A company's web application is hosted on Amazon EC2 instances running behind an Application Load Balancer (ALB) in an Auto Scaling group. An AWS WAF web ACL is associated with the ALB. AWS CloudTrail is enabled, and stores logs in Amazon S3 and Amazon CloudWatch Logs.
The Operations team has observed some EC2 instances reboot at random. After rebooting, all access logs on the instances have been deleted. During an investigation, the Operations team found that each reboot happened just after a PHP error occurred on the new-user-creation.php file. The Operations team needs to view log information to determine if the company is being attacked.
Which set of actions will identify the suspect attacker's IP address for future occurrences?
A
A company has hundreds of AWS accounts, and a centralized Amazon S3 bucket used to collect AWS CloudTrail logs for all of these accounts. A Security
Engineer wants to create a solution that will enable the company to run ad hoc queries against its CloudTrail logs dating back 3 years from when the trails were first enabled in the company's AWS account.
How should the company accomplish this with the least amount of administrative overhead?
B
A Security Engineer is troubleshooting a connectivity issue between a web server that is writing log files to the logging server in another VPC. The Engineer has confirmed that a peering relationship exists between the two VPCs. VPC flow logs show that requests sent from the web server are accepted by the logging server, but the web server never receives a reply.
Which of the following actions could fix this issue?
A
Reference:
https://docs.aws.amazon.com/vpc/latest/userguide/VPC_SecurityGroups.html
A Security Engineer accidentally deleted the imported key material in an AWS KMS CMK.
What should the Security Engineer do to restore the deleted key material?
B
Reference:
https://docs.aws.amazon.com/kms/latest/developerguide/importing-keys.html
A company's Security Engineer is copying all application logs to centralized Amazon S3 buckets. Currently, each of the company's application is in its own AWS account, and logs are pushed into S3 buckets associated with each account. The Engineer will deploy an AWS Lambda function into each account that copies the relevant log files to the centralized S3 bucket.
The Security Engineer is unable to access the log files in the centralized S3 bucket. The Engineer's IAM user policy from the centralized account looks like this: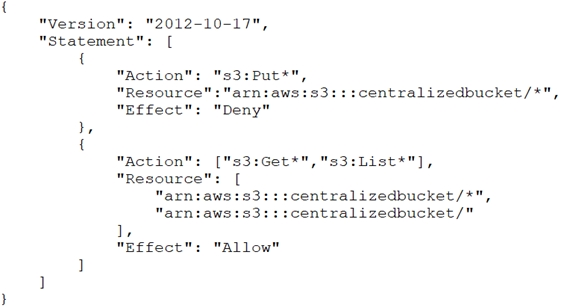
The centralized S3 bucket policy looks like this: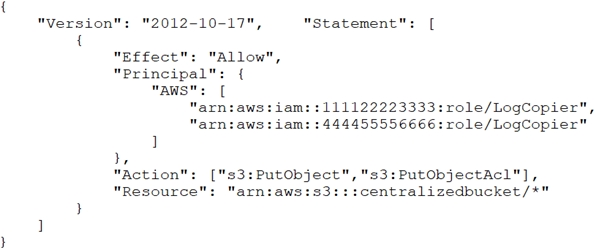
Why is the Security Engineer unable to access the log files?
D
An application running on Amazon EC2 instances generates log files in a folder on a Linux file system. The instances block access to the console and file transfer utilities, such as Secure Copy Protocol (SCP) and Secure File Transfer Protocol (SFTP). The Application Support team wants to automatically monitor the application log files so the team can set up notifications in the future.
A Security Engineer must design a solution that meets the following requirements:
✑ Make the log files available through an AWS managed service.
Allow for automatic monitoring of the logs.
✑ Provide an interface for analyzing logs.
✑ Minimize effort.
Which approach meets these requirements?
B
Reference:
https://docs.aws.amazon.com/systems-manager/latest/userguide/monitoring-cloudwatch-agent.html
A company has multiple AWS accounts that are part of AWS Organizations. The company's Security team wants to ensure that even those Administrators with full access to the company's AWS accounts are unable to access the company's Amazon S3 buckets.
How should this be accomplished?
A
Reference:
https://docs.aws.amazon.com/organizations/latest/userguide/orgs_manage_policies_scps.html
A Security Engineer has several thousand Amazon EC2 instances split across production and development environments. Each instance is tagged with its environment. The Engineer needs to analyze and patch all the development EC2 instances to ensure they are not currently exposed to any common vulnerabilities or exposures (CVEs).
Which combination of steps is the MOST efficient way for the Engineer to meet these requirements? (Choose two.)
CD
A company has decided to use encryption in its AWS account to secure the objects in Amazon S3 using server-side encryption. Object sizes range from 16,000 B to 5 MB. The requirements are as follows:
✑ The key material must be generated and stored in a certified Federal Information Processing Standard (FIPS) 140-2 Level 3 machine.
✑ The key material must be available in multiple Regions.
Which option meets these requirements?
C
An organization has a multi-petabyte workload that it is moving to Amazon S3, but the CISO is concerned about cryptographic wear-out and the blast radius if a key is compromised.
How can the CISO be assured that AWS KMS and Amazon S3 are addressing the concerns? (Choose two.)
CD