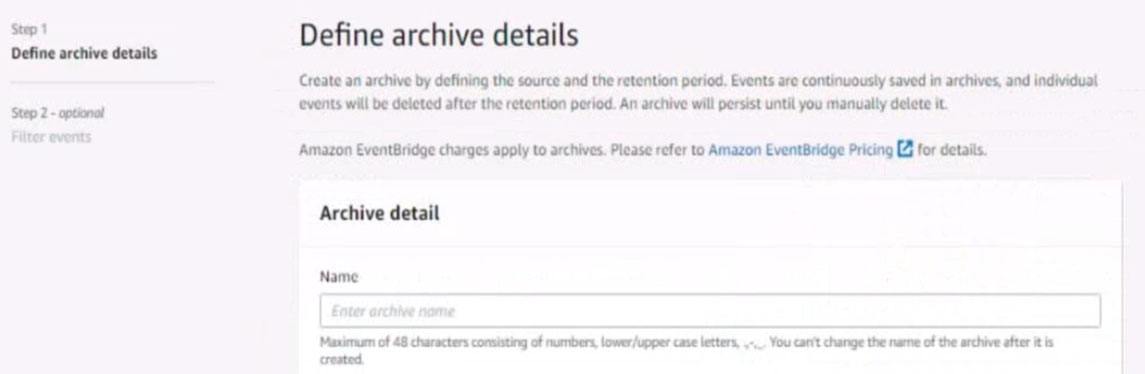
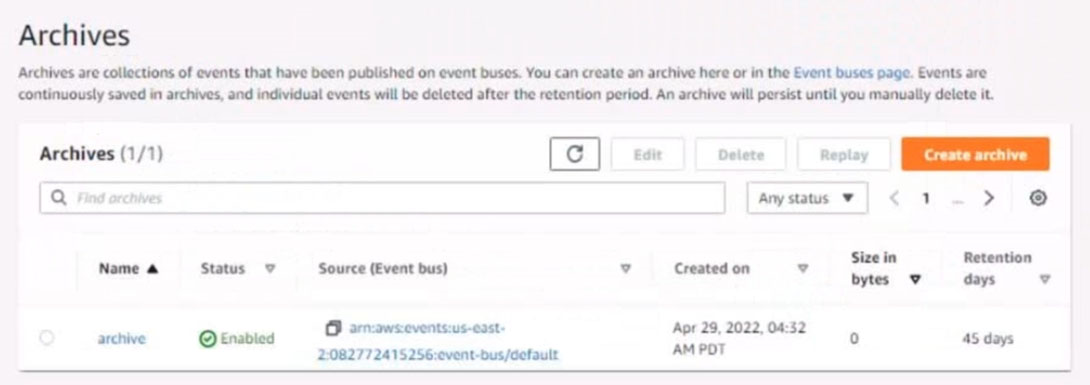
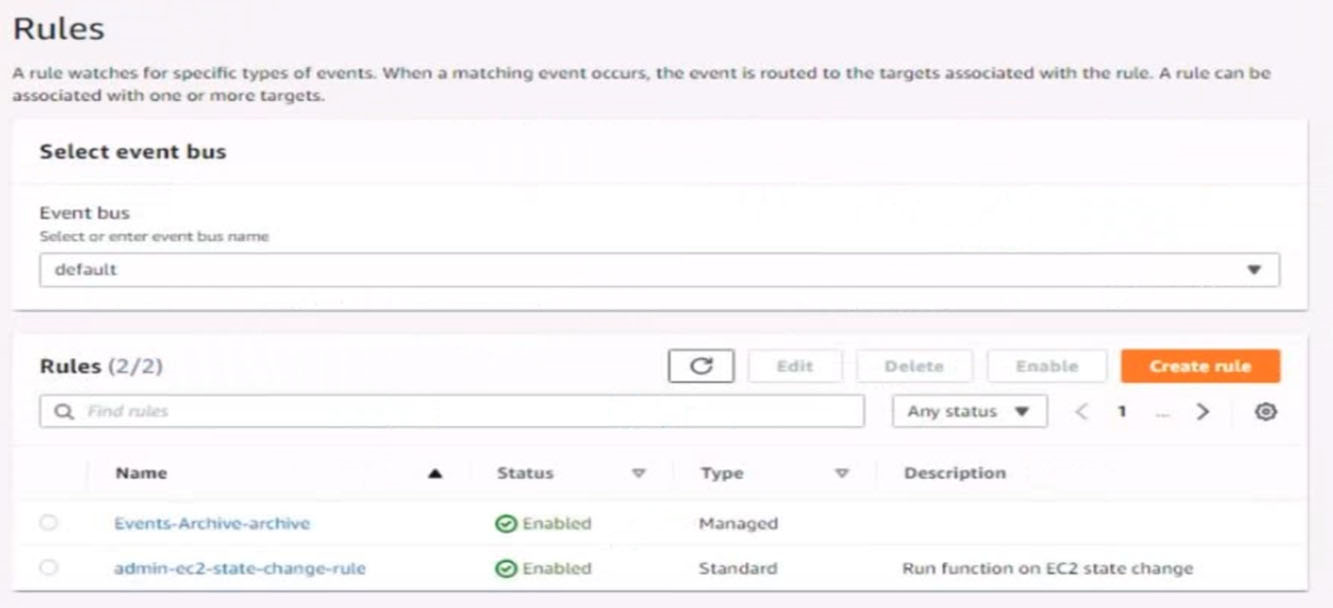
4. Ensure all Amazon EC2 events in the default event bus are replayable for the past 45 days.
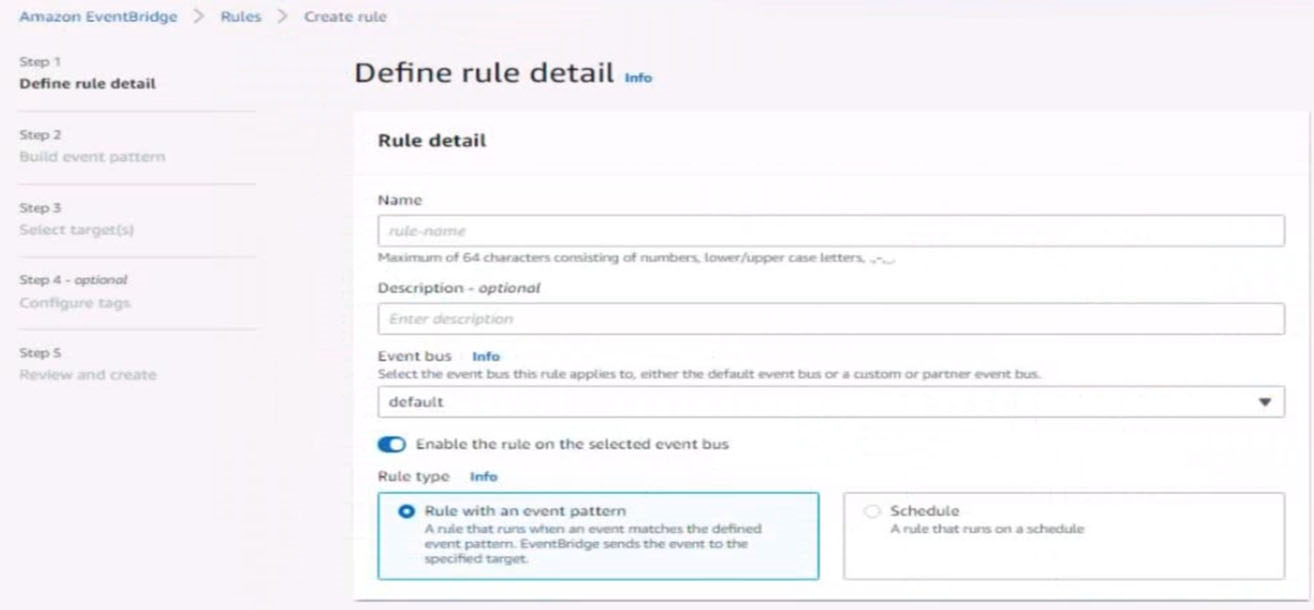
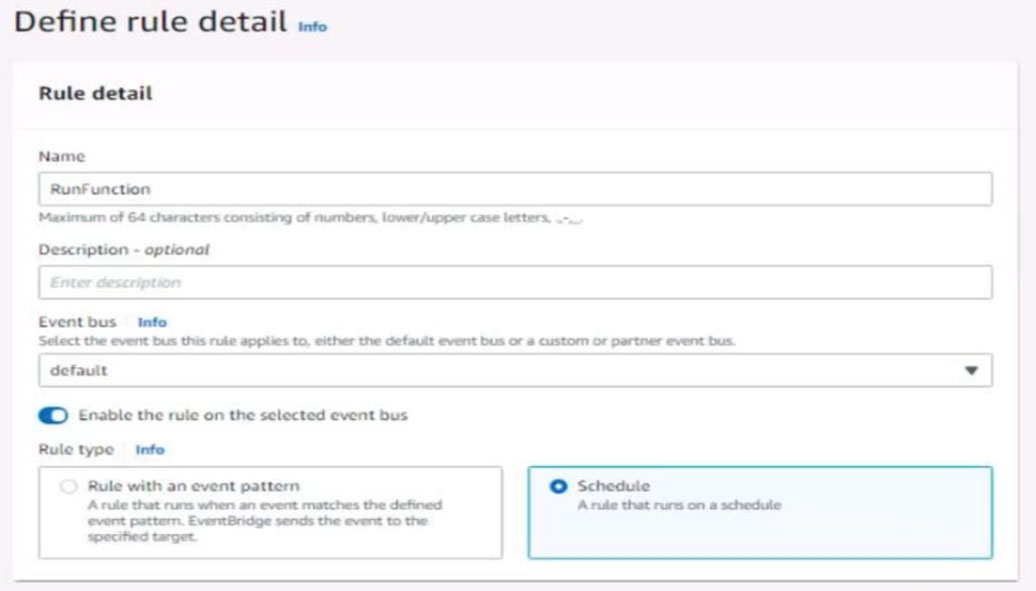
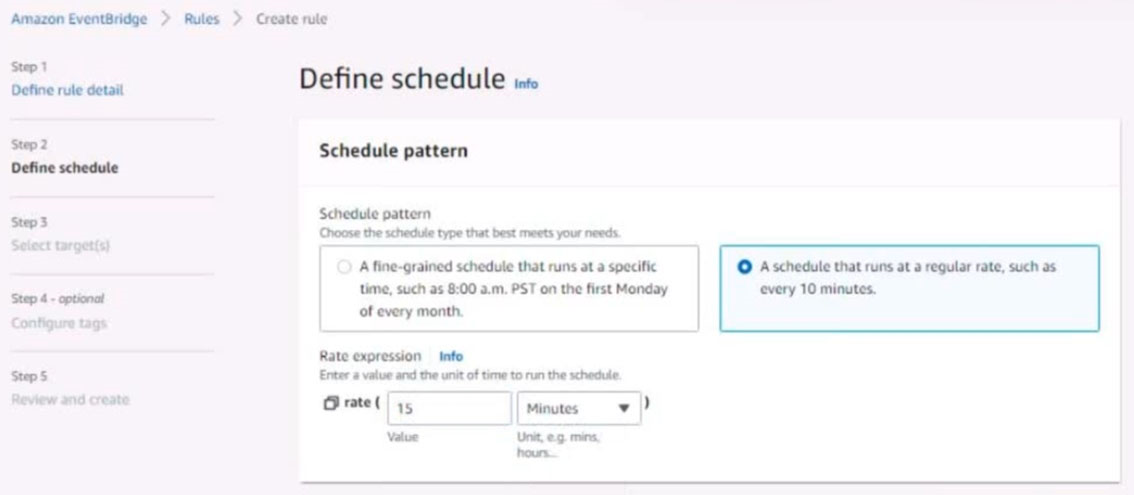
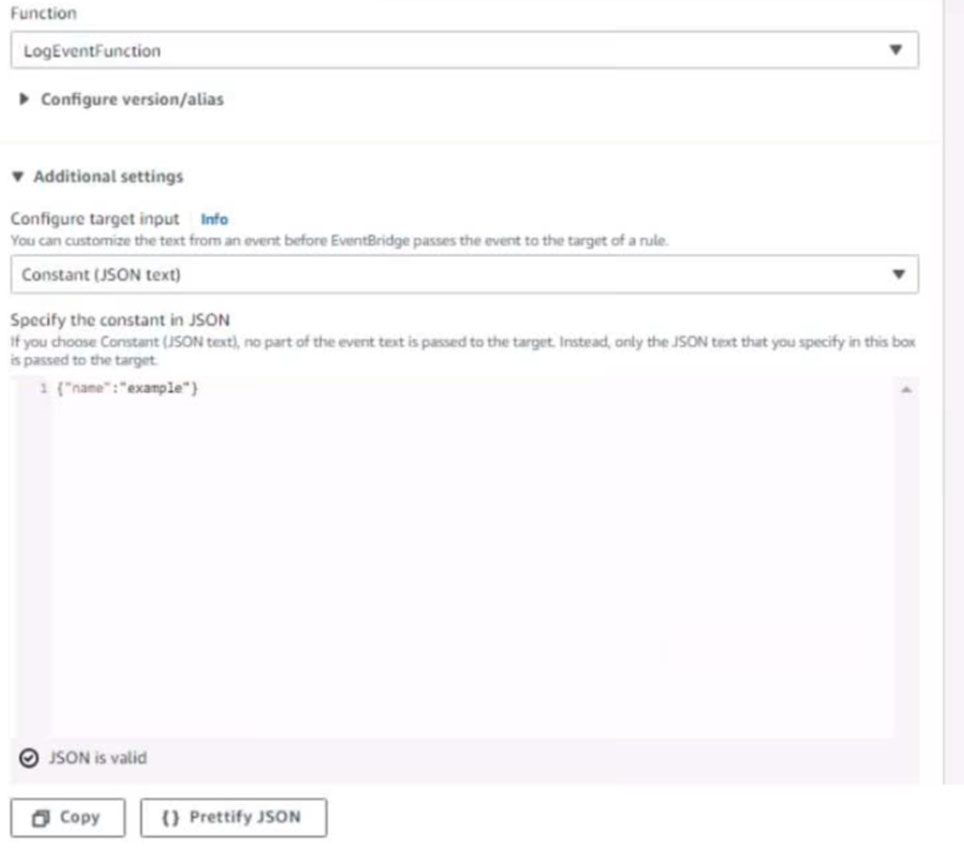
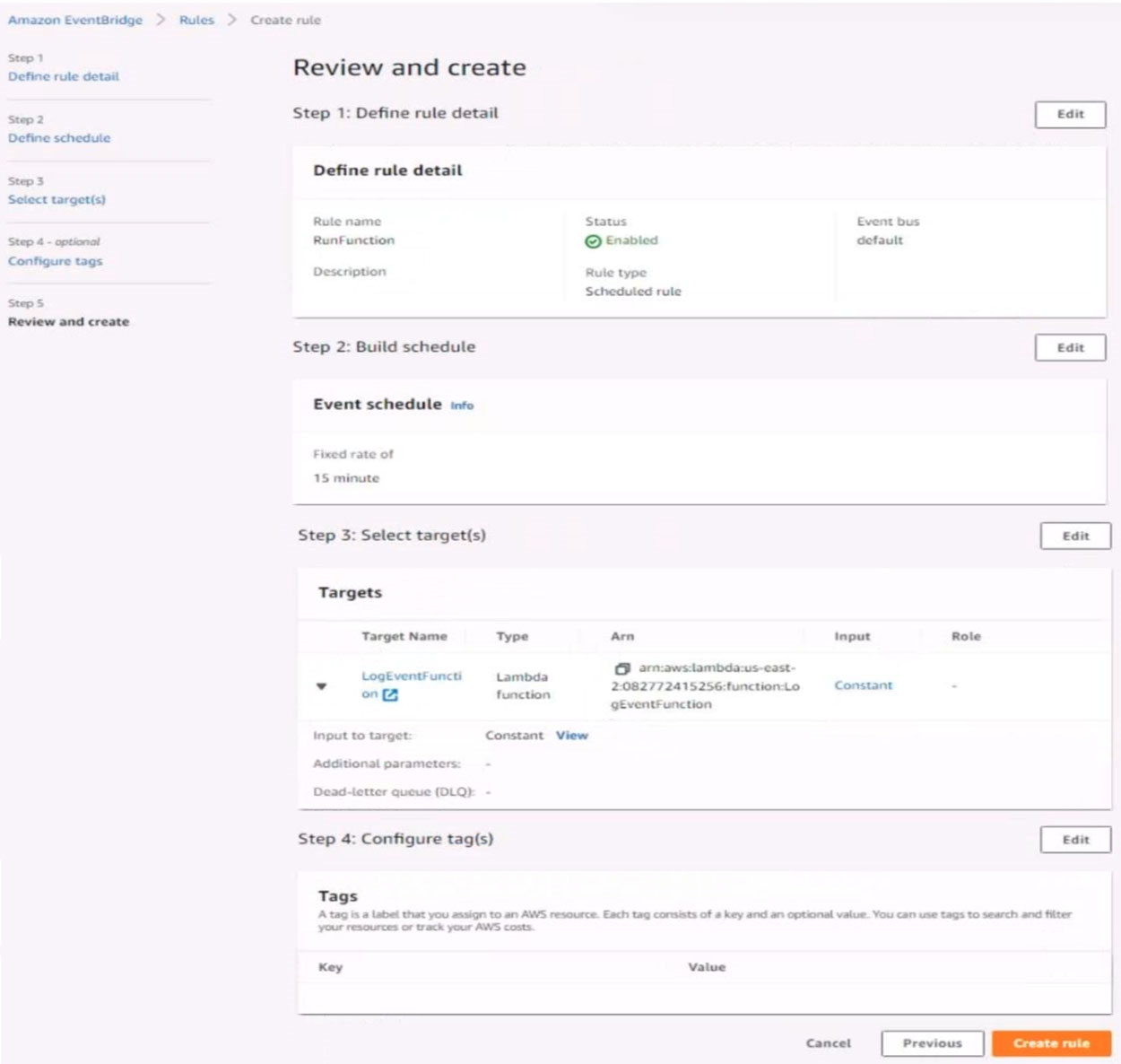
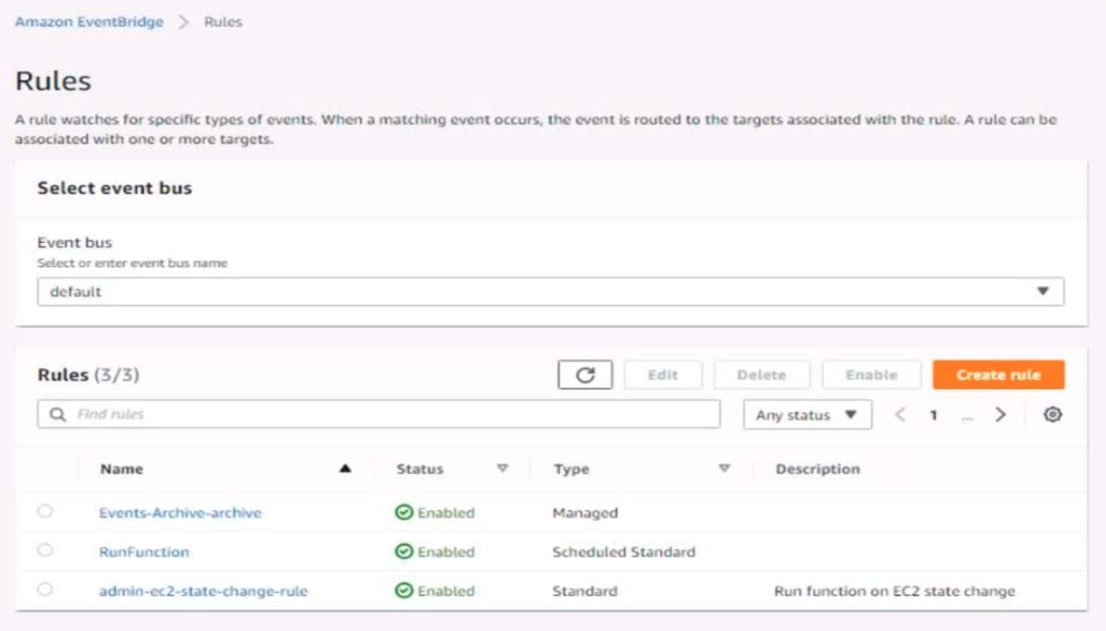
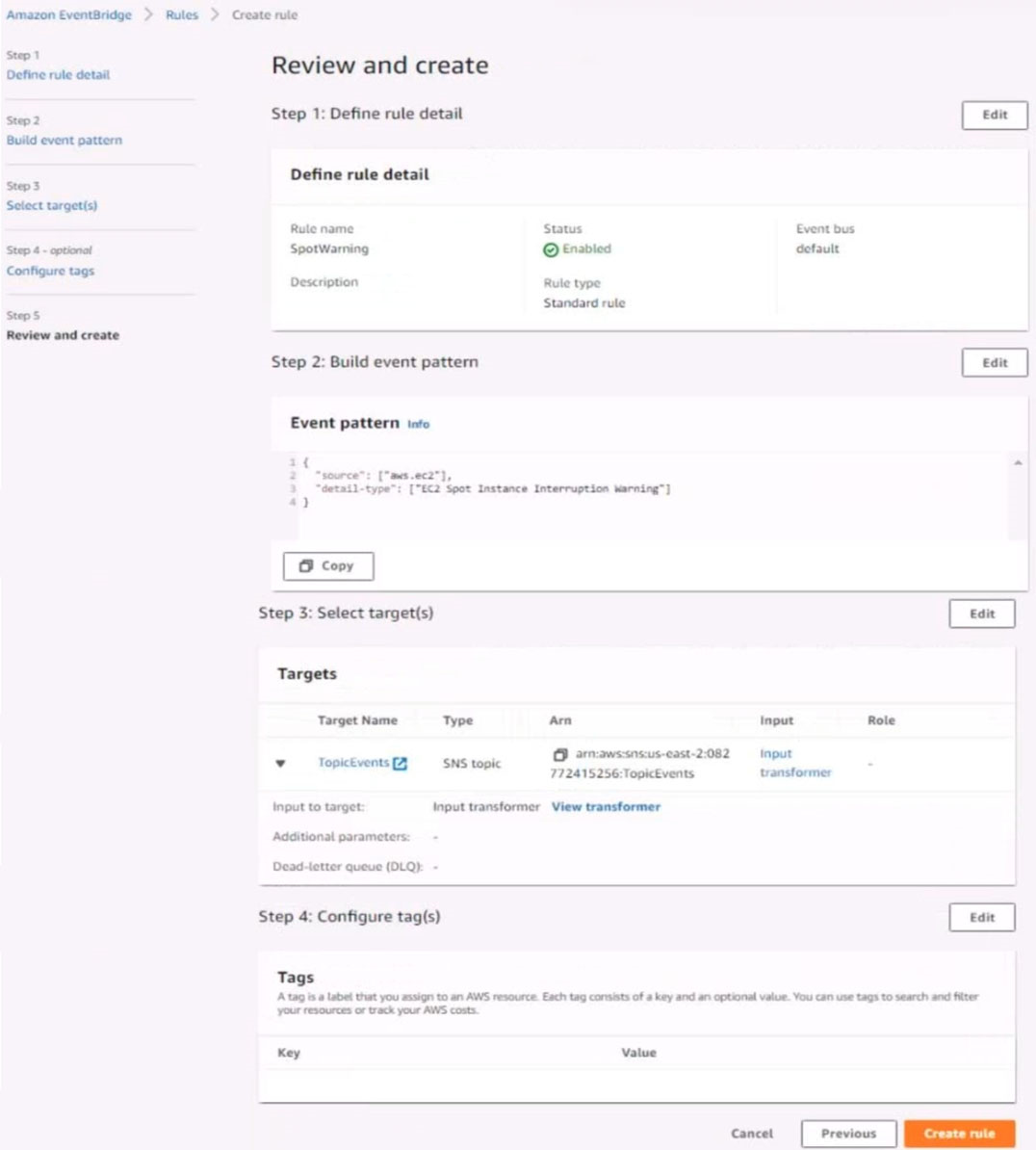
5. Create a rule named RunFunction to send the exact message {"name":"example") every 15 minutes to an existing AWS Lambda function named LogEventFunction
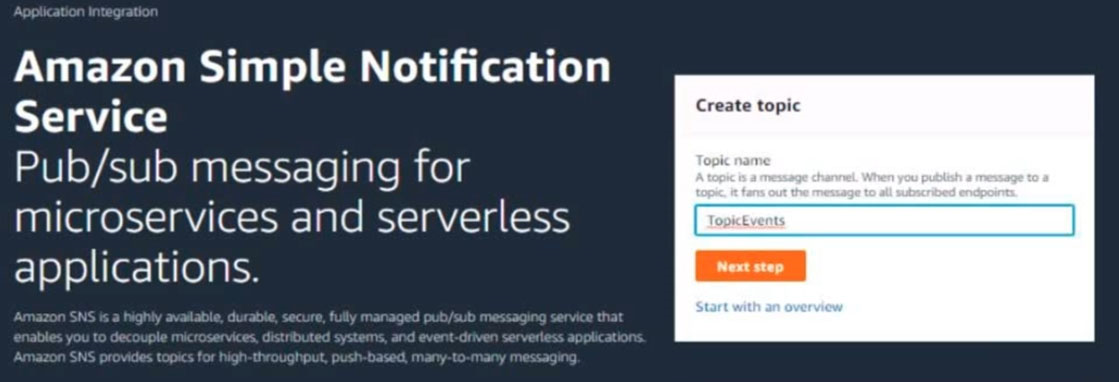
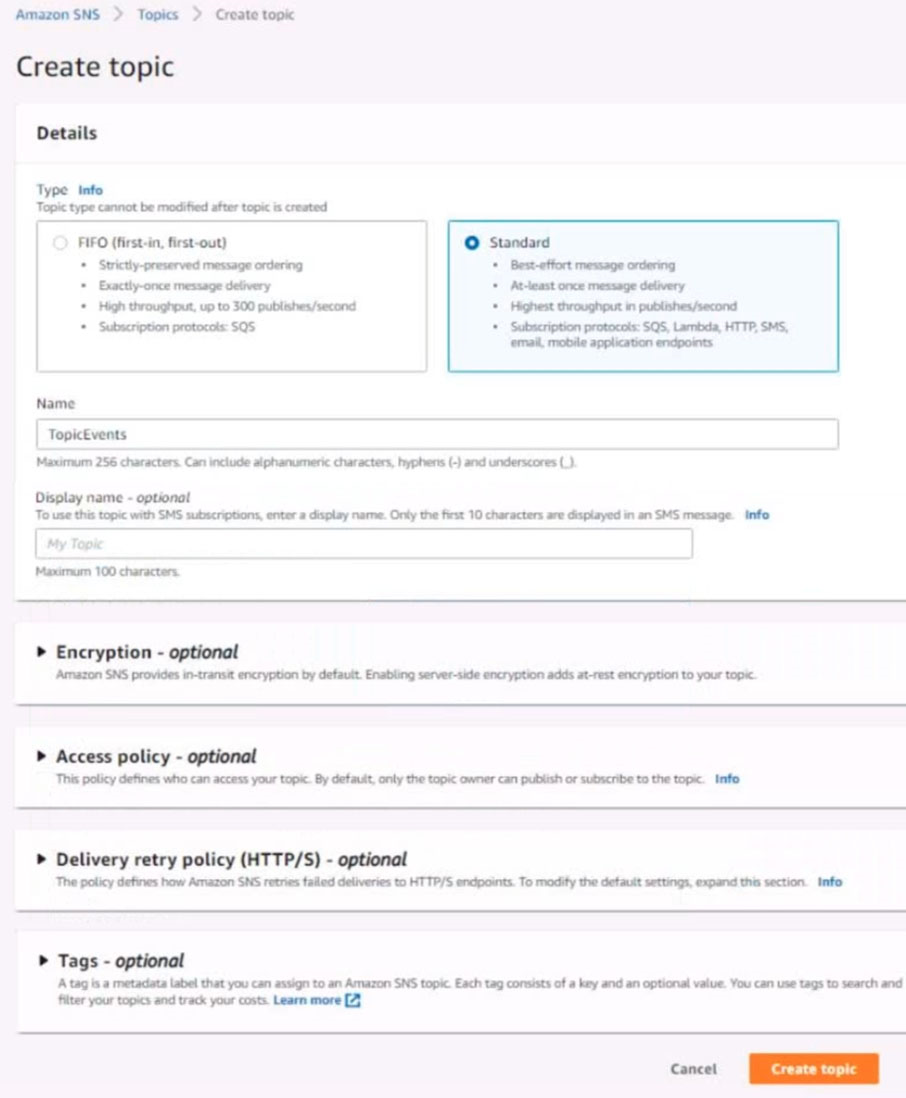
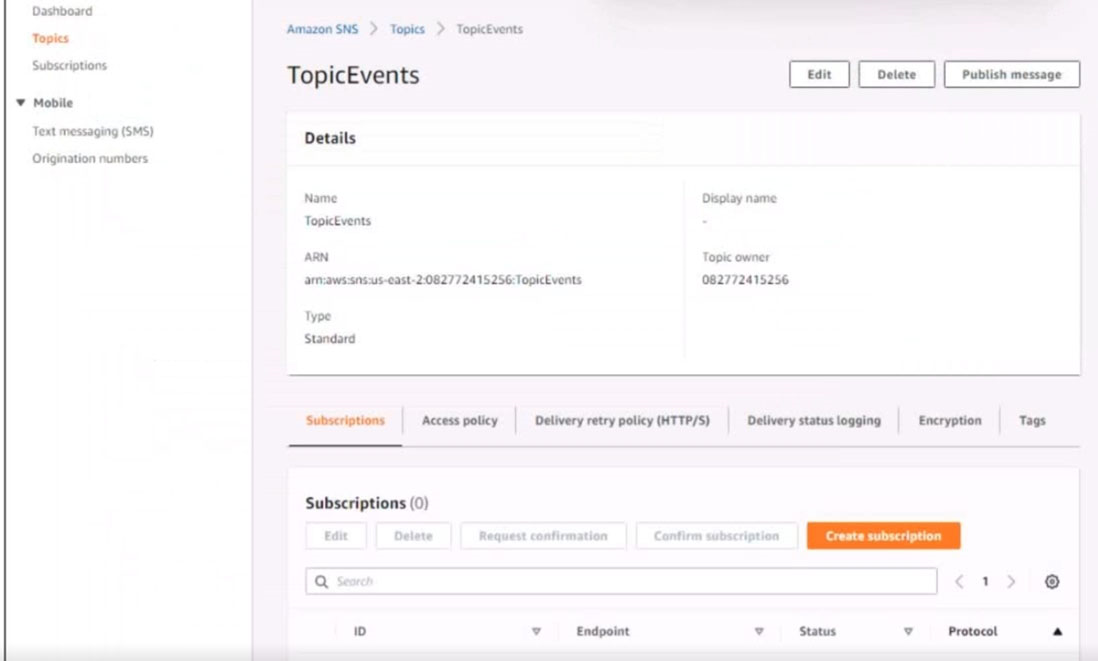
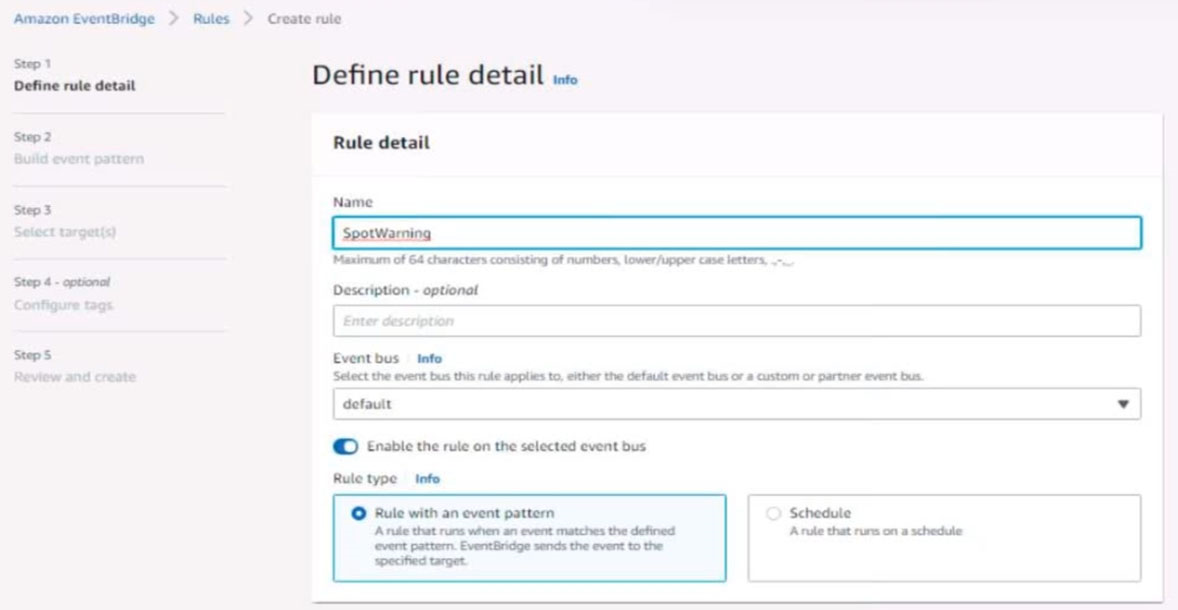
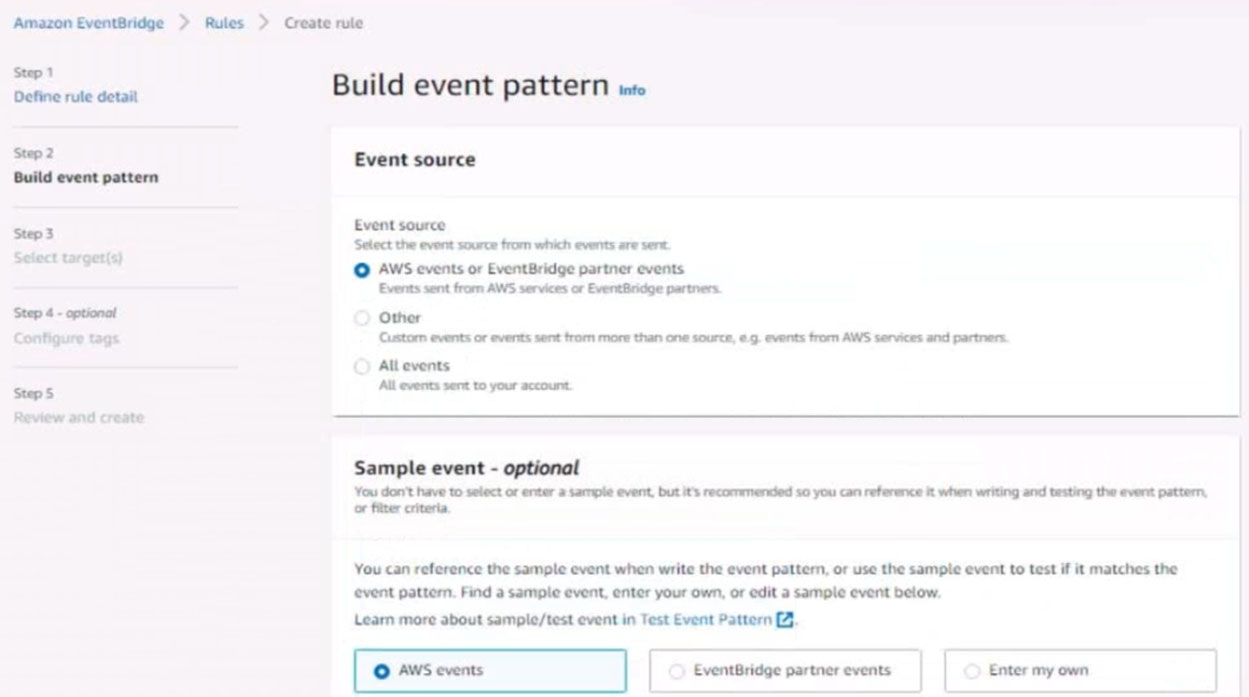
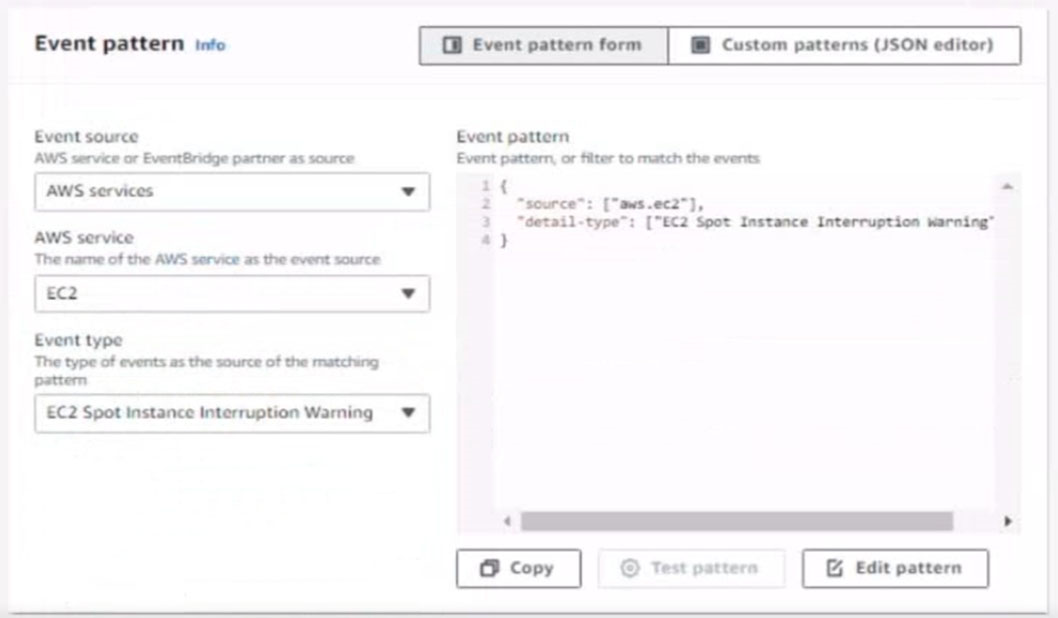
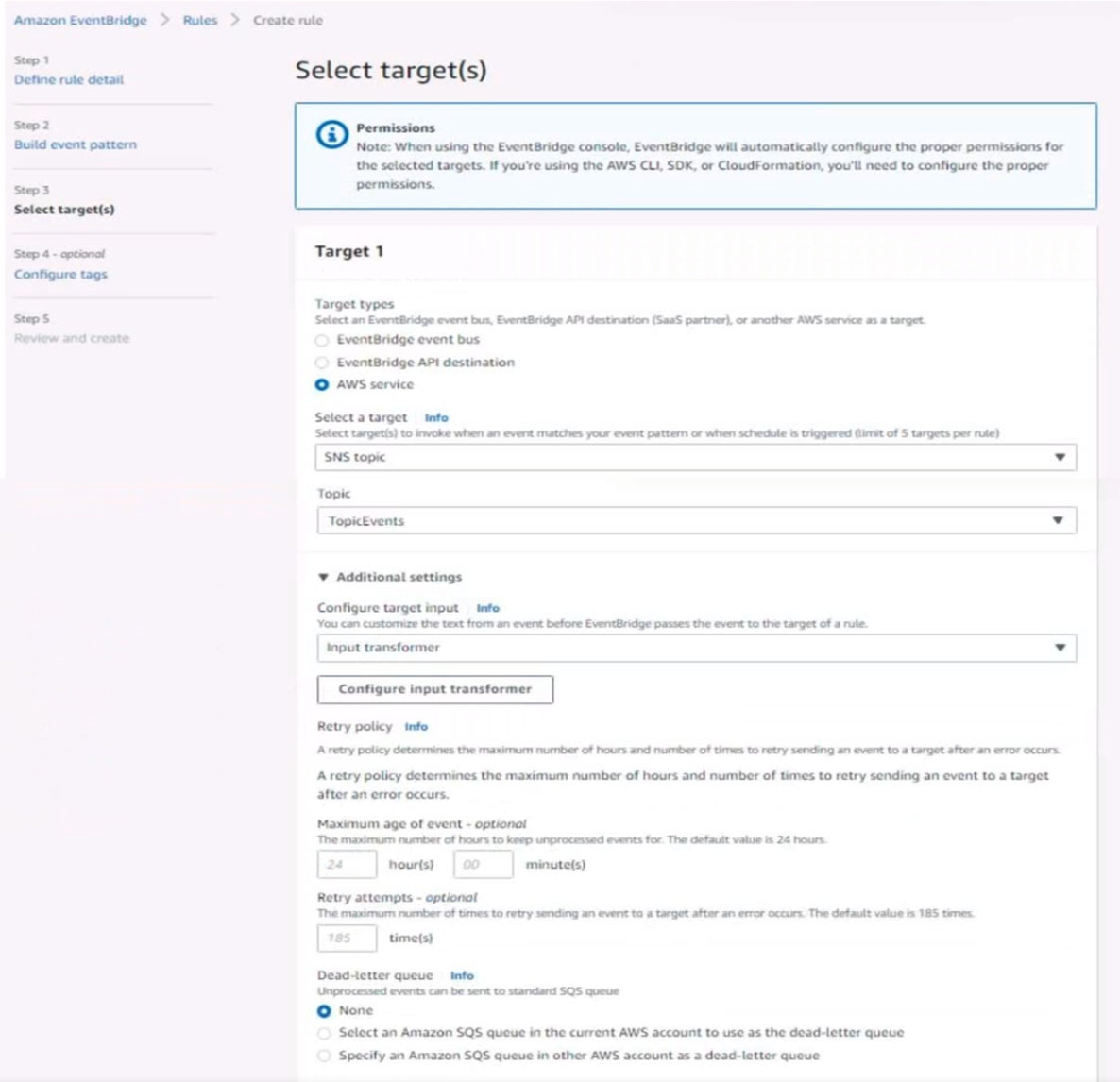
6. Create a rule named SpotWarning to send a notification to a new standard Amazon SNS topic named TopicEvents whenever an Amazon EC2 Spot Instance is interrupted. Do NOT create any topic subscriptions. The notification must match the following structure:
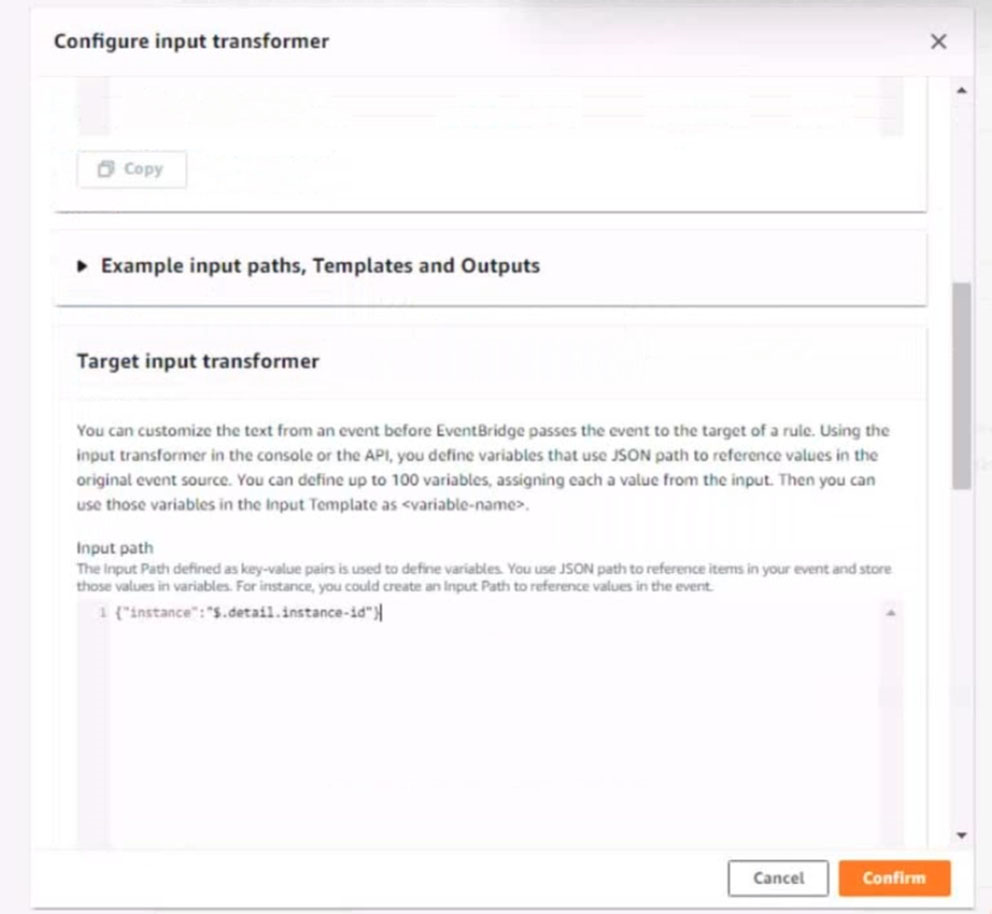
Input path:
{`instance`:`detail.instance-id}
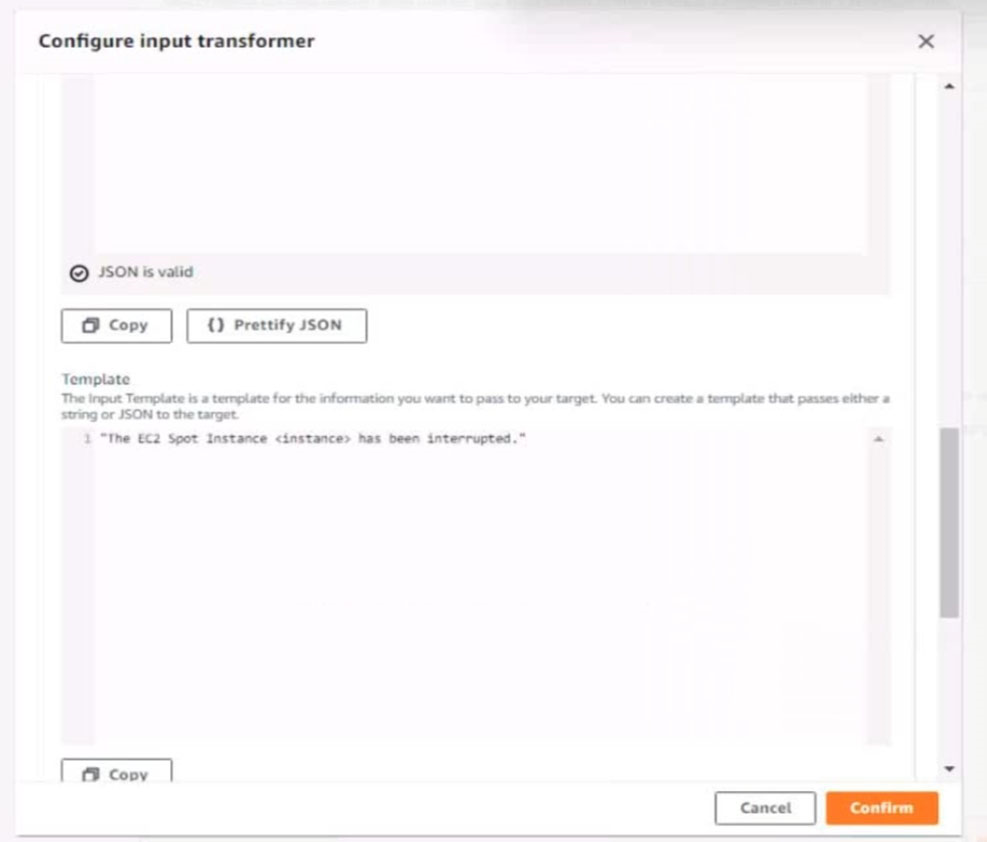
Input template:
`The EC2 Spot Instance <instance> has been interrupted.`
Important: Click the Next button to complete this lab and continue to the next lab. Once you click the Next button, you will NOT be able to return to this lab.
See explanation below.